|
|
RSS 1.0 RSS 2.0 |
October 27, 2009
10 Tips for Safe Social Networking for Attorneys & Experts
LinkedIn. Facebook. Twitter. Blogs. Bob Ambrogi, always on the forefront of web technologies and their impact, recently published two helpful "Top 10" articles - one each for attorneys and experts, with some great tips for those navigating online communities for networking and socializing.
One such tip is to separate professional and personal contacts into different networks. However, don't fall prey to the myth of anonymity or that restricted social networks will necessarily protect you. It isn't always clear which content is restricted to just your approved network contacts. Others have been known to seek invitations or sign up for accounts solely for getting at the "good stuff". As always, be ever mindful of what you post online.
Not surprisingly, the best and number one tip is to use good old fashioned common sense. However, given some of the gaffes Bob used as examples, it's easy to agree with his observation that it "sometimes seems to be in short supply these days".
Definitely good fodder for any law school ethics curriculum, since these are among the modern day challenges lawyers face while building both their practices and professional reputation online.
April 01, 2009
Twittering Away a Job – Infamously
It's all over Twitter and the web - how a Twitterer made a negative Tweet about her new job offer from Cisco. Naturally, someone who identified himself from Cisco saw it and responded. It's now an urban wegend (web legend), dubbed the "Cisco Fatty" incident, in reference to the "fatty paycheck" comment in her Tweet. There are already YouTube videos parodying and discussing it.
Covered in a DailyTech article, the Twitterer identified as Connor Riley explained her situation and intent in why she turned down the job and sarcastically tweeted about it to her friends. But she didn't protect the tweet from others seeing it. She even authored a thoughtful blog post to explain, apologize, and add her thoughts on the subject of social media. But really, the damage is done to her professional and personal reputation. Not exactly how one wants to gain their 15 minutes of fame in transitioning from college into the workforce. The Chicago Tribune also ran an article, "'Cisco Fatty' incident provides cautionary tale to those who tweet about work".
The moral of the story: Think before you tweet.
March 11, 2009
Multi-Pass Erasure Myth Debunked
In his latest LTN column, Ball in Your Court, Craig Ball debunks the long-held hard drive multi-pass erasure myth, that goes like this:
"Top notch computer forensic examiners have special tools and techniques enabling them to recover overwritten data from a wiped hard drive so long as the drive was wiped less than 3 or 7 or 35 times." The myth also goes that someone using a magnetic force electron microscope would be able to discern the trace magnetic signal left behind on a drive that wasn't wiped enough times, and somehow piece together the underlying wiped data. Which is a leading reason why common file and disk wiping tools have included all kinds of multi-pass wiping options, ranging from the DOD-specified wipes to the massive 35 times Gutmann wipe.
One part of the myth also says that one can recover trace magnetic data from the spaces between the tracks as the drive heads don't track exactly the same on each pass when writing data. (Think of this as the space between the grooves on a vinyl record, for those of us who fondly remember them.)
To which Craig says, "Nonsense!" and "[i]t's all a lot of hogwash, at least with respect to any drive made this century." He explains how the vastly increased "areal density" of modern hard drives leaves little room for wiped data to be resurrected, even if it's only wiped with a single pass. Areal density simply refers to how closely packed together all the data bits are, which allows manufacturers to place hundreds of GB on a single hard drive platter these days.
Like him, I've heard the myth for years and questioned the ability to use a magnetic force electron microscope to resurrect wiped data. First, it would be incredibly expensive to do (but that factor only makes it impracticable). So it was interesting to hear the results, as Craig related from several professionals performing such an experiment, was that it was less successful than a simple coin toss.
Thus he concludes:
"You only need one complete pass to eviscerate the data (unless your work requires slavish compliance with obsolete parts of Department of Defense Directive 5220.22-M and you make two more passes for good measure).
No tool and no technique extant today can recover overwritten data on 21st century hard drives. Nada. Zip. Zilch."
While fascinating from a technical perspective, the real take-away from Craig's article is the reminder that:
"The most egregious is the assumption that formatting a hard drive is the same as wiping its contents. In fact, formatting obliterates almost none of a drive's contents. Any eBay purchaser of a formatted drive can easily restore its contents."
If only I had a Google share for every time I advised someone about this danger and resulting risk. If you are disposing of a hard drive or giving it to someone else to use, use a proper drive wiping tool first, not a simple format command.
Another good take-away is Craig's discussion of the "G List" sectors on a hard drive, and why conventional wiping cannot touch that data. So what are those?
In essence, modern hard drives have the ability to sense when a sector is going bad (i.e., not able to store information reliably). When that is detected, the hard drive automatically copies the contents of the ailing sector to another unused sector on the hard drive, and remaps (points) to its new location on the drive. This map is kept in the G List on the drive, which stands for Growth List or Growing Defect List. This is a good thing so you don't lose data to bad spots on the hard drive. However, when you use wiping software to wipe the drive's data, it can only wipe data in the accessible areas of the drive (which include the second copies of the bad sectors). However, the original "bad" sectors cannot be wiped by conventional software as they are not accessible to it.
But as Craig points out, for the industrious there's a cure for that as well:
"Remarkably, nearly all hard drives manufactured after 2001 incorporate the ability to rapidly and securely self-erase everything, including the G List; but, drive and computer manufacturers are so petrified you'll mess that up, they don't offer an easy way to initiate a self-destruct sequence.
For those at ease with command line interfaces, the Secure Erase commands can be run using free tools developed for the NSA and available at http://tinyurl.com/serase. But be careful with these as there's no road back."
It's a good read for anyone curious (and paranoid) about securely deleting data.
December 19, 2008
Apply a Critical Security Patch for IE 5, 6, 7 & 8 ASAP
As if "Clickjacking" wasn't bad enough, yet another critical security exploit was found in IE, and it affects virtually every version that people would have on their PCs (from the older v. 5.0 all the way through to IE's 8 beta). This flaw was recently publicly reported, and Microsoft just released the critical patch yesterday, Dec. 18th. Since it's very rare when Microsoft issues a security patch out of their normal cycle, you can tell this one is important. Without going into techie details, suffice it to say that thousands of web sites have already been compromised to deliver the exploit to your PC should you visit them using an unpatched version of IE. The exploit could allow criminals to take control of people's computers and steal their passwords. The problem was that hackers found this security hole before Microsoft, so MS had to play catch-up.
For personal PCs, download and install this patch from Microsoft. It should also be available in your Windows Update (remember to log in as an administrator first). If you're in an enterprise environment, check with your IT department as they are very likely already painfully aware of this and are probably working on it.
I read through the Microsoft-suggested workarounds in lieu of applying the patch, and none are pretty. For instance, setting your IE's security level to "High", while effective, disables ActiveX and scripting, and would disable a number of features on legitimate sites. Plus, you'll likely get nagged to death from prompt after endless prompt while surfing.
Of course, the best suggestion is to not use IE at all, and instead use an alternate browser such as Firefox, Opera, or Chrome. However, even if you don't use IE overtly, you could still be at risk. For example, some people use a Firefox plugin or extension to have an IE tab open within Firefox -- useful when a specific site just won't work properly in Firefox. Guess what? It's as if you're using IE to visit that site, and so you're vulnerable if the new IE patch isn't installed. Also, remember that IE's core components are used in a number of non-web browsing functions, so you may be vulnerable even if you're not using IE as your default browser.
Some experts suggest that eventually hackers will find a way to use this exploit in a slightly different manner than what the MS patch was designed to fix. But for now, I'd say your best bet is to apply this IE patch, and set and use Firefox or another non-IE browser as your default browser in Windows.
December 13, 2008
Norton Internet Security 2009 -- What A Difference!
I recently upgraded my personal laptop to Norton Internet Security 2009, and was very pleasantly surprised. In stark contrast to prior versions, the new 2009 version has been streamlined and so far seems very light on system resources. In recent years, Symantec has needed to rebuild both its brand and its products, mainly due to the horribly bloated and CPU-intensive 2005 and 2006 versions of their Norton Internet Security (NIS) and Norton Antivirus (NAV) programs, which prompted many customers to post negative feedback online.
Starting with the 2007 version, Symantec recoded these products from the ground up in an effort to make them lighter on system resources. It was a partial success. While it was a good restart for the Norton line, I still saw my system take a noticeable performance hit during the Live Updates, with a lot of disk thrashing as it processed the chunkier updates. When it wasn't updating, though, it was mostly transparent. The main problem was that it always wanted to update shortly after I logged into Windows, which I found quite interruptive and annoying. I could've turned off the automatic updates, but I tend to forget to turn them back on, and my protection would become outdated.
Well, no more. The folks at Symantec have finally gotten the message, loud and clear. NIS 2009 has several new features designed to significantly lighten the load on your PC. In fact, Symantec went out their way to not only make it faster, but to show you as well (can you say, "win back customers"?). In addition to several key performance enhancements, NIS 2009 includes two CPU meters on its main screen and other visual cues and logs to show how much lighter it is on your system resources. The user interface was also streamlined to present users with cleaner status view:

Also new is "full screen detection", which temporarily disables non-essential alerts, updates, and scans while you're running a program in full screen mode, such as while watching a movie or playing a game. Rest assured, the auto-protection feature smartly provides continuous protection while in this "silent" mode. Norton Insight is a new feature which speeds system scanning by identifying files that don't have to be scanned again. It checks your program and system files against a database of trusted programs and displays a large meter showing how many it can skip next time to save you a lot of time. I'm hoping that it also tracks each file's checksum or hash as it's not uncommon for malware to replace system or program files with its own tainted versions.
For further explanation of all the new features and performance enhancements, I'll direct you to the following review and online resource guide which provide more depth:
- PC Magazine Review and Editors' Choice
- How To Master New Norton Internet Security 2009 -- Guides and Tutorials
The only downside -- and it's a big annoying one for me -- is that in NIS 2009, Symantec disabled all standard user accounts from being able to change its settings by entering the administrator password. Remember, even if it's your own personal laptop, it's more secure to run programs and access the Internet using Windows accounts without administrator privileges. So I mainly run as a standard user in Vista and only log in as the administrator when needed. However, prior versions of NIS would allow me, as a standard user, to enter the administrator password in NIS when I needed to temporarily disable the firewall or antivirus for troubleshooting, or when a blocked program needed temporary Internet access.
With NIS 2009, I either have to log off or switch users to the admin account in Windows to do this, which is time-consuming and a royal pain. When I inquired about this, Symantec's tech support responded the product team changed this behavior to make it more secure in case users discovered the admin password. Unfortunately, this is faulty logic as users could do a lot more in that situation. I logically suggested that Symantec provide a program update which retains this as the default behavior for maximum security, but which simply adds a configuration setting in which the administrator can re-enable the option to accept the admin password from standard users. In other words, give the customer the choice! Don't just take it away in the name of security.
Last but not least, since the Norton products are now subscription-based: If you have a current subscription for a previous version of NIS or NAV, you should be able to upgrade for FREE to the 2009 versions as I did, and your remaining subscription period carries over. Just remember you need to uninstall any older version first so they don't conflict. I also recommend storing your Norton product activation code in your online Norton account -- it just makes reactivation easier.
It also appears Symantec's tech support has improved over the past year or two. I used both the built-in chat feature as well as the telephone option and both went very well with only a minor wait. While no security suite is perfect (many reviewers report the spam module is still subpar), I'd say that Norton Internet Security 2009 is a welcome advance and it's good to see Symantec getting back in touch with the needs of its customer base.
November 29, 2008
Wireless WPA Encryption Component Hacked -- How to Protect Yourself
Beware, security researchers have discovered a way to do a partial hack of some wireless networks using WPA (Wi-Fi Protected Access). WPA is used by many to encrypt and secure their wireless networks. I first read about this announcement a few weeks ago, and preferred to wait until after the findings were published for confirmation. ARS Technica has an excellent and balanced article, "Battered, But Not Broken: Understanding the WPA Crack", describing the hack, and the researchers published their paper online.
There's a lot of FUD (Fear, Uncertainty & Doubt) floating around on this, so I decided to add my perspective and tips for legal professionals. The sky isn't falling. It's important to understand that WPA itself hasn't been cracked, just one of the algorithms used with it, known as TKIP (Temporal Key Integrity Protocol). If you're using AES (Advanced Encryption Standard) encryption with WPA, you're still safe. If you're still using WPA with TKIP, you just need to make a simple change in your wireless router and any wireless device that connects to it, such as your laptop. I've posted an example below on how to change the settings in a Linksys router.
Basically, if you have your wireless router configured to use WPA with TKIP, your wireless network is now vulnerable over that connection. One of the researchers, Erik Tews, stated that for routers using WPA with TKIP, he can access and manipulate the network traffic being sent from your wireless router. While they're not yet able to break the TKIP keys, it's still serious. Supposedly, the traffic sent from your PC back to the router is still safe, but now it's probably only a matter of time before that gets compromised as well.
What Should You Do?
I'll try to keep the jargon to a minimum, but need to mention a few acronyms throughout because that's what you'll see in your router and laptop options. Keep these guidelines in mind:
- First, using any encrypted network is better than a non-encrypted network, even if it only stops the casual or amateur snoops in the area.
- Use a long and strong passphrase for your encryption key -- at least 20 characters with a mix of upper- and lower-case letters, numbers, and symbols.
- Keep in mind that cheap and home-made wireless antennas can access your wireless signal even a mile away.
- Never, ever use WEP (Wired Equivalent Privacy) if you have a better choice -- WEP has been cracked for years now and is considered very insecure.
- WPA (think of it as WPA1) and
- WPA2, which is more secure than WPA.

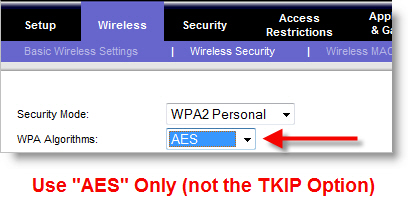
AES encryption is used by the U.S. government, as it's considered much more difficult to crack. If your wireless router doesn't support WPA2 (i.e., doesn't have it listed), then you probably need a firmware update from the manufacturer, which you can usually download from their web site. If your router is too old that it doesn't have WPA2 and there isn't a firmware upgrade for it, then it's probably time to buy a new router. I'd suggest buying one of the new "n" routers for better speed and coverage, as new laptops have been coming out with "n"-capable wireless cards for well over a year. While "g" routers are still very usable, 802.11n is the platform to use going forward if you need to upgrade.
Also, you may need to configure all of your wireless network devices (PC's, wireless printers, BlackBerries, etc.) to use WPA2 if available in their setup options. Windows Vista supports WPA2 out of the box, whereas you'll likely need a patch for Windows XP (see the end of this post for details). I've found my new HP wireless printer and BlackBerry Curve also both support WPA2. If you have some devices or PCs that cannot use WPA2, then you'll need to use WPA for all of them, including your wireless router.
Why Some Sources Reported WPA Was Hacked
It's a matter of semantics. In many wireless routers, WPA comes with two types of encryption algorithms, TKIP and AES. It's important to know that TKIP was only intended as an interim industry solution until they could come up with something better (AES encryption). I explained this back in 2004, when I published my "Wireless Networking Best Practices: Version 2.0" on this blog:
Due to the relative ease in which WEP (Wired Equivalent Privacy) is cracked, WPA (Wi-Fi Protected Access) is vastly preferred. For home use, most people will want to enable WPA Pre-shared Key (WPA-PSK) and use a long key name with a mix of upper and lower case letters, numbers, and odd characters (such as ~!@#$%^&*).That advice still holds true today, just with the added suggestion to use the newer WPA2 if available to provide more security, and practically, to buy you more time as less secure options continue to be hacked. Consider that it's taken a number of years for researchers to find a crack in WPA-TKIP's armor. Like WEP, don't use WPA with TKIP if you have a better option. Keep in mind that home users will likely want to select the WPA2 Personal (aka "WPA2-PSK" or "WPA2 Pre-shared Key") option, while enterprises will use simply "WPA2". The main difference is that the "Personal" or "Pre-shared Key" options require you to enter the passphrase (the pre-shared key) into each device that needs to connect to your wireless network.For the WPA Algorithm, at a minimum choose TKIP (Temporal Key Integrity Protocol). Better yet, use AES (Advanced Encryption Standard) if your router, Wi-Fi card, and software support it. TKIP is an interim industry solution, but it adds the ability to automatically generate new keys at preset intervals. (...) Again, AES is the stronger encryption method that the wireless networking industry is moving toward. If you have it, use it. (emphasis added)
Adding Some Perspective
Again, keep in mind the sky is not falling. While serious, this is a limited hack. It's far better to use some level of encryption than nothing, since the latter leaves your wireless network wide open. Use the most secure option available to you. If you do any work from home, I'm sure your employer will appreciate it as well.
Consider this from the ARS Technica article:
Don't hyperventilate yet; you're (mostly) safeWith all that said, if you have the option of using AES instead of TKIP, use AES. If nothing else, you'll sleep better knowing you're using the most secure encryption currently available.
Now let's back up a little. The early coverage of this crack indicated that TKIP keys were broken. They are not. "We only have a single keystream; we do not recover the keys used for encryption in generating the keystream," Tews said.To describe the attack succinctly, it's a method of decrypting and arbitrarily and successfully re-encrypting and re-injecting short packets on networks that have devices using TKIP. That's a very critical distinction; this is a serious attack, and the first real flaw in TKIP that's been found and exploited. But it's still a subset of a true key crack.
Tews pointed out that "if you used security features just for preventing other people from using your bandwidth, you are perfectly safe," which is the case for most home users. Someone can't use this attack to break into a home or corporate network, nor decipher all the data that passes.
[...]
So WPA isn't broken, it turns out, and TKIP remains mostly intact. But this exploit based on integrity and checksums should argue for a fast migration to AES-only WiFi networks for businesses who want to keep themselves secure against further research in this area-research already planned by Tews and Beck. And now that these two have opened the door, WPA will certainly become subject to even closer scrutiny by thousands of others interested in this space: black-, gray-, and white-hatted.
For those of you still running Windows XP: You might not see the option for WPA2 in your wireless client settings. A while back, Microsoft released a patch to add the WPA2 protocol to XP's wireless settings. Please note this patch is only for 32-bit versions of XP running SP2 (Service Pack 2). While I've successfully installed this patch on several PCs, I always recommend performing a full backup of your system using a drive imaging tool such as Norton Ghost. I also recommend creating a "restore point" in XP as a precaution before installing any patch. While this patch installed just fine for me, I take no responsibility for it or any resulting consequences as it is a Microsoft patch. I'm merely pointing you to it as a resource. Let's be safe out there.
October 16, 2008
Beware, Many Browsers are Vulnerable to "Clickjacking"
Here's a truly disturbing thought: "Submit" buttons (and other buttons, such as "Print", "Next Page", etc.) are very common in web pages. That "Submit" button you think you're clicking on in your web browser could be redirected to to another web site or perform just about any other type of action. This is known as "clickjacking", where the attacking web site steals your mouse clicks. What's worse, all of the popular web browsers are being reported as vulnerable: IE, Firefox, Safari, and others. Ouch.
The problem is, clickjacking takes many forms. Some require javascript, and some don't. Some of the vulnerabilities show up in other web-related add-ons, such as Adobe Flash and Microsoft's Silverlight. One important way to help stop at least some of the clickjacking attempts is to disable javascript in your browser. The huge downside is that because javascript is present on so many sites today, disabling it just cripples your web experience, and possibly a number of web apps. So instead of disabling javascript for all sites, it's better to enable JavaScript only for approved sites. The same goes for ActiveX, which has long been a security challenge. But again, that's a lot of sites for most of us, so it pretty much stinks either way you look at it for a supposed "quick fix".
Per Stuart Johnston's column in Windows Secrets, here's how clickjacking works:
In clickjacking, surreptitious buttons are "floated" behind the actual buttons that you see on a Web site. When you click the button, you're not triggering the function that you expected. Instead, the click is routed to the bad guy's substitute link.You can also read Robert Hansen's blog posting, "Clickjacking Details", which describes it in much more technical detail. It also lists specific types of clickjacking exploits, and each of their statuses in terms of whether they are still unresolved, have been resolved, or will be fixed in a future version of the software mentioned.Robert Hansen, CEO of SecTheory, and Jeremiah Grossman, chief technology officer of WhiteHat Security, are the bug sleuths who discovered this latest generation of potential security glitches.
They point out that even users who watch their systems like a hawk can be victimized.
"There's really no way to know if what you're looking at is real," Hansen told Windows Secrets.
In fact, Hansen and Grossman found so many new ways to attack your PC - and your Mac - that they categorize these threats as a "new class" of exploits. While this class includes scripting attacks, it also affects scriptable plug-ins such as Microsoft ActiveX controls, Skoudis said.
Clickjacking isn't new. In fact, it dates back to at least 2002, Hansen said. What's new is the range of browser vulnerabilities that make clickjacking possible.
Probably the best advice to take away from this is to be careful which web neighborhoods you're visiting, just like in the real world. Mainstream companies usually don't want the bad press and customer reactions, so it's more likely going to be the fringe sites that would implement these security exploits.
The trick with many exploits is that they somehow have to get you to go there. So don't click on web site links contained in your incoming e-mail, unless you're absolutely sure they are legitimate (which can also be somewhat difficult to tell these days). I can see where a lot of phishing e-mail scams would send you an official-looking e-mail with a link to an official-looking but totally fake web site, which would then either steal your personal data or employ clickjacking or other tactics to accomplish their nefarious goals.
September 09, 2008
Webtop Wars & Security Patches for Google Chrome Browser
Several days after its beta release, and it looks like Google's new Chrome browser suffers from security flaws much the same as its competitors. CNET News' Security blog posted about a number of security patches already released by Google. Also, yesterday Google established a Google Chrome Releases blog to let users know about releases, fixes, security updates, and other changes.
Just remember, Chrome is a beta release so it's a work in progress. Microsoft's IE8 beta has also been well underway, with the first beta released back in March and the second beta released two weeks ago. IE8's beta sports a number of interesting new features, which are detailed at Wikipedia's IE8 page -- just remember it's an unofficial source.
And of course, Firefox 3 beat them both with an official release earlier this summer. I haven't seen this much excitement and competition over new browsers since the dot.com era.
Opera was made free some time ago, but it doesn't look like it's helped their market share in any noticeable fashion. I've typically shunned using their browser due to various incompatibilities reported by users, and I've augmented both IE and Firefox with various add-ons and plugins to get most of Opera's benefits. I actually find their Opera Mini browser to be more compelling, as it offers a different browser toolset on my BlackBerry than its bundled browser.
And let's not forget Safari, both on Apple PCs and the iPhone/iPod Touch devices. Granted, that's a different platform than Windows.
This time, Google has a vested interest in having some control over your webtop, particularly in light of their expanding applications list (think Google Apps). As defined at Wikipedia:
"A web desktop or webtop is a desktop environment embedded in a web browser or similar client application. A webtop integrates web applications, web services, client-server applications, application servers, and applications on the local client into a desktop environment using the desktop metaphor. Web desktops provide an environment similar to that of Windows, Mac, or a graphical user interface on Unix and Linux systems. It is a virtual desktop running in a web browser. In a webtop the applications, data, files, configuration, settings, and access privileges reside remotely over the network. Much of the computing takes place remotely. The browser is primarily used for display and input purposes."That's a fair definition. However, Google is going to have to work hard to compete in light of IE's and Firefox's established presences. ZDNet's Hardware 2.0 blog posts the question, "Is Google’s Chrome sliding into obscurity?" In tracking Chrome's usage hourly, after initial increases in market share, it has started to slide back over the past few days.
So while I'm glad to see another major player, especially one generally committed to adhering to web standards, I'm also beginning to think that after the initial media hype free pass is over, Google will need to deliver a fast, safe, stable, feature-rich, and innovative browsing experience to win over, and more importantly, keep the minds and hearts of its users. And that includes being very, very transparent on the data privacy aspects, both when using its normal mode and private browsing mode. I'm not so sure that a search engine company will be able to do that since it's an inherent conflict with their business model. But as I said in my prior post, I'm glad to see the competition intensify as we'll benefit by seeing more rapid and innovative developments on our webtop.
I don't see Chrome ending up as most people's primary browser -- IE and Firefox will continue to dominate there -- but as a secondary or tertiary browser, it may be used for more niche purposes. But I also think people are willing to cut Google some slack for now, considering this is their very first release. After all, the other browsers have been out for years, so Google has to catch up quickly. They did pretty well with Gmail, but again, I don't use it for any sensitive information because it's "read" by their automated services. Truth be told, I still prefer Yahoo's classic e-mail interface, having tried their new one and went back to the old one. It just works the way I like.
So far, I've pretty much filed Chrome under the category of "Google needed a web browser for their webtop offerings". We'll just have to see if they convince us otherwise.
September 05, 2008
What You Need to Know About Chrome, Google's Shiny New Browser
Google just released a beta of Chrome, throwing their hat into the browser wars. A couple of thoughts on what this means, and what you need to know about it if you want to try it:
First, the Google Chrome browser sports an interesting minimalist design and some unique features (particularly how it approaches the tab metaphor and stability). Google has thoughtfully outlined them in video, and check out Walt Mossberg's practical perspective, including a good description of its pros and cons. It is, after all, a beta or test release.
Chrome sports two browsing modes: Default and Incognito. Those who are concerned over their browser breadcrumb trails will likely welcome Incognito, which is meant to allow you to surf without Chrome saving the information after you close the window. Of course, there are other ways to track your web activities, particularly in corporate environments, so don't get too comfortable with this. Even some personal firewalls keep logs on web sites visited.
That brings me to the next point -- privacy. Why would the leading search engine company, skilled at tracking data across the web, release a web browser? How much of your personal web surfing information is being tracked and recorded by Chrome, either stored locally on your PC or sent back to Google? The conspiracy theorists are having a field day with this. After all, Google tracks more of your web activities while you're logged into your Google account than as an anonymous user. So why wouldn't they do the same with a browser they developed?
Well, the jury is still out on this one, particularly on its increased reliance upon a user's browsing history. Fortunately for us, Chrome is an open source software project -- which means that others can look at the code and see what it is doing. This is one of the great reasons why I frequently look to use open source software. Second, here's a post by Google's Matt Cutts which attempts to explain what does and doesn't get sent between your PC and Google when you use Chrome. I for one appreciated the transparency, and am hoping that it's a fairly complete accounting of which types of data are being transferred, and under which use cases. Although it should be noted that Matt isn't on the Chrome development team, as he's the head of Google's webspam team. So while well-intended and useful, consider that it's somewhat secondhand information.
Just as importantly, Google is more than ever jumping into mainstream software development (I'd be hard-pressed to get more fundamental than how we access the web and its rich content). Along with Google Apps, this pits them directly against the market share-dominant Microsoft on yet another level. However, it would also be naive to ignore the information and relationships gained from Chrome users to further enhance and develop their search services, where Microsoft has never quite "gotten it" in my opinion. Chrome also gives Google a browser by which it can serve up its other web apps without fear that Microsoft will alter IE in some proprietary or anticompetitive manner. This isn't to say that Chrome is superior to all other browsers, as it still has some issues and is missing several key features. But it gives Google a platform over which it didn't have control previously.
Despite the privacy concerns, which should be more formally addressed to users' comfort level, I'm always glad to see another major player in the browser market. If you think about it, web browsing really hasn't changed all that much from the mid-90's. Sure, there have been a number of new enhancements such as tabbed browsing and inline searching, but the underlying mechanics have remained the same for well over 10 years.
Also, how many of us are genuinely irked when we have one browser tab crash and it crashes your entire browsing session, whether it be IE, Firefox, or whatever -- especially when you have a dozen or more open tabs at the moment? Sure, they'll offer to reopen your last set of open pages, but then you've lost all the forward/back browsing capability for each one, so you can't easily track around to re-find that site you found in the middle of your surfing. Your browsing history might have it, but you'll have to hunt for it.
Using this as an example, I'm glad to see that each Chrome tab runs separately in memory from the other tabs, so that when one tab crashes, it doesn't crash the others. With Google's savvy, ease of use, and advanced technologies in simple wrappings, it's going to up the ante among web browser developers and keep them on their toes. That nudge has been a long time in coming, as evidenced in Walt Mossberg's observations:
"Meanwhile, Microsoft hasn’t been sitting still. The second beta version of IE8 is the best edition of Internet Explorer in years. It is packed with new features of its own, some of which are similar to those in Chrome, and some of which, in my view, top Chrome’s features."Whether you're in the Google or Microsoft camp, or just want a better browser, that's good news for all of us.
July 25, 2008
Personal Firewall Software - Security Test Results Reveal Surprises
Matousec, a security consulting and research group named after its founder, David Matousek, researched and tested security performance on numerous software firewalls (also known as personal firewalls, as they are installed on personal computers rather than being hardware-based).
The firewall test results and rankings are worth a read if you've just purchased a new computer, considering a change, or your annual subscription is nearing its renew point. Some of the better known firewall products such as those from Norton, McAfee, and ZoneAlarm were ranked particularly low. The results were somewhat surprising on that front, although I wasn't surprised to see that the free Comodo Firewall Pro remained in the top-ranked group, as it's been receiving accolades for some time.
It's good to see the results and methodology so we can make more informed choices, and the software vendors can learn more about their weaknesses so they can plug the holes. It's also a good idea to watch the rankings over time to see which ones are progressing, and which ones are falling further behind.
Update 8.1.08: I should also mention a very noticeable trade-off between certain firewalls. Some firewalls will prompt you, seemingly endlessly, to allow or block a program or service that's trying to access the Internet -- particularly while it's in "learning" mode. I believe Comodo Firewall Pro and ZoneAlarm operate as such. Others, like Norton Internet Security, silently grant or deny access to your programs based upon its considerable database of common applications.
From a user perspective, especially for those who are not security professionals, the latter approach provides what I call "usable security". The problem with the former types of firewalls is that after a short while, users become increasingly annoyed with the barrage of prompts. At that point, they'll likely either begin allowing all access or denying all access to the vast majority of the prompts. Obviously, neither is desirable. Too much access granted, and you've compromised the security of your PC and network. Too little access granted, and well, you won't be getting much done on the Net now, will you? Couple these firewall nags with Vista's User Account Control (UAC) prompts, and it's enough to make you run screaming straight for a Mac.
I've used a number of personal firewalls over the years, and have to say that while the Norton Internet Security firewall didn't measure up on these particular tests, I greatly prefer its more balanced user approach. By the way, for those of you who understandably left Norton after using their bloated 2005 and 2006 products, it's worth another look. Since the 2007 version, both the Norton Antivirus and Norton Internet Security packages have been redesigned from the ground up with the goal of optimizing their performance. I've found it performs much more quickly, takes up less resources, and is virtually invisible to the user. Yes, it makes certain decisions for you automatically, which I'll agree with some security experts results in some compromises. However, it's usable, and gets out of your way so you can actually get some work done. Now, if a software developer could develop a top-notch personal firewall that could pass these advanced security tests while being transparent to us, the users, now that's something I'd be very interested in having on my PC.
June 05, 2008
Yet Another Redaction Infraction
As reported on Law.com, a plaintiff's firm against GE in a class action sex discrimination case improperly redacted filings appearing on PACER, allowing readers to copy and paste the sensitive redacted text into another program like Word. Sounds like the classic mistake of adding black boxes without stripping the underlying text. I'm surmising they filed PDFs which is usually the standard in e-filing.
Taking the plaintiff firm's spokesperson at their word (I'm assuming the leak wasn't intentional), it sounds like it was a mistake made from ignorance. The article reports that they were working to correct the problem by making emergency, corrected filings with the federal court clerks. At that point, it's probably best thing they could do to prevent further inadvertent disclosures. But how do you unring the bell?
Rather than restate the article (which I recommend reading as a cautionary tale), I'll add that law firms and corporate law departments still need to be vigilant in the proper way to redact electronic documents. Historically, Adobe Acrobat did not provide appropriate redacting tools (a point I've suggested to them over the years and to which they listened by adding redaction in Acrobat 8 Professional -- but take note, it's not in the Standard version). So firms running on older versions of Acrobat or other PDF tools without built-in or third-party redaction tools (such as Redax from Appligent), remain at risk. By the way, Acrobat 9 was just announced and will likely ship in the next month or so. The same caveat re: Standard-sans-redaction applies per Acrobat's Feature Comparison Table.
If you haven't already invested in these tools, your process may be similar to this:
- Justifying the need for the proper tools (um, just read the article above)
- Communication to the legal staff as to why they are required, using real world examples to demonstrate the impact and that it's not just a hypothetical
- Investment in the appropriate software tools
- Training and practice for the legal staff actually performing the redaction, and it's not a bad idea for supervising attorneys to at least understand the underlying principles (as the plaintiff's lead counsel said, "I didn't know that.")
If your organization is already using appropriate redaction tools (you are, right?), it's probably a good idea to have redaction "tune-ups" with your staff. Meaning, reviewing and/or creating documentation for the standardized and firm-approved process of redacting documents, holding periodic refresher and new user training (consider "on-demand" video training snippets for training or follow-up support so busy professionals can fit it into their schedule), and consider making it part of the organization's overall risk management initiatives so it's at least on the radar. While you're at it, you might want to take a look at how many people actually know how to properly secure or lock a PDF, particularly those posted to external sources such as web sites.
For other helpful resources, the NSA (yes, that NSA) published a guide several years ago describing how to redact documents after the federal government suffered several information breaches and embarrassments from improper redaction efforts. There are also several very informative blogs dedicated to using PDFs in the legal market, such as Acrobat for Legal Professionals and PDF for Lawyers, both of which have definitely addressed redaction issues.
While these tools have significant price tags, as the saying goes, "an ounce of prevention..." Taken into perspective, an organization is likely going to incurs costs far greater than software and training when dealing with just one of these mis-redaction incidents. Sounds like a pretty good ROI to me.
Posted by Jeff Beard | Permalink
March 05, 2008
Free "Shadow Explorer" Displays & Recovers Shadow Copies on Any Version of Vista
I've posted previously about Vista's Shadow Copy feature, and its security and e-discovery implications. Having explored it a bit more over the past several months, here are some things legal and IT professionals should know about it. Consider it a crash course in Vista Shadow Copies, and I'll share how to get a new utility program for accessing and restoring these hidden files.
Please keep in mind some of these items are based on information found online including unofficial sources, so it's best taken as my personal interpretation of that information (meaning that if I've unintentionally stated something incorrectly, don't hold it against me, and I would appreciate constructive feedback):
- Numerous postings online have stated that by default, all versions of Vista automatically create shadow copies of your documents and other user data files and folders as part of the "System Restore" feature.
- You can turn off "System Restore" to disable shadow copies, but it's a bit of throwing the baby out with the bath water. You see, "System Restore" allows you to roll back the clock on your system to an earlier (and hopefully more stable) state. This is incredibly useful whenever your Vista system experiences problems (such as after installing a problematic program, driver, or update, adverse registry changes, etc.). FYI, newer Apple operating systems offer a somewhat similar feature called "Time Machine".
- By default, Vista allocates 15% of the drive's size or 30% of available free space, whichever is smaller, for storing this data. In Vista, Microsoft removed the nice slider control available in Windows XP, so changing its space allocation requires some arcane text commands with administrator privileges. Thus most users will just leave it as-is. On larger hard drives, this creates a fairly large backup cache. For instance, on a new 200GB hard drive, up to 30GB would be dedicated to storing these hidden backups. When the allocated space fills up, Vista deletes the oldest backups as needed to make room for the new ones.
- However, only the Ultimate, Business, and Enterprise editions of Vista actually allow users to access and retrieve the hidden shadow copies via the "Previous Versions" feature in Windows Explorer.
- This means the Vista Home Basic and Premium versions create these hidden shadow copies but do not provide any way for their users to access or retrieve them. This results in potentially large amounts of wasted disk space and additional data retention concerns. Perhaps Microsoft intended this as a teaser to entice Home users to upgrade to Vista Ultimate, but they really should have disabled shadow copies on those editions or alternately provided the "Previous Versions" feature to access and restore them as needed.
- To help address these issues, Shadow Explorer is a free basic utility program (not affiliated with Microsoft) which allows these users of other Vista versions to access and restore these prior shadow copy backups. However, unlike "Previous Versions", it requires administrator privileges to run. (But see my caveat at the end of this post since it's a 0.1 release.)
- Even Vista Ultimate, Business, and Enterprise users and IT departments may find Shadow Explorer of use. I've discovered firsthand that Vista's "Previous Versions" feature is dependent on a number of system and service prerequisites, and the lack of any one of them will disable the ability to access and restore these Previous Versions. For instance, disabling a drive's administrative share, certain Windows services, or networking settings can all disable the "Previous Versions" listing in Vista Ultimate even though the backups are still present on the drive.
- Tip: If you have Norton Internet Security installed and have run its "Security Inspector", it may have reported and disabled several hidden administrative drive shares (such as C$) as security risks (which they are indeed). However, as mentioned above, these administrative shares are necessary for "Previous Versions" to function in Vista. So if you want to leave these shares disabled for better security, the Shadow Explorer utility program allows you to access and restore shadow backups even though Vista's own "Previous Versions" feature is disabled.
Organizations interested in migrating to Vista will need to explore these issues in more detail before crafting their security and group policies. I expect some will elect to disable System Restore altogether and rely upon other system restoration methods to address user support issues as they arise. Others may move user folders onto a separate disk partition or drive and simply turn off "System Protection" for that location. Such options may improve Vista's performance if it's not churning away saving hidden backup copies, and it's usually a good idea to separate documents from program files for a number of valid reasons.
So it's all the more puzzling to try to understand why Microsoft chose to disable access for Vista home users, as they are the ones most likely wanting to use and restore Shadow Copies. I seriously doubt informed businesses would want multiple hidden document versions floating around on their corporate laptops and desktops, particularly in light of numerous regulatory and litigation concerns.
Shadow Explorer Tutorials can be found at:
http://www.howtogeek.com/howto/windows-vista/recover-files-with-shadow-copies-on-any-version-of-windows-vista/
http://www.shadowexplorer.com/documentation/manual.html
Please keep in mind that Shadow Explorer is a very basic version 0.1 release. While it worked fine for me during my brief testing, it may contain bugs and other issues consistent with a new release. With that said, it provides an easy way to access, view, and restore the various shadow copies in Windows Vista. I applaud the author for providing such a useful tool, and for considering these additional planned features as it's developed further.
February 09, 2008
Word 2007 -- A Tale of Two Experts @ LegalTech NY
It was the best of times: While making my way through the vendor hall jungle at LegalTech NY, I had the pleasure of catching up with Donna Payne (Payne Group) and Sherry Kappel (Microsystems). I always find time to seek out these document technology savants, and this week's discussions were as helpful as ever.
My personal opinion is that Office 2007 is the clear winner from Microsoft this past year (definitively overshadowing Vista), and the massive improvements are well worth the office suite upgrade and third-party integration efforts. Sherry insightfully observed that with Word 2007's linked styles right out of the box, firms are likely going to need to pay even more attention, not less, on training and reinforcing solid style usage with their user base. As Sherry mentioned in a recent ILTA publication, if you're not automating your document practice, then how are you going to maintain your margins when your corporate clients demand a substantial rate cut? Also, she noted that the new XML format, while adding some needed document file stability, also adds a bit more complexity due to the XML intricacies.
Donna Payne and I had some techno.fun comparing and contrasting Word's built-in Document Inspector capabilities to a dedicated metadata scrubber such as Payne's Metadata Assistant. On one hand, it would seem that Word's built-in Document Inspector gets the job done. Both Donna and I have used it and found it to be effective, especially in a pinch where you're working on a simple document and just need a quick scrub before sending it off to someone. When you want to remove just about everything, it pretty much does the trick. But in comparing notes, we quickly agreed it has several fundamental weaknesses:
1) No Workflow: In other words, when using Word's Document Inspector, you have to remember to manually scrub and save the Word document before you start the e-mail process. Third-party scrubbers add the necessary workflow which allows you to scrub the file as part of the e-mail attachment process.
2) No Selective Scrubbing Within Each Category: For each of Word 2007's five scrubbing categories, it only offers you an "all or nothing" approach for the items in that particular category. There is no middle ground. So if you want to scrub only some of the document property fields, but keep a few like "Author" and "Title", you'll need to first remove all of that category's metadata, and then manually retype in the few you want to retain. And that's a bad thing, because you can lose useful or necessary metadata in the process if you're not careful.
So while we've seen very substantial improvements in Word 2007, firms and companies will still need to assess their overall practice workflow and specific scrubbing needs, and it will likely take third-party add-ins to more fully address them.
Posted by Jeff Beard | Permalink
January 31, 2008
FeedDemon is Now Free -- Read Why
NewsGator is now giving away several of their RSS or news reader programs for free. These include FeedDemon, NetNewsWire, NewsGator Inbox, and NewsGator Go at the free download page.
Many of you know FeedDemon has been my preferred RSS reader since I started using it at least 4-5 years ago. I've also played around with other readers, both PC client and web-based, but kept going back to FeedDemon. I also chose FeedDemon as the best RSS reader or news aggregator for a prior Law Office Computing Shootout feature article. It packs a ton of useful features into a very intuitive, fast, and polished package. But rather than extoll upon its many great features and advantages, MediaBlab has already done a fine job of that.
Lest ye think NewsGator is abandoning their client-based software programs, it's just the opposite according to Nick Bradbury, the programming genius behind FeedDemon. In a nutshell, they're making it free to expand their client software users. Why? Because we humble human beings seem to make an effective relevance engine. You see, when using one of these now-free NewsGator programs, it sends back information when one flags an article, saves a clipping, or e-mails it to a friend. By these simple actions, we're signifying that particular item was important or relevant. I'm quite reminded of how Google was founded upon ranking relevance via tracking a site's inbound links. Nick gets it.
All this aggregated information helps NewsGator determine which RSS feeds and articles are more relevant than others, and helps them "bubble it up" to the surface for their enterprise customers. That's where NewsGator is refocusing their efforts and attention. So in exchange for getting the software free, users help them by doing nothing more than they are already -- reading, flagging, searching, etc. As Nick says, "Your attention is valuable." Sounds very Web 2.0 to me.
To their credit, both Nick and NewsGator recognized that we're just a little concerned about our privacy. Nick covers that in his post, and points us to NewsGator's FAQ so we can decide for ourselves. Apparently, we can choose to disable the data collection and reporting mechanisms, albeit at the loss of features like data synchronization.
Also, since many of their enterprise customers use these very same programs, Newsgator appears to have a vested interest in keeping them updated rather than abandoning them.
I give them credit. In a very innovative way, they're providing value in offering a first-rate RSS reader for free and enabling us to see what news is popular with others. NewsGator is gaining value in return while being fairly transparent about it. Of course, the new free FeedDemon 2.6 specifically contains more "phone home" mechanisms for "attention reporting". While I would normally suggest staying with an earlier version for privacy reasons, if their FAQ is accurate and we can indeed disable those tracking and communication methods, then there's probably little harm. Besides, even if they could still track my RSS reading habits, there's nothing there that would make me miss any sleep. But I'd still hold them accountable so that all users have a clean choice.
I also really like Nick's attitude and customer focus in his other blog post:
"Sure, I enjoy making money as much as the next guy or gal, but I'm really doing this because it's fun. I like writing software, and I'm going to keep writing it until my fingers break off.Now there's an attitude I wish more software developers would fervently adopt!There's no point in creating software in a vacuum - you've got to make it useful, make it scratch an itch, for it to be truly rewarding. And to do that, you've got to listen. You've got to pay attention to what people are asking for and what they're complaining about.
So, regardless of whether you've paid for FeedDemon in the past or you're a new user now that it's free, I'm not going to stop listening. It wouldn't be fun otherwise."
November 27, 2007
Addressing Laptop Data Vulnerabilities
Law.com has an excellent article discussing several workable approaches for securing data on corporate laptops. A quick look at one list of data breaches illustrates how sensitive data continues to be compromised by unsecured storage on laptops.
It's a particularly savvy article because its first piece of advice is not to overreact and go overboard -- "Draconian laptop-use policies may, ironically, increase an enterprise's vulnerability." Consider that employees often respond by finding other ways of circumventing security to make their jobs easier, which usually means making the data more accessible (i.e., less secure). For instance, blocking file saves to the laptop's hard drive or limiting e-mail inbox sizes can result in employees saving the data to unsecured thumb drives or forwarding sensitive e-mail to personal e-mail accounts. Where there's a will, there's a way. EMC was quoted as opting for a more blended approach, depending on the sensitivity of the data.
Another interesting suggestion was full hard drive encryption, rather than just encrypting the documents folder. This is often a highly debated solution. In my experience, some IT professionals will quickly suggest that doing so will entail a performance hit on the user and cause additional support problems. I'd say that noticeable performance hits are more likely with older, slower laptops. If this presents serious problems, consider phasing in encryption or issuing new laptops to those accessing more sensitive data.
Also keep in mind that when you are working on a laptop, it is likely creating a number of temporary file copies on the hard drive, sometimes in places outside the document folders. Full drive encryption therefore provides more complete protection for these additional copies of sensitive data. Naturally, such a solution would need to be thoroughly tested to determine the real-world impact on users and the IT support organization. Another issue to consider is segregation of the master keys -- do you allow one person or group to have them, or do you segregate them between two entities within the organization to avoid unilateral and potentially undesirable actions? I liked the allusion to the missile silo two-operator requirement.
Removable storage continues to be a major concern, such as flash thumb drives and external hard drives. And let's not forget iPods, which are either the former or latter type of devices. On one hand, these drives are very useful tools for mobile users. When unsecured (e.g., unencrypted), they can represent a larger security threat due to their tiny physical size and increasing storage capacities. For example, an 8GB thumb drive goes for less than $100 and can store a staggering amount of information. The article mentions products that control which devices can be plugged into which computers, and the best ones allow exceptions to be set when needed. If thumb drives will be used and supported, I'd suggest issuing employees with the following: only those models which support high-end encryption, such as AES, and make its entire capacity encrypted before it's issued to the employee. While a savvy user will likely know how to reformat the thumb drive to make it unprotected, the default encryption status is in your favor for the majority of users.
Many new laptops have built-in fingerprint readers, which can make security a bit more convenient. But as the article states, users often forget a key step: Register more than one finger with the device, so if you cut or burn your primary finger, you can use another one to gain access via the reader. Also, without the back-end drive encryption, keep in mind that a fingerprint reader only locks the front door. There are other ways to get to the unencrypted data on the hard drive, such as removing it from the laptop and accessing it from another PC.
Lastly, the article mentions lojack services for laptops, which hopefully reduce their recovery time. However, once the horse is out of the barn, it's too late to employ any of the above security measures. An unprotected hard drive containing sensitive data can be copied very quickly to a number of storage devices. The data contained on missing laptops is often much more valuable and/or costly to an organization than the cost of the physical laptop itself. An ounce of prevention...
Posted by Jeff Beard | Permalink
November 20, 2007
Test Your Phishing IQ
Think you can tell the difference between a legitimate and a phishing e-mail? Take the SonicWALL Phishing IQ Test, a collection of ten e-mail screens. Read the helpful hints before taking the test, as they explain the links displayed.
After you identify each e-mail as "Phishing" or "Legitimate", the final scoring page includes links to explanations. In each e-mail explanation, the comments in green relate to legitimate e-mail indicators, while the comments in red highlight why that item may be indicative of a phishing e-mail. Be forewarned that several e-mails took more than a cursory look to identify them properly -- which is exactly why phishing works.
I happened to score 9 out of 10. I took some issue with Question #5 as it's not a particularly valid test in this format for the following reasons: The links matched in the example, but the static screen capture prevented any further investigation of the underlying link -- i.e., the html source code of the e-mail was not accessible. Also, you would be able to confirm the last four numbers of your own credit card matched those in the e-mail. With that said, I very much agree that you cannot rely solely upon what is displayed in the status bar due to scripting tricks. The explanation for Question #5 also failed to mention the lack of a secure "https" link as another potential indicator. It's important to note this example was the most subtle of the ten in my opinion, and therefore more likely to succeed in "phooling" people.
Overall, it's a good test, and ten minutes of your time could help you avoid disclosing sensitive information online. On a personal note, it's good to see that Outlook 2007 has more features to help users in this regard. It's not perfect, of course, but it's definitely a step in the right direction. Every bit helps.
Browser Beware: Web 2.oh.oh?
As the web has become more feature rich, new security exploits are popping up all over. CTO and Chief Researcher Roger Thompson over at Exploit Prevention Labs has posted half a dozen short videos showing how sites have been compromised or are otherwise serving up some bad content due to embedded advertisements.
The problem, as he aptly describes, is that most web traffic goes straight through your firewall. Some of the exploits use javascript to redirect to other sites. In another example, he shows how the Bank of India site was compromised to automatically download a frightening number of malware files simply by loading the web page in an unpatched browser. The scary part is that it was only detectable by running a separate debugger window -- meaning that the vast majority of web visitors wouldn't have seen anything amiss until it was far too late. He claims that anti-viral software isn't as effective in recognizing and stopping these types of exploits, and I tend to agree. (Please note I have not tried their LinkScanner Pro software, so this isn't an endorsement of that particular product.)
As the holiday season usually spurs a noticeable increase in spam, scams, and other exploits, remember to keep your PC and your information safe with updated patches, anti-spyware, ad blockers, etc. Also consider using a non-IE web browser, as IE's ActiveX helps to enable these drive-by downloadings. However, keep in mind that using alternative browsers could still expose you to some risk when javascript is enabled. Indeed, many web pages nowadays won't load or perform properly with javascript turned off, so exploits such as these will continue to crop up. Also keep a keen eye on your web browser's status bar (usually in the bottom left corner) when mousing over links and while web pages are loading, as sometimes they may be your only clue that you may be visiting a "Web 2.oh.oh" site.
July 26, 2007
More on Vista Shadow Copies & the Dreaded Index.dat Files
As I posted previously, by default Windows Vista enables shadows copies in Vista Ultimate, Business, and Enterprise editions. Shadow copies aid in recovering prior versions of files and are part of Vista's system restore points protection (which was also included in XP). So, basically, it appears the only way for a user to turn off shadow copies is to disable the system restore point protection. The problem is that the system restore point feature is incredibly helpful in troubleshooting and curing a system's ills by rolling back Vista's system files to a previous point in time. This is especially useful after installing a problematic program, driver, or update. In effect, turning off shadow copies is throwing the baby out with the bath water. Nice going Microsoft. If there's a way for enterprises to set a Windows policy to disable shadow copies but keep system restore points active, that would be a good solution. However, I haven't come across that yet.
Now on to Index.dat files. Windows has used these for many years as a way to store data histories, such as your complete URL browsing history. Since these Index.dat files were always kept open by Windows, it took special utilities such as the Index.dat Suite to view their contents, and even better, delete them at bootup before Windows fully loaded. It seems Microsoft has been aware of the problem and has changed the way that Windows and IE work to better clear out the contents of these tell-all files. This blog post from the Windows Core Networking MSDN blog has a greatly detailed discussion of how the WinInet's Index.dat files work under Vista, as well as this one about clearing tracks with IE7.
With e-discovery hot on everyone's plate with the new federal rules, these are additional reasons to have qualified and experienced professionals on your forensic team.
July 24, 2007
Windows Vista Security: Pros and Cons, Third Party Solutions Still Needed
Vista has a number of new security features, such as a two-way firewall, Windows Defender, UAC (User Account Control), BitLocker Drive Encryption, and more. These are certainly improvements over XP in terms of baking more security into Windows. My thoughts and experiences with them so far, along with recommendations for third-party security apps where needed:
Vista Firewall:
While Vista indeed comes with a two-way firewall, it's a mixed bag. While it blocks incoming requests (Windows XP does this too), it appears there's no easy way to configure Vista's firewall to block unauthorized outgoing communications (for example, spyware phoning home from your PC). A user would need to add blocking for each type of malware out there today, which as we know, numbers in the thousands. Not good, so I embarked on researching several of the Internet security suite products for easier and more robust protection, and posted my results below.
Windows Defender:
Windows Defender is basically the next generation of Microsoft's Windows AntiSpyware. For users that don't have any anti-spyware protection installed, this is certainly a step in the right direction. However, it's not an antivirus program. For that, you'd need to subscribe and pay for the Windows Live OneCare service, listing for $49.95/year on Microsoft's web site. The site lists OneCare's features as Antivirus, Antispyware, Anti-phishing, Firewall, Performance tune-ups, and Backup and Restore. It's interesting to note a number of these are already bundled in Vista, at least to some extent. Again, while I applaud Microsoft for offering additional security, they don't have a great track record in the security business, and for that price I found several Internet security suites that were more mature and robust for roughly the same price. Also, I still like having Spybot Search and Destroy installed to catch anything the other solutions missed, and vice versa.
UAC (User Account Control):
First off, if you haven't heard of or seen Vista's UAC prompts, you absolutely must view this hilarious Apple TV commercial. For certain types of actions, Windows will prompt you to confirm whether you want them to run or not. It's annoying and productivity-sapping as you're basically issuing commands twice. The idea behind it is to prevent malware from doing something unauthorized on your PC. As the commercial mentions, you could turn it off, but then it wouldn't provide any alerts or protection. I've read that Microsoft is looking to make it less intrusive and annoying in the future. One could only hope.
New User Account Types:
Vista helps address one of the support problems with Windows XP -- standard user vs. administrative rights. Under XP, it was common to have to log into Windows as a system administrator to install programs, make system changes, troubleshoot, etc. With Vista, standard user accounts can be temporarily escalated to administrator privileges simply by typing in an administrator password when prompted. Granted, I seriously doubt that corporate enterprises will allow their users such privileges, but for home use, it's a great feature that eliminates a lot of user swapping and logins back and forth. It also allows me to work as a standard user with limited privileges for better security, while providing me temporary superpowers when needed.
BitLocker Drive Encryption:
Wouldn't it be nice to know that if someone stole my laptop, they couldn't get access to my confidential e-mails, documents, financial information, and more? Hard drive encryption was one of the reasons I wanted to purchase Vista Ultimate, as it's only available in Vista Enterprise and Ultimate editions (so don't expect it in any Home version nor the smaller business editions). With the staggering number of laptop thefts and inadvertent disclosures of confidential data and corporate data privacy debacles, this is a welcome addition to Windows. Just for "fun", take a look at the very long Privacy Rights Clearinghouse list of data breaches since 2005. In your browser, press CTRL-F and type "laptop" to find each occurrence involving a laptop computer breach. Scary, isn't it?
Sure, there are plenty of third party drive encryption products available, but it's nice to see one incorporated into the OS itself. I haven't tried it yet, and there is some drive preparation required. As I understand it, BitLocker needs to create two hard drive volumes. One is unencrypted for all of Vista's system files for better performance. The other is encrypted and contains all of the non-system files (including your data). FYI, Vista Ultimate users can download a free "Extra" via Windows Update that streamlines this preparation process and makes it more user-friendly. As I prefer to use Norton Ghost to backup Windows installations, I haven't enabled BitLocker until I know that Ghost can handle backing up and restoring these encrypted volumes. Symantec just released Ghost 12.0 for Vista compatibility, so I'll be checking up on its ability to handle BitLockered drives.
Data Execution Prevention (DEP):
Vista continues to support DEP as did WinXP SP2. Per Microsoft, Data Execution Prevention (DEP) is a set of hardware and software technologies that perform additional checks on memory to help prevent malicious code from running on a system. In plain English, it prevents programs from running from memory marked for storing data, not programs. This is one way the system can stop malicious software exploits.
On my Toshiba laptop, I used SecurAble from Steve Gibson (of ShieldsUp! fame) to determine whether my new Core 2 Duo processor had hardware DEP capability and whether it was enabled. Sure enough, it had DEP, but Toshiba shipped the laptop with DEP disabled in the BIOS. After I enabled it, I have encountered a few instances where Windows closed Internet Explorer and other apps under DEP protection. As I have a clean system, I'm chalking these up to software bugs. As an educated guess, this is probably why Toshiba chose to leave it disabled -- less problems for users out of the box (but perhaps leaving them open for more problems down the road without hardware DEP protection). Most processors made in the past year or two support hardware DEP, which is preferable to the software-based DEP protection Vista will use if it doesn't detect it in the processor.
Why is DEP so important? I'll let Steve Gibson answer that by quoting from his site:
"Why would data or communications buffers ever contain executable code? . . . because so-called "Buffer Overrun" attacks are the predominant way Internet-connected computers have historically been remotely hacked and compromised. Hackers locate obscure software vulnerabilities which allow them to "overrun" the buffers with their own data. This tricks the computer into executing the hacker's supplied data (which is actually code) contained within that buffer. But if the operating system has marked that Internet communications buffer region of memory as only being valid for containing data and NOT code, the hacker's attack will never get started. Instead, the operating system will display a notice to the user that the vulnerable program is being terminated BEFORE any of the hacker's code has the chance to run.Third-Party Internet Security Suites:The real beauty of this system is that it provides strong protection from UNKNOWN vulnerabilities in the system and user programs.
Anti-Virus and anti-malware software is useful, but as we know, virus signature files must be continually updated to keep A/V software aware of new threats. Significantly, A/V software is unable to protect against unknown viruses and malware intrusions because it searches for known malicious code rather than detecting and blocking potentially malicious behavior. Hardware DEP, on the other hand, when properly configured, hardens the entire system against both known and unknown vulnerabilities by detecting and preventing the behavior of code execution in data buffers.
Buffer overrun vulnerabilities are so difficult to prevent that scores of them are being found and exploited in operating system and application software every day. Taking advantage of modern processor XD/NX capabilities is a powerful way to fight back and prevent this most common class of Internet vulnerabilities."
While Microsoft's emphasis on security is welcome, I have to say their security track record gave me great pause in relying exclusively on their solutions -- particularly when there are mature and tested security products available. For my new Vista laptop, I took a look at three leading Internet security suites from ZoneAlarm, Symantec (Norton), and McAfee. Only one met my definition of appropriate security features, ease of use, and system performance.
First off, Toshiba had preinstalled a 30-day trial of McAfee's Internet Security Suite. I've never been a big fan of McAfee's antivirus software, having seen first-hand some clunky performance and other issues in the past. Keeping an open mind, it was a good opportunity to see if they've corrected prior shortcomings. Sad to say, the new version only confirmed my concerns. Every time I used Outlook 2007 to send/receive e-mail, I saw my dual-core processors peg at 100% usage continuously. It literally brought my new Vista system to its knees. The entire system was running in extreme slow motion. At first I thought it was an Outlook problem, but the trusty Windows Task Manager pinpointed McAfee's e-mail proxy service as the culprit. Killing it fixed the problem. No, actually, spending several hours uninstalling, rebooting, and then manually removing all of the McAfee remnants in my system and registry fixed the problem. Even McAfee's special uninstaller from their web site didn't do a complete job. Let this be a lesson.
Next, I looked at both ZoneAlarm's and Norton's Internet security suite offerings. This took a bit more research, as both have produced excellent products in the past. ZoneAlarm has one of the best personal firewalls in the market, while Norton's Antivirus has never, ever, let me down. The ZoneAlarm suite now uses Kaspersky's highly-regarded antivirus, which brings it on par with Norton Antivirus. Previously, ZoneAlarm used CA's antivirus, a less impressive solution in my opinion. So how did they fare against each other in security features?
Like Norton, ZoneAlarm has a network and program firewall. However, ZoneAlarm has an added OS firewall, providing even greater protection at the operating system level. Score one for ZoneAlarm. Both provide full stealthing of ports. Both provide an option to block all traffic. ZoneAlarm provides a nice big red button for one-click blocking. Norton's "Block Traffic" feature requires you to perform several clicks and type an administrator password to confirm. Apparently they're taking lessons from Microsoft's UAC above, and this is bad. When you have an intrusion in either direction, you need to be able to kill all traffic quickly and easily, so ZoneAlarm easily wins this round for ease of use. Naturally, with Wi-Fi laptops, another easy way is to just turn off your Wi-Fi card, as many new laptops provide a handy off switch. Also, both suites provided anti-spyware, anti-phishing, rootkit, and wireless network protection, so those were a draw.
However, it's extremely critical to note that the ZoneAlarm Internet Security Suite for Vista is missing important features compared to their XP program. ZoneAlarm's Vista version lacks spy site blocking and blocking of confidential data. ZoneAlarm also lacks parental control, IM (instant messaging) protection, and ad blocking. ZoneAlarm's customer service explained that they were not included due to the fact that Vista and IE7 already include many of these features. While plausible, it did not excuse the most glaring omission of all: There was no adequate e-mail security. The Vista version of ZoneAlarm Internet Security Suite could not scan or repair e-mail attachments, quarantine them, or block infected outgoing messages. This was the tipping point for me.
As spam and e-mail attachments continue to be critical security threats, I opted for the excellent e-mail antivirus protection Norton provided. While the Norton Internet Security suites from 2005 and 2006 received a lot of negative feedback for being bloated and slow in scanning, the new NIS 2007 suite has been mostly recoded from the ground up. Increased scanning speed performance and reduced CPU usage were two of their main goals, and it shows. The installation went flawlessly, as did the initial scans and live updates. As for configuration, it was mostly automatic. By default, Norton Antivirus ignores all low-risk items, not something I like to see in a security program. It can be changed to prompt the user for those items, which I heartily recommend.
As further justification, I recently perused a copy of Windows Vista Magazine while killing time in an airport. They reviewed something like the top 7-8 Internet security suites including Norton, ZoneAlarm, and McAfee. They also concluded that Norton Internet Security 2007 was the top pick. While no suite is perfect, I've always liked the die-hard protection that Norton provides with virtually no false positives, easy updating of both programs and virus definitions alike, and that it just plain works. On the downside, if you should encounter a problem, Norton's customer service and support isn't what it used to be, and they tend to force you to buy new versions instead of solving problems with their installed user base. Something to consider if you aren't a power user.
FYI, Symantec has also just released Norton 360, an even more comprehensive suite that provides backup and performance tuning features in addition to the security features. While it sounds nice, all these additional features just seemed reminiscent of Norton SystemWorks -- a fairly bloated, invasive, and problematic suite for many users, and one which I strongly recommended against to friends and colleagues. Frankly, I just needed the Norton Internet Security suite features, and didn't want to overload my new Vista system with potential bloatware. Norton 360 may indeed prove to be a valuable package, but I emphasize the word, "prove", before recommending it.
Concluding Thoughts:
As you can see, Microsoft has beefed up security in Vista and IE7 to some extent. How effective these new features are, well, that remains to be seen. I still recommend installing a separate security suite with good firewall, antivirus, anti-spyware, and other features to more fully protect your system. Yes, they cost a little more, but they're worth it.
BitLocker hard drive encryption sounds promising. As faster dual- and quad-core processors and faster hybrid hard drives (those with added flash memory) hit the market, we may indeed see a mobile data security solution with reduced performance lag. For once, I'd love to read this headline: "Laptop with Critical Data Stolen -- Encryption Saved Company, Customers, and Employees From Yet Another Identity Theft and Data Privacy Fiasco." However, I have to wonder why Microsoft omitted BitLocker from other Vista versions that will obviously be installed on business and personal laptops? It just seems to lessen their stance on security by making it subordinate to profitability.
Overall, I like the attention on added security. I think that over time, with additional service packs and updates, Vista will surpass XP's popularity -- particularly as newer and faster hardware will put its performance on par with XP.
April 05, 2007
On the Ball with Vista
Thanks to Dennis Kennedy commenting on my last post, I came across the link to Craig Ball's Vista overview. As usual, Craig does a great job of walking the uninitiated through Vista's enhancements and their impact on EDD. Of course, Craig left me feeling like I just took a trip though Willie Wonka's Chocolate Factory with a rockin' Stones soundtrack. (Did you really want to know what the Vista Oompa Loompas are doing with your data?)
I also mention it since it supplements my comment about considering encryption pros and cons. He introduces the new BitLocker encryption in Vista's Enterprise and Ultimate editions and the challenges it presents.
Posted by Jeff Beard | Permalink
April 01, 2007
Vista Shadow Copies -- Helpful to Users, Even More to EDD Recovery?
Microsoft has billed Vista as their most secure operating system to date. However, there's a little-known feature that could cause some data security concerns. Amidst the flurry over EDD and the new rules, Microsoft included a feature to certain versions of Windows Vista that may aid in recovering prior versions of files.
From Microsoft's Vista site:
Have you ever accidentally saved over a file you were working on? Accidental file deletion or modification is a common cause of data loss. Windows Vista includes a useful innovation to help you protect your data: Shadow Copy. Available in the Ultimate, Business, and Enterprise editions of Windows Vista, this feature automatically creates point-in-time copies of files as you work, so you can quickly and easily retrieve versions of a document you may have accidentally deleted. Shadow copy is automatically turned on in Windows Vista and creates copies on a scheduled basis of files that have changed [...] It works on single files as well as whole folders.Very helpful indeed. There have been a number of occasions over the years when I've accidentally replaced a file when I should have saved it as new one with a different file name. We've all been there.
However, now consider the difficulty in trying to rid a system of shadow copies for legitimate security and confidentiality concerns. A laptop user may need to work on a confidential file while traveling. Since laptops are easily stolen, accidentally left behind, etc., it may be desirable to wipe the file later to maintain security and confidentiality. Consider some of the recent news stories covering thefts of laptops containing considerable amounts of personal data. It's a good bet that most file wiping utilities can't handle wiping the Vista shadow copies, at least not yet anyway.
Note that Shadow Copy is enabled by default in Vista Ultimate, Business, and Enterprise editions. So if data security and confidentiality is paramount to file recovery, organizations should consider disabling this feature in their Vista rollouts. On-the-fly encryption is another consideration, recognizing it has pros and cons as well.
[P.S. Seeing as I'm posting this on April 1st, I thought I'd emphasize this information was gathered directly from Microsoft's site. Also, Ars Technica has a post on this from as far back as last summer. Now if you're looking for an April Fools gag, Google got their hands dirty this year with Google's TiSP Beta. More on the gag at USA Today.]
Posted by Jeff Beard | Permalink
April 18, 2006
NextGen Security Threats
News.com has an interesting article on what the next security threats may be. Botnets and phishing are featured prominently, as intruders are becoming more interested in the money angle than just seeing if they can cause some mischief.
In another News.com article, rootkits are on the rise per McAfee.
Frankly, I was expecting something much sexier and well, "nextgen". However, I think stealthier, and thus perhaps more persistent, system level intrusions will be the norm for awhile, as remote manipulations provide very powerful and useful tools.
April 10, 2006
iPod Used as an Identity Theft Cache -- Only the Beginning
The San Francisco Chronicle reported yet another use for iPods: storing lots of stolen identity-related information. iPod users have known for quite some time that they can be used as portable storage for computer files, just like a thumb drive. Perhaps more troubling than a criminal using it that way is that the San Francisco police sounded surprised and considered this novel -- and that was the fraud division. They got their man through a sting operation, though, and I'm glad to hear it given the details of the identity thefts and other crimes perpetrated.
But it underscores the need for law enforcement and security professionals to consider new uses for everyday tech tools and gadgets, especially when theft of data with iPods is nothing new. As the Tech Law Prof Blog correctly pointed out on this issue, at least four years ago we learned that one could walk up to demo Macs in stores, plug in an iPod, and copy entire software programs for use on other Macs. I remember reading about this on Wired.com ("Have iPod, Will Secretly Bootleg") at the time. So why is this considered something "new"?
With all due respect to our police departments (I mean that sincerely), it sounds like they would benefit from a "Tech Culture 101"-type class. Give them some freebies to go play with -- iPods, thumb drives, camera phones, Treos, BlackBerries, Bluetooth devices, digital cameras, flash cards, etc. Show them how they work, how they capture, store, and transfer information, and perhaps most importantly, how easy it is to hide information on them "in plain sight". I hate to say this, but "you gotta think like a teen".
For example, it would not surprise me to hear one day very soon that someone was caught smuggling confidential information on one of the tiny flash cards inserted into innocuous-looking devices like a cell phone or a PSP (Play Station Portable). In fact, the PSP is quite a useful computer in its own right, well beyond playing games. Heck, you can already remotely control your home with it, not to mention all of these cool uses. Sony is also empowering it with the LocationFree console to stream all kinds of digital media to your PSP at any hotspot.
There's also a new project for porting Linux over to the PSP. As any hacker knows, once you've got Linux running on a capable device with Wi-Fi (yup, it's a Wi-Fi Finder too). . . well, it doesn't take much imagination, does it? Now that makes toting stolen info on your iPod très passé.
Posted by Jeff Beard | Permalink | Comments (0)
April 08, 2006
Why IP Phones (VOIP) Needs Encryption
On Wired News, crypto expert Bruce Schneier sums up why encryption is a necessary ingredient for VOIP usage. Here's why I'd want crypto for any VOIP solution, but I'd want it baked in as a seamless function:
I use a cable provider for Internet access, which is simply described as a neighborhood network. Although it would take some skill, who wants their neighbors being able to listen in?
Think the Government isn't listening in? Think again.
Just as importantly, sometimes I provide confidential information over the phone, such as a credit card number or my SSN -- many times when I'm asked to verify my identity. You know where I'm going with this -- criminal activity and identity theft. Bruce agrees. Organized crime has simply gone high tech, although a single hacker can also do a lot of damage with identity theft.
Per Schneier: "My greatest worry is the criminal attacks. We already have seen how clever criminals have become over the past several years at stealing account information and personal data. I can imagine them eavesdropping on attorneys, looking for information with which to blackmail people. I can imagine them eavesdropping on bankers, looking for inside information with which to make stock purchases. I can imagine them stealing account information, hijacking telephone calls, committing identity theft. On the business side, I can see them engaging in industrial espionage and stealing trade secrets. In short, I can imagine them doing all the things they could never have done with the traditional telephone network.Now, as Bruce said later in the article, it's important to recognize that crypto is not a panacea. I'm guessing it probably won't stop SPIT (SPam over Internet Telephony) should it become a larger concern. But it could make it that much harder for someone to eavesdrop, which is both a deterrent and an incentive to go after easier targets. Just as long as it's not just encryption for encryption's sake.This is why encryption for VOIP is so important. VOIP calls are vulnerable to a variety of threats that traditional telephone calls are not. Encryption is one of the essential security technologies for computer data, and it will go a long way toward securing VOIP."
Along those lines, Phil Zimmerman (of PGP fame) has just released the public beta of Zfone, an encryption tool for VOIP. I used PGP for e-mail back in the 90's. While effective for use with a small number of people willing to configure and learn it, it was just too burdensome for many others. While I applaud Phil's efforts, it will be interesting to see if Zfone will be easier to use and ultimately adopt. Regardless, consumer-facing VOIP still needs shoring up in the security department, beyond encryption, but still has to remain easy to use.
April 02, 2006
Jigsaw & Web 2.0: The Return of Privacy Concerns
As a market trend, Web 2.0 has been getting a lot of buzz, particularly on the social networking slant. Voluntary social networks such as LinkedIn have enjoyed a lot of success (at least in mindshare and user volume, anyway). I've long considered blogging to be a form of networking, and of course Wikis too, especially in the collaboration department.
While Web 2.0 is many different things to many people, one could say that social networking and collaboration are rivers that run straight through it. The main idea has merit: Lots of people contributing their individual knowledge to the whole to create something bigger and more useful than just the sum of its parts. Sounds great, doesn't it?
But just like Web 1.0 in the 90's, along comes something that gives one pause as to what direction the Brave New World will take. Back then, it was emerging privacy concerns from web usage tracking, and plans to link online and offline activities and data (DoubleClick, anyone?). For better and worse, Commercialism invaded the pure collaborative energy of the Net, and things began to take off in a different direction. Spambots, adware, spyware, and other controversial technologies came into existence and changed our online experience, probably for a long, long time.
Most recently, Jigsaw seems to fated to play the role of the privacy heavy. The WiredGC's post, "Hold on to Your Business Card", links to TechCrunch ("Jigsaw is a Really, Really Bad Idea") to get recovering attorney Michael Arrington's savvy take on it. Adding my own opinion, that makes three technically-inclined and informed attorneys who think this is a bad idea. The posted comments at TechCrunch are also a good read.
Basically, people are being paid $1 per business contact they upload into Jigsaw's online database, whether the referenced individual likes it or not. This service aims to provide salespeople, recruiters, and marketers with inside contact information they can't obtain (or as easily obtain) elsewhere. The tagline on the home page states, "Buy, Sell and Trade Business Contacts".
While one can easily see the value proposition, thus far it sounds like there is no way for a person to delete their originally-uploaded information. One can only annotate it, and that's a big difference. This lack of "Opt Out" mechanism runs counter to commonly accepted data privacy principles. One could also dive into a discussion about the business ethics and why an "end justifies the means" rational is usually a slippery slope. I note with mixed feelings that I found my contact information in their database, and if given the option, I'd probably remove it. Again, most of the comments posted at TechCrunch were resoundingly negative.
Thus If Jigsaw wants to play in the Web 2.0 sandbox more for than a brief stint, I seriously suggest they learn to play nice with others' data. Public opinion, particularly in the blogosphere, can make or break a startup, and it would be unwise for them to ignore this reality, even if this generates a "buzz". To me, Web 2.0 is about voluntary collaboration. I could see where some may want their business contact information available, say for new business development opportunities or recruitment. Others may view it much more darkly, and that's their prerogative. For a good discussion of these issues, see Release 1.0's article "Anti-Social Networking", which interestingly I found linked on Jigsaw's site.
In my mind, Jigsaw needs to better sort out the puzzle they've created, and fairly soon. They need to better balance the competing interests. Most importantly, providing an easy and visible Opt Out option should ease some of the tensions and perhaps build back some of the lost goodwill and integrity. Even better: Send an e-mail notification to each person when their contact information has been uploaded to Jigsaw, and give them the option to correct or delete the information. Then Jigsaw could truly boast they have the most accurate information, since the contacts themselves would correct it. Now that sounds much more like Web 2.0 to me.
March 18, 2006
Enhancing Mobile Security - Feature Article
Organizations usually focus more heavily on protecting the castle by fortifying its defenses. However, mobile technology security can be a bit more challenging, in no small part due to the plethora and complexity of devices, user mobility, and increased risks outside the firewall. Sometimes it doesn't receive as much attention, or perhaps is perceived as less securable. Thus I've recently written a feature article on effective mobile security techniques, strategies, and policies, entitled "Enhancing Mobile Security". The downloadable PDF is compatible with Acrobat 5 or higher.
This was originally published as the cover feature in the February/March 2006 issue of Law Office Computing. I am greatly honored by Amanda Flatten, LOC's Editor and Publisher, for granting me permission to publish it here. Amanda, you're the best. If you're in the legal field and have any interest in improving your practice via savvy use of technology and keeping abreast of new developments, then I highly recommend a subscription to LOC.
Posted by Jeff Beard | Permalink | Comments (0)
March 11, 2006
80 Super Security Tips
PC Magazine has done the world of average PC users a favor by publishing 80 Super Security Tips in fairly understandable language. While it was published some time ago, it's still darn good advice that's actually usable -- besides, where else are you going to find 80 very good security tips in one place that isn't a load of geek-speak?
February 19, 2006
New Google Desktop: Configure It Carefully, or Forget It
I've been meaning to post this: That's the warning from the EFF, as reported in The Register. I know many people think Google Desktop is the coolest thing for personal info management, but I've previously posted my concerns here. It just keeps getting more complicated for maintaining control over your personal data, unless you are very committed to learning exactly what the software does and knowing what escapes out through your firewall.
Thus one should question using a number of these free tools. It's not paranoia when others have confirmed it. If you do, then in addition to the configuration suggestions, see if you can configure your software firewall to block all its traffic requests, particularly outgoing traffic to try to limit its phone home capabilities. If you don't have a firewall that can block outgoing traffic by software program, get one, pronto. It never hurts to add a second layer of protection, but don't rely on any single precaution as absolute.
It also makes me wonder about the effect on client confidentiality when used on a PC with access to sensitive documents and other data. Even if the privilege isn't waived, if one is representing a client with questionable or confidential activities, then you aren't exactly helping to keep them confidential with tools such as this, right? It's a bit difficult to unring the bell, food for thought. Not professing any legal advice, just good old-fashioned common sense. Let's be careful out there.
January 15, 2006
Anonymous Online Annoyances Outlawed?
You may want to read this CNet News.com editorial, as this post will make more sense if you do:
Perspective: Create an e-annoyance, go to jail
By Declan McCullagh
Published: January 9, 2006, 4:00 AM PST
From the article:
"Annoying someone via the Internet is now a federal crime.Note there's apparently a mens rea or intent component. Otherwise, this would end up as yet another anti-spam law (who doesn't find spam quite annoying?). One thought occurred to me about anonymous blogging: What if something is posted anonymously that others may find annoying?It's no joke. Last Thursday, President Bush signed into law a prohibition on posting annoying Web messages or sending annoying e-mail messages without disclosing your true identity.
In other words, it's OK to flame someone on a mailing list or in a blog as long as you do it under your real name. Thank Congress for small favors, I guess."
Even if the blogger is ultimately proven innocent, one could still be charged and would have to defend against it to show there was a different intent. I've always thought anonymous blogging was a fairly bad idea -- it's only a matter of time before your identity is discovered, and you'd be instantly accountable for all of your online remarks (just ask the recently unveiled "Underneath Their Robes" blogger, who was, ironically, a federal prosecutor). This could also put a serious chill on free speech, as there could be very good reasons why someone would want to post anonymously for fear of reprisal. Yes, there is prosecutorial discretion, but how well does that spell out the boundaries for us?
Here's a much more common occurrence I see nearly every day, especially in online forums and comment sections: Flame wars or biting remarks directed to another poster, usually resulting in a long, drawn out thread comprising numerous posts (i.e., not just a single passing flame). Many times they are the result of miscommunication and/or different perspectives, some are emotional knee-jerks, but others are just downright nasty. In many forums, participants use screen names, nicknames, aliases, etc. to protect their identity for legitimate reasons. Heck, many people don't post their real e-mail address just so they won't be spammed by spam bots. Will this become the anti-flame law? The "Let's just all get along online" law?
Yes, some cases of online harassment will likely be quite clear due to the pattern, number of incidents, content, etc. In others, well, it's rather like the old Tootsie Pop commercial: How many biting retorts does it take to get to the center of intent? Don't get me wrong, as I've received an e-mail or two from people who related an online harassment incident -- it's scary and it's real, and they would likely be the first to applaud such a law if it did them any good to prevent cyberstalking and harassment. Thus I like the underlying idea, which seems to mirror the telephone harassment laws, but where does one draw the line?
It also doesn't bode well when a law has to be piggybacked on another bill politically, just so no one would shoot it down. One wonders: how well would it have stood on its own? So despite perhaps some good intentions (pardon the pun), I think this is yet another Internet-related law that will be challenged on Constitutional and other grounds. I think I'll stick with the age-old parental advice, "If you can't say anything nice..."
January 02, 2006
Mighell on Metadata and User Error
Tom Mighell has a great reference post on Inter Alia that links to several informative metadata articles, including discussions of ineffective PDF redactions. Be sure to check out the comments following the Washington Post article, as it features an interesting post by none other than the metadata diva, Donna Payne.
December 07, 2005
IE Flaw + Lax Google Desktop Security = Very Fast Phishing
Now here's a very clever hack, using your own software tools against you:
Phishing with Google Desktop
The Register
Published Saturday 3rd December 2005 01:24 GMT
IE flaw lets intruders into Google Desktop
CNET News.com
Published on ZDNet News: December 2, 2005, 1:31 PM PT
From CNET:
"This design flaw in IE allows an attacker to retrieve private user data or execute operations on the user's behalf on remote domains," Gillon wrote in his description of the attack method. He crafted a Web page that--when viewed in IE on a computer with Google Desktop installed--uses the search tool and returns results for the query "password."The security researcher who found it is recommending the use of alternative browsers, such as Firefox and Opera, to be safe. Until a patch is developed, you may not want to use IE if you have Google Desktop installed. At least be very careful about which sites you visit, as the exploit requires a specially crafted web page.
From the articles, the flaw is in definitely in IE, but Google isn't above reproach: The Register reports, "The weight of responsibility for this flaw falls on Microsoft. But Google shares some blame too, for failing to take the integrity of your personal data seriously." "...this particular flaw wouldn't have been possible without careless programming by Google, which amazingly, fails to obey the Google Desktop security model on its own site."
Of course, other search phrases are possible. Call me a rebel, but it's times like these I'm thankful I've resisted the strong urge to install some of these free goodies, for exactly the privacy and security concerns that have abounded since a number of free desktop enhancement tools have been released in recent years. Yes, it's mainly an IE flaw, and desktop productivity software has its uses, but I've always thought it a good idea to be a bit leery of anything that wants full access to all my personal files and e-mails and is Internet-enabled. Today, it's IE and Google Desktop. Tomorrow, it'll be something else, but I guess that's what keeps it interesting.
October 09, 2005
Public PCs Expose Confidential Information
Here's something to consider before you use a "convenience" PC at an airport, hotel, or other public place:
"Airport PCs stuffed with meaty goodness"
The Register, Sept. 25, 2005
Even if you just use a public PC to check e-mail, at the minimum you're probably risk the following (particularly as the average user doesn't clean up their information afterwards):
- Leaving behind a cached copy of e-mail messages.
- Unopened attachments are iffy, depending on the e-mail client's method for working with attachments -- but if you open one, there's very likely a local copy left behind.
- Having a keylogger or other piece of malware record your login name and password, and anything else you've typed on that PC, including e-mail replies. These types of programs often transit this information to another web site or server via the Internet.
- Even if no malware is present on the PC, you may still be leaving cached copies of this information, as well as cookies, completed web forms, etc.
- Assume the PC is not safe, and has already been compromised.
- Assume everything you access from that PC will be compromised in some fashion from tracking your actions, so only access the minimum necessary.
- Assume installed keyloggers will record and transmit everything you type, including e-mail replies, login names, and passwords, so exercise extreme caution (general web surfing to open sites is okay).
- Remember that encryption (e.g., VPN) isn't much protection if your keystrokes are recorded.
- Learn how to properly clean up after yourself, which includes:
- Clearing the web browser's multiple caches for web pages, passwords, forms, history, cookies, and other information But clearing these items can't unring the bell if a keylogger was installed, as your information is now in another's hands -- clearing these items just helps prevent later users from accessing the information from the PC.
- Deleting files and emptying the Trash or Recycle Bins (but remember, deleted files can recovered using special programs)
- As soon as you gain access to a secure PC afterward, change your passwords.
September 21, 2005
Opera Browser: Now Free & Why You Should Care
The Opera 8.5 web browser just became free, offered without the ads. As Opera's site is fairly scarce on details, BetaNews and CNet provide a few more tidbits as to why Opera is now offered without ads, licensing fees, or registration. (Premium support is still available at $29 per year.)
Interestingly, the timing could be fortuitous, given this CNet article published two days ago: "Symantec: Mozilla browsers more vulnerable than IE". (Yes, that's not a misprint.)
According to CNet's summary of Symantec's Internet Security Threat Report, "25 vendor-confirmed vulnerabilities were disclosed for the Mozilla browsers during the first half of 2005, 'the most of any browser studied,' the report's authors stated. Eighteen of these flaws were classified as high severity. 'During the same period, 13 vendor-confirmed vulnerabilities were disclosed for IE, eight of which were high severity,' the report noted." [...] "There is one caveat: Symantec counts only those security flaws that have been confirmed by the vendor."
With this said, Symantec adds that only IE has experienced "widespread exploitation" so far, but "expects this to change as alternative browsers become increasingly widely deployed." In other words, IE is just more squarely within hackers' sights -- at the moment.
The article goes on to cover the Secunia statistics for the browsers. Secunia is a well-known security monitoring company that tracks security issues of various applications. Just to provide a more apples-to-apples comparison between IE, Mozilla, and Opera, I looked up the latest version of each browser to see how many Secunia "advisories" (i.e., security risks, exploits, etc.) were reported for each. As of today, Opera indeed appears to fare the best among the three, and Mozilla doesn't look so bad with just a few outstanding issues (although "none" would be better):
Total Secunia Advisories (I believe these are cumulative):
| IE 6.x: | 85 |
| Mozilla Firefox 1.x: | 23 |
| Opera 8.x: | 8 |
Total Unpatched Secunia Advisories (these are the ones to worry about):
| IE 6.x: | 19 |
| Mozilla Firefox 1.x: | 4 |
| Opera 8.x: | 0 |
Over the past several years, I haven't been a big fan nor user of Opera, namely for these reasons: I don't like ads or anything remotely related to adware, nor did I want to pay for a web browser when good free alternatives existed. Also, some web sites didn't display properly in Opera (although the same could easily be said for Mozilla-based browsers as well).
However, given that Opera is on version 8.5 and was more commercially developed compared to Mozilla's open source efforts, one could make a very good argument that it's more mature and has more built-in features. Mozilla requires many third-party plug-ins to achieve its functionality. One area I've always thought Opera was a leader was its mouse gestures for quick navigation -- a great feature that once you master, you don't want to use a browser without. And, as a market trailer, it's far less likely that hackers would find any meaningful return in their efforts to exploit it. That could change now that it's free, as there's a lot to like.
Is it too late for Opera to compete in the browser wars? Hard to say. Fairly recent surveys show people are much more aware of security issues relating to Internet use (adware, spyware, browsers, spam, phishing, etc.). People like choices. People like free choices even more, especially if it's a good product and the pain to change over from a competitor is fairly low. I do think that by now, most people have "settled in" with their browser of choice, and don't want to migrate their bookmarks/favorites yet again. However, there are many who always want to try the latest and greatest, and I have no doubt they are already downloading Opera, willing to give it a whirl.
After Microsoft has dominated the browser scene for so long (amazing considering its lack of releases to keep pace), it's nice to see the pendulum swinging back the other way.
August 19, 2005
Zotob & Security Best Practices
With the rapid spread of the Zotob virus and its variants this week, I thought I'd direct others to my comprehensive article on making your personal wireless network more secure: "Wireless Networking Best Practices: Version 2.0".
Why? Because the vast majority of home and SOHO (Small Office/Home Office) wireless networks are notoriously insecure by many estimates. The tips contained in this article provide critical defenses to the techniques and mechanisms used by Zotob and its variants.
By some reports, even if your version of the Windows OS cannot be infected by Zotob, the virus may still run on it as a host. This effectively turns your PC into the electronic equivalent of Typhoid Mary, so it can seek out and infect other unprotected PCs.
Please also note the article's section on disabling the UPnP (Universal Plug 'n' Play) feature of your router. UPnP is the main exploit used by Zotob. A year ago, I stated: "UPnP is used for some devices like the Xbox game system. If you don't have a UPnP device, then make sure it's disabled. Otherwise, it's another potential security hole for your network." For instance, I noticed that some versions of Linksys' wireless router firmwares left the UPnP feature enabled by default where previous versions had it disabled. This, in my opinion, was a bad decision by Linksys. Leaving UPnP enabled in the router may have been required for gaining the Microsoft Xbox certification. However, it's still a really bad security decision considering that many people using those routers don't have an Xbox or use the UPnP feature.
Anyway, I hope you find these security best practices helpful. All of the information is still current and valid.
August 05, 2005
Hotel Systems Hackable Through Room TV's
Just when you thought others hacking into your hotel room's Wi-Fi access was annoying, here's one to up the ante: "Hacking the hotel through the TV".
Basically, a knowledgeable person can hook up a laptop with a USB TV tuner and hack into hotel systems that expose other guest information.
Speaking about Adam Laurie, who presented this at the recent DefCon event, the article states: "He can't look into their rooms (yet), but depending on the system he can see what they are watching on their TV, look at their guest folios, change the minibar bill and follow along as they browse the Internet on the hotel television set. To tease his fellow guests, he can also check them out of their room and set early wake-up calls via the TV."
If that wasn't bad enough: "And the situation isn't getting better. 'They are starting to do things like allowing you to put credit card numbers in through the TV,' Laurie said. Also, he said, some of the makers of these hotel systems are looking at adding Webcams, perhaps to let people chat over the Internet." Now doesn't this sound just like, oh, I don't know, Big Brother watching people via television in "1984"? Life imitates art.
He can do all this because of the "inverted security model" of these types of systems. Per Laurie, "The TV is controlling which content I get to see. The hotel in most cases is streaming all content without any control." Talk about a dumb terminal. So he substitutes his own laptop-based TV as the control mechanism to hack the content. He also uses a special infrared remote to hack the remotes codes used to communicate via the TV. (He obviously has waaaay too much time on his hands, but what's a hacker to do when he's bored and stuck in a hotel room?)
So on your next stay, cover up or unplug any courtesy webcams (and their microphones if they have them), don't enter any sensitive data into the TV, and be aware of all your activities through your room's TV. Don't feel strange about doing so -- you're not being paranoid if others are actually accessing this data. For similar reasons, I haven't used public or kiosk PCs in ages due to keyloggers and other spyware.
Hey, after all these years, there's finally something good on cable TV -- your personal information. As Dana Carvey would say, "Now isn't that special?"
July 28, 2005
Tech Tip: ICE Your Cell Phone for Emergencies
Now here's a tech tip that could help you in an emergency: Most accident victims carry no next of kin details, yet most carry a mobile phone. Should you be injured or otherwise incapacitated, consider adding one or more ICE entries to your cell's phone book. ICE stands for "In Case of Emergency", and many paramedics are trained to look for ICE entries. The emergency medical team can use them to call others to notify them of your condition. You can use "ICE1", "ICE2", etc., or "ICE - Sue", "ICE - Jim", etc. For more information, see the ICE web site.
On a similar note, I've added "Call if Found" entries for many years in my cell's contact list, although for a different purpose -- recovering my cell phone when I lose it. It's happened twice over the past few years, and both times someone called me to return it.
As you'll want these entries to be conspicuous, don't bury them in a long phone book list. Force them to the top. Since many devices sort the phone book entries alphanumerically, you'll probably need to place a special character at the beginning of the contact name. I prefer to add a period (.) as it's unobtrusive, such as ".ICE1" or ".Call if Found 1". If this doesn't work, you can try other characters or simply prefix ith with one or two "a's".
Note: If you've already added the same phone number as a separately named entry (e.g., Jim's Home), you may notice some substitution in your Caller ID and call lists -- especially if these new entries are sorted first as recommended. Where you used to see "Sue's Cell" or "Jim's Home" on your incoming call display, you may see "ICE1", "ICE - Sue", or "Call If Found 1" -- depending upon what you entered.
Unfortunately, some or all of this information could also be used to assist identity theft if the person who finds your phone is so inclined. Thus you may want to limit the amount of personal information listed. Most definitely, notify your ICE contacts that you've added them and provide them with additional instructions, such as a list of people to contact on your behalf. Also counsel your ICE and trusted contacts to be careful not to give out any truly sensitive information, even during the initial shock of hearing bad news. In this regard, I'd suggest telling them to gather as much verifiable information as possible from the caller, including name, address/location, and phone number.
Lastly, I just read "E911 is a Joke" in the print edition of the August 2005 issue of Mobile Magazine. The gist is that E911 (Enhanced 911) has a ways to go yet, as the author states it's common for cell phones to have trouble reaching 911 for several reasons. From the article:"Most major wireless carriers have long since complied with a federal law requiring cell phones to transmit location-based data to emergency call centers, which would make it easy for the authorities to find you if you need help. But that's only half the equation. Enhanced 911 (E911) data is worthless if the emergency center that receives your call lacks the technology to do anything with it. And sadly, most do."
Basically, it goes on to state that when some call centers are overwhelmed by volume, they just forward the calls elsewhere, so you may be bounced from center to center. So while E911 is a great idea, it's probably a spotty solution for the near terrm. I'd like to see the same push directed at the carriers and phone manufacturers to be focused on the local call centers, so we can eventually have a much more reliable and effective solution.
Posted by Jeff Beard | Permalink | Comments (0)
July 22, 2005
Your Cell Phone Records for Sale Online
Yet another disturbing development in the erosion of privacy in this digital age: For just over $100, others can obtain your last 100 outgoing cell phone calls from your last billing cycle. All they need to provide is your name, address, and cell phone number. The Washington Post just covered this in "Online Data Gets Personal: Cell Phone Records for Sale".
These services are available online, making it even easier to get the information, and more quickly. Since the call records are maintained by the phone companies, the article discusses the legality (or lack of it) of these practices and services. Regardless, it's happening.
July 11, 2005
How Good is Your Spyware Scanner?
This timely PC World article warns that various spyware scanners may intentionally stop detecting various adware programs. It's not because of any technical deficiency, but because adware companies are getting aggressive about being "delisted".
Delisting occurs when an antispyware developer removes a particular adware program from its detection database. At that point, it may not detect the program if it's installed on your PC. So why would anyone do that? Per the article: "Some adware companies, arguing that their software is benign, have petitioned anti-spyware firms to stop warning consumers about their software. Other companies have resorted to sending cease-and-desist letters that threaten legal action."
The real problem is that we users generally can't access the detection database, and won't be notified that a particular program has been delisted after a software update. While there could be good reasons for delisting (e.g., an adware developer cleaned up its software to be far less intrusive), there will have been a certain reliance built up over time on a particular spyware scanner's effectiveness. Also, while a particular adware developer may have cleaned up new versions of their software, prior "nasty" versions could still abound on a number of web sites, and be downloaded. Will the spyware scanner distinguish between the versions and protect against them?
Even Microsoft has been in the news today (even Slashdotted) about how Microsoft AntiSpyware downgraded the threat level of Claria's software (formerly known as "Gator" -- yes, that Gator). Here, Microsoft has the appearance of a conflict because of reports and speculation that it is looking to buy Claria. Others doubt this will really happen. Whether or not Microsoft acted appropriately is certainly clouded by the circumstances and timing. However, it illustrates how sensitive and controversial the issues have become.
These issues aren't new. Similar problems cropped up with how sites have been categorized in content blocking software, aka "censorware". Among other things, this type of software blocks young family members from accessing questionable sites. While certainly useful, it also had some questionable results. See The Censorware Project for more info. From time to time, various other sites would get caught in the "censored" net. That is, they'd be added to the list of blocked sites for having controversial or critical information posted. Some were allegedly blocked primarily because they dared to criticize the companies doing the blocking. I believe lawsuits ensued.
Regardless, the various content blocking, antivirus, and antispyware products work because we end users trust someone on the development side to find, block, and/or remove the "bad stuff". The problem is that determining exactly what is the "bad stuff" is somewhat subjective, and requires a judgment call. Sometimes it's also influenced by "cease and desist" letters and legal threats. Some may be legitimate, and others basically bullying tactics. Depending on the ability and determination to withstand such pressures, some spyware scanner developers may delist where others do not. Thus I'd advise utilizing several antispyware programs to have more complete coverage and mitigate your risk.
Obviously, antispyware developers now have more to worry about than the latest adware program. And, as a result, so do we.
June 03, 2005
Beware Electronic Horses Bearing Trojans
Industrial espionage is alive and well in Israel, according to the Jerusalem Report. Major companies were implicated, both on the spying and victim sides of the fence. Among the methods used by the spying private investigators was a Trojan horse. "The private investigators, police suspect, would send the virus hidden inside a promotional CD to various companies, which unknowingly uploaded the Trojan horse onto their computer system. The private investigators would also send emails to the various companies with the virus as an attachment, police said."
So be careful what you click on in your e-mails, particularly attachments. If you weren't expecting it, don't open it. Just delete it.
Overall, a very disturbing chapter at the intersection of business ethics and business intelligence (the latter ultimately an oxymoron in this case).
May 23, 2005
Using eBay to Locate Stolen Goods
Who says you can't take a bite out of crime online? How about this for a cool electronic discovery, thanks to some clever thinking:
"Burgled mum finds stolen iPod on eBay"
At least she had a personally-identifiable iPod. It's getting so bad regarding iPod theft that one might consider a Kensington MicroSaver-type cable for it. ;^) Just in case anyone still thinks those cables are effective, check out this video (link courtesy of Gizmodo) which shows how to pick the lock in seconds flat with a cardboard toilet paper tube. Yep, that's what I want protecting my laptop. Right up there with the Kryptonite Evolution 2000 U-Lock, pickable with a ballpoint pen.
Where there's a will and cheap household items for the use...
March 22, 2005
VOIP Insecurity & Caller ID Spoofing Are Enough to Make You SPIT
If you have a perverse desire to increase your anxiety level, then you'll love Wired's report on "Scammers Snag Money on Net Phones". Internet telephony, also known as VOIP (Voice Over Internet Protocol), has some serious security challenges.
I've previously posted about the issues surrounding Caller ID spoofing over regular phone lines. With Internet telephony, the virtual phone lines are subject to hacking just like the rest of the Internet.
If you thought spam was bad for e-mail users, there is potential for a new form of spam for VOIP. It's called SPIT -- SPam over Internet Telephony. According to the FTC Chairman, in theory "unscrupulous telemarketers could use VOIP to blast huge numbers of voice messages to consumers". I immediately thought about the creation of a "Do Not Call" list for VOIP users, but then, what would be the point? Unless one could actually track down the origin of the Spitter (now there's an appropriate appellation if I do say so), it's probably not going to do much good. Look how effective the CAN-SPAM Act hasn't been.
Phishers are also getting into the act via Caller ID spoofing. Some wire-transfer services such as Western Union use Caller ID to verify that someone is calling from their home phone to validate the fund transfer. I was astonished to read that "the company has no other way to verify that transfer requests are valid."
It certainly sounds like there's a huge untapped market for anyone offering a better mousetrap in consumer-friendly identity authentication.
March 21, 2005
Tips for Identifying Phishing & Fraudulent E-Mails
Microsoft, in its battle against spam and online fraud, has a very good article describing deceptive e-mails. It covers how they work, and how you can spot their characteristics.
To summarize, many deceptive e-mails have the following attributes, either separately or in combination:
- Requests for personal information
- Urgency, such as closing or deleting your account unless you respond
- Deceptive links (HTML e-mails can display seemingly valid links, but the underlying link goes elsewhere)
- One or more images to get past spam text filters and/or phone home as web beacons
- Attachments containing all kinds of malware
- If it sounds too good to be true -- it is
Say what you will about Microsoft security, but I applaud their efforts to educate people on these attacks. Protective software and security only go so far, especially when it comes to e-mail. The rest is up to the recipients, so we need to know how to protect ourselves.
January 22, 2005
Don't Panix! Lessons Learned from Domain Name Hijacking
InternetWeek has a good article chronicling the recent hijacking of the Panix.com domain name, and the lessons learned.
It shows how the recent ICANN changes to domain transfer rules to make transfers easier and quicker has made the system more vulnerable to abuse. Apparently Panix, the New York ISP, took all the appropriate precautions in advance to protect themselves, but the hijacking occurred anyway. The amazing thing is that even with a domain lockdown in place, the "hacker took the domain with a very unsophisticated attack. The attacker simply used normal registration procedures and a stolen credit card to claim panix.com with a MelbourneIT registrar reseller."
It's a good read and offers some suggestions to protect yourself. But as this illustrates, it's still a fragile system. Even with precautions in place, I wouldn't be surprised to see this happen again.
January 09, 2005
Microsoft Now Offering Beta AntiSpyware
As I mentioned back in October, Microsoft was planning to offer antispyware and antivirus solutions, but hadn't offered any dates. Recognizing the enormity of the spyware problem, Microsoft has since acquired Giant AntiSpyware and is now offering its own beta version via downloads at the "Microsoft® Windows AntiSpyware (Beta)" download page. I've never heard of nor used the Giant software, so unfortunately I can't comment on that product's details or effectiveness. From the Microsoft download page, this was just published on January 7th, 2005.
This CNET News.com article provides much more detail, including Microsoft's quick actions to provide a beta shortly after the acquisition, and additional discussion regarding Microsoft's overall strategy and timing for offering antispyware and antivirus to its customers. I applaud Microsoft's efforts, but wonder how complete and therefore, effective, they will be. At this point, keep in mind it's a beta.
Something is probably better than nothing, as long as its users don't gain a false sense of security -- no one thing provides 100% effective security, simply because security is a process, not a product. Products are tools to implement security measures. There are a number of different antivirus and antispyware programs available on the market. If Microsoft adopts a "single solution" for each, it paints a big red target on them for the malware developers and hackers to attack and exploit, much like the built-in Windows XP firewall (which again, is better than having nothing in place, yet an incomplete solution by itself). This isn't Microsoft's fault per se, it's just that the dominant player is normally the one on whom the malware developers focus their attacks. Microsoft's security record is also well known.
At least the Microsoft name is also well known (although I've never heard of Giant), and it sounds like they are consciously trying to provide solutions which help both their customers and themselves. Other antispyware providers may not: Walt Mossberg of the Wall Street Journal offers similar advice, "Beware of antispyware programs offered via pop-up ads or e-mail spam. Some of these actually are malicious, and will install spyware and adware, rather than expunging it." So don't forget about the well-known and often-recommended spyware solutions. Lastly, it's important to recognize that many computer users are, in themselves, a weak link -- they introduce spyware and other malware to their systems by not being sufficiently self-informed, and thus are unaware of best practices. Check out my prior post, "Practicing Safe Hex", for some great ideas and linked resources. It's an eye-opener.
[Update 1.11.05: Per the comment attached to this post, check out Flexbeta's antispyware comparison review or its printable version. They put the new MS AntiSpyware through its paces, head-to-head against Ad-Aware and Spybot S&D. Their results, while quite encouraging, emphasize an often-made key point: No one antispyware program will detect and clean everything from your system. Thus you may want to consider using multiple antispyware programs to double-check your computer and catch the malware the others left behind. Also, Flexbeta indicates MS may offer their AntiSpyware on a subscription basis, so there may be a cost factor after the beta period has concluded.
In any event, it's good to know there's another antispyware option with potential, hopefully one which will also play nice with Microsoft's operating systems and applications. I found it interesting that the CNET News.com article referenced above included this tidbit: "She [Amy Carroll, director of product management for Microsoft's Security, Business and Technology unit] pointed to a compatibility issue that Microsoft experienced just after the launch of Windows XP Service Pack 2 as partially caused by a hidden spyware application." So it's probably safe to say that Microsoft is attempting to offer a win-win for both their efforts as well as those of their customers. Like antivirus solutions, antispyware needs regular updating for detecting and removing new malware. Should Microsoft charge a subscription fee for a commercial grade product, it's right in line with industry norms. It also increases its chances of being actively developed and supported. In comparison, look what happened with Internet Explorer's stagnation, which was offered for no additional charge.]
[Update 1.13.05: Walt Mossberg at the WSJ chimes in with some mixed comments on MS AntiSpyware: "Unfortunately, the company's first free security program has some serious flaws and lapses. I've been testing Microsoft's antispyware software, called simply Microsoft AntiSpyware, and I can't recommend it, in its present form, over the leading third-party antispyware program I have favored, Webroot's Spy Sweeper." He concludes, "It's good that Microsoft is finally offering users tools to protect their Windows computers. But it's going to have to do much better, and it's going to have to avoid the perception that it's using security as a tool to promote or favor its own products."]
October 02, 2004
Microsoft Planning to Offer Anti-Spyware and Antivirus Software?
Thanks to a link from Techdirt, Bill Gates may feel our pain. According to a CNet News story, Mr. Gates has experienced malware firsthand:
"This malware thing is so bad," he said in a speech at the Computer History Museum here. "Now that's the one that has us really needing to jump in." It's also a problem that has affected Gates personally. He said his home PCs have had malware, although he has personally never been affected by a virus. "I have had malware, (adware), that crap" on some home machines, he said.Sounds like he's a bit peeved. However, no news yet on when Microsoft would offer anti-spyware software:
"Gates said Microsoft will offer software to detect malicious applications and that the company will keep it up-to-date on an ongoing basis. He did not say when the software would be available or whether Microsoft would charge for it."Regarding the giant's entry into the antivirus market, the above CNet article references another back from June 2004:
"Our plan is to make antivirus part of our pay-for product offerings," she [Amy Carroll, director of product management for Microsoft's Security Business and Technology Unit] said. "But we don't have specific (antivirus) product plans right now." The comments come almost exactly a year after the company bought a Romanian antivirus firm, GeCAD--a move that set off speculation that the giant was going to turn its attention to dominating the antivirus market.My concern, and I'm sure that of many, is that Microsoft's approach to security leaves much to be desired. Would it would add value to have these solutions seamlessly integrated with other Microsoft products? Or would it be a larger security risk to put all one's eggs into the same basket? I'm not planning to abandon Symantec's excellent antivirus offerings nor effective anti-spyware products such as Ad-Aware and Spybot Search & Destroy just yet. Microsoft will definitely need to prove itself in these markets.
Best quote of the day, from Techdirt: "Anyone want to suggest BillG start using Firefox to protect himself?"
September 07, 2004
After Threats, Caller ID Spoofing Entrepreneur Selling Business
Three days, that's all it took. The Net has been rife with criticism over this new startup endeavor, which I posted late last week. From the NY Times (free registration required):
"It may be known as caller ID spoofing, but it is evidently no laughing matter.Here's the real irony: According to the article, Mr. Jepson's own privacy was severely compromised:Three days after the start-up company Star38 began offering a service that fools caller ID systems, the founder, Jason Jepson, has decided to sell the business. Mr. Jepson said he had received harassing e-mail and phone messages and even a death threat taped to his front door - all he said from people opposed to his publicizing a commercial version of technology that until now has been mainly used by software programmers and the computer hackers' underground."
"While network security consultants and some other technology professionals are known to have a cottage industry involving the use of caller ID spoofing, Mr. Jepson said the nature of the threats he had received made him conclude they had come from so-called phishers - people who use caller ID spoofing and online techniques to trick people into handing over confidential information.Yet another example of asking the wrong question. Instead of asking, "Can we?" perhaps he should have asked, "Should we?" While I think many of us would probably not condone the more extreme actions taken against him, it sounds like he got a little taste of what it feels like to be harassed by unknown callers. For some strange reason, I just don't think he's going to get much sympathy.The people who threatened him, he said, had already tapped his phone calls and had obtained details about how much money he last deposited into his checking account. 'Some people,' he said, 'are pretty fired up about this.' "
The problem, however, remains. The genie is still out of the bottle, and his business is now up for sale. I feel it's one thing if a caller chooses to block their caller ID. The recipient still has the choice whether or not to pick up the call, knowing that it may be unwanted (after all, what did we do before Caller ID?). However, intentionally forging a caller's identity plunges Caller ID into a level of uncertainty and deceptiveness that crosses the line in my book.
Gmail Gets Up Close and Personal
Dow Jones columnist Jeremy Wagstaff's Loose Wire (a great technology blog which I find myself reading more often) details a few sensitive or personal subjects Gmail appears to be culling from individual Gmail accounts -- one of the initial and continuing concerns surrounding the new controversial e-mail service.
He cites an example whereby a friend wrote another friend about her ex-boyfriend, and then saw numerous ads in her account relating to getting her ex back, a breakup survival guide, meeting a lover, and more.
Jeremy raises some interesting points:
"As my friend says, 'This is too damn scary. Going back to Yahoo.' I agree. I think Google has to draw a line here somewhere: Firstly, contextual ads should not be so clever that they know what you're cooking that night (or if they are, they shouldn't be so dang literal about offering to spice it up) and secondly, and most importantly, there has got to be a broader definition of what is considered intrusive. Figuring out from what you write that (a) you've broken up, (b) you have kids and (c) there might be a problem related to (a) and (b) is way too creepy to be helpful. Google should immediately drop any contextual ads that deal with such issues unless users specifically approve of them.Playing devil's advocate for a minute, such information could be helpful to a person in that situation. However, who feels comfortable knowing that one's personal life is being indexed and cataloged so precisely? I agree -- we need to know more, and in the meantime, err on the side of caution if personal privacy is of any concern.Then, of course, there's the issue about where this information is stored. Already a deeply detailed profile of my friend has been built up in the week she had Gmail; what would happen over a year? And how is that information stored, shared and combined? We need to know more."
Obviously, we each have a choice whether or not to use Gmail, and in providing feedback. If we don't like something online, we can always vote with our mice.
September 02, 2004
Controversial New Caller ID Spoofing Service
Here we go again. When Caller ID was first introduced, it raised numerous privacy issues. Now, just as we're finally comfortable with it, along comes new technology to disturb the status quo. According to the New York Times (free registration required), a new company called Star38 (or *38) is offering a new service which enables debt collectors, law enforcement officials, and private investigators to spoof, or fake, their Caller ID information when they call you.
The service is cheap and easy to use, and the callers can set the Caller ID telephone number and name to whatever they want. The NY Times article discusses the legal concerns involved, including the Fair Debt Collection Practices Act. Engadget, one of my favorite tech blogs, recently had an interview with Star38's CEO and included photos of the service in action. Star38's sparse information is found here.
The following from the Times article is an eye opener:
"The developers of Star38, who say they required only 65 lines of computer code and $3,000 to create their service, insist that they will take steps to ensure that it is not used maliciously. They plan to spend up to 10 days checking the business licenses of all applicants and will ask subscribers to agree not to use Star38 to commit fraud, and to accept legal liability if they violate state or federal laws."It will be interesting to see how effective asking subscribers not to commit fraud will be. It doesn't give me any warm fuzzies. It certainly wasn't good enough for the RIAA in the 321 Studios lawsuit, wherein the controversial DVD X Copy software asked its users whether the DVD being copied was borrowed or rented. Granted, that was primarily a DMCA suit, but you get my point.
Initially, the service will only be offered to the above types of customers following some type of background check, but not the general public. On this point, per the Times article:
"The company also plans to cooperate with police forces, if asked, to provide records of what numbers customers dialed to and from, and what numbers they chose to show the recipients of their calls.In the immortal words of George Carlin: That's what scares me."Law enforcement will have complete access to search our database," said Jason Jepson, the chief executive of Star38, of Newport Beach, Calif. "We don't want the insinuation that they can sign up, use it temporarily and then run off."
Mr. Jepson, 30 - who says he got the idea for his service after speaking to his aunt, a bounty hunter, about the best ways to get in touch with people - said Star38 had no immediate plans to sell its service to ordinary consumers because of the potential for misuse. "There are too many things that can go wrong," Mr. Jepson said.
But industry experts say that the caller ID spoofing, as it is known, is simple enough to develop that it is only a matter of time before other service providers make it available to anyone."
August 31, 2004
Crypto-Guru Bruce Schneier on IT Threats
Just after I posted regarding IE and malware, I came across this interesting Bruce Schneier interview at Neowin. Bruce is a well-known cryptologist and security expert, and I've read his informative book, "Secrets and Lies".
As you can tell from my prior post, I heartily agree with Bruce, particularly on this point:
"What do you see as the biggest threat in the IT age?Regarding the ultimate responsibility for security:People. Since the beginning of time, people have always been the biggest security threat. That hasn't changed because of computers. People are why firewalls are invariably misconfigured. They're why social engineering works. They're why good security products are rarely deployed properly. Securing the computer and network is hard, but it's much easier than securing the person sitting on the chair in front of the monitor."
"If you were to look at 3 areas - The Software Designer, The Systems Administrator, The User - who would you say should bear the burden of responsibility for security? Or do you perceive it to be a shared responsibility?Again, this illustrates my point about users simply not knowing any better while contributing to the problem. But that's reality, like it or not. Some may take the initiative to better protect themselves (especially after getting burned at least once), and others won't. While there's a lot of self-help available online (you know it's bad when WSJ's Walt Mossberg covers spyware this month), it only goes so far. When it comes to security, people are often the weakest link in the chain. Just ask this law firm whose longtime bookkeeper fell prey to a Nigerian e-mail scam to the tune of embezzling $2.1 million. The breach in security wasn't just the person who embezzled the money, but also the management under which it occurred, and the bank manager who approved all of the wire transfers even though the bookkeeper was not authorized to make such transfers. I also recommend reading Sharon Nelson and John Simek's enlightening article on "Disgruntled Employees in Your Law Firm: The Enemy Within". Please don't misunderstand this as a "down on people" tone, as I can assure you it's not. It's about recognizing some of the root causes for security breaches and thereby being better prepared as a result. For example, "social engineering" preys on our fundamental tendency to trust one another, especially in a seemingly routine context.Right now, no one is responsible; that's part of the problem. In the abstract, everyone is responsible...but that's not a fair answer. In the end, we all pay. The question really is: what's the most efficient way to assign responsibility? Or: what allocation of responsibility results in the most cost-effective security solutions?
We can't survive with a solution that makes the user responsible, because users don't have the knowledge and expertise to be responsible. The sysadmins have more knowledge and expertise, but they too are overwhelmed by the sheer amount of security nonsense they have to deal with. The only way to solve the security problem is to get to the root of it, and the roots are in the software packages themselves. Right now, software vendors bear no liability for the software vulnerabilities in their products. Changing that would put enormous economic pressure on software vendors, and improve computer security faster and cheaper than anything else we can do. I've written about this here."
I too would like to see software developers better address the issue. But unlike Bruce, I don't see that as quite the rosy picture he's painting. Reiterative security testing, while welcome, would no doubt increase the development cycle and overall cost of the software. Since it's not practical to expect all software developers to include an equally effective level of security testing and remediation, and since viruses and trojans authors generally find ways to proliferate their malware faster than developers can detect and close the holes, we're still going to need all of our expensive security software and experts to keep us relatively secure. Overall, we'd probably be more secure, but it's going to cost us. How much? As he mentioned, it's tough to determine what's the most cost-effective method for allocating responsibility. Not all that long ago, it occurred to me that the free market would probably determine how much security is appropriate and Bruce lays this out regarding Microsoft:
"The company is not a charity, and it doesn't make sense for them to make their products more secure than the marketplace demands. And right now the marketplace doesn't demand security."Lastly, Bruce offers good advice, but inherent in that is the requirement for self-education (my emphasis added):
"Do you have any practical advice for our readers, in terms of staying secure, and safe?Backup. Backup, backup, backup. You're going to get whacked sooner or later, and the best thing you can do for yourself is to make regular backups.
Staying safe in the Internet is actually pretty simple. If users bought a personal firewall and configured it never to accept incoming connections, and were smart about email attachments and websites, they'd be a lot safer. Also, the fewer Microsoft products the better."
August 13, 2004
Bust a Myth
PCWorld has a nice article that addresses some of the really tough PC questions:
- Do magnets really zap your data?
- What happens when you forget to "stop" a USB device before disconnecting it?
- Do browser cookies track everything you do on the Internet?
- What happens when you turn off your PC without shutting down Windows first?
- Does opting out of spam generate more spam?
- Does turning off your PC daily to save power really shorten its life?
- Is the government reading everyone's e-mail?
You'll have to read it to find out.
August 05, 2004
Crossing the Wi-Fine Line?
If you access an open Wi-Fi connection in the woods and nobody hears you, have you broken the law?
This type of mixed question seems to be stumping a lot of experts. Thanks to Ernie posting a related link, I just read a great article by Mark Rasch, the former head of the Justice Department's computer crime unit, who now serves as Senior Vice President and Chief Security Counsel at Solutionary Inc.
Mark gives a number of everyday examples, and points out the thorny legal issues. One of the big ones is how much should individuals be held accountable for not securing their own Wi-Fi networks?
Mr. Rasch responds:
"You're busted! You see, when you "broadcast" the cable connection, you are opening it up for anyone to potentially use it. So other people can potentially get Internet access from Comcast without paying for it. In Maryland, for example, it is illegal to use an "unlawful telecommunication device" which is a "device, technology, [or] product . . used to provide the unauthorized . . . transmission of . . access to, or acquisition of a telecommunication service provided by a telecommunication service provider." Delaware, Florida, Illinois, Michigan, Virginia and Wyoming all have laws on the books that may do the same thing."
Regardless of the outcome, it's just not wise to expose oneself to the threat of prosecution, embarrassment, and substantial legal defense fees for the sake of convenience. Regarding intruders accessing unsecured access points, Mr. Rasch properly raises the "slippery slope" problem, "How much security must you have on a system in order to be able to prosecute someone for accessing it without authorization?"
However, in regard to the "cable sharing" laws above, one would think the Wi-Fi network owner's simple act of enabling encryption, disabling the network name broadcast, and other easy security steps would be enough to keep him/her out of hot water. Again, how much security is required?
His answer to all of the above: "But ultimately if we want to move to ubiquitous wireless computing, where you can use the WiFi protocols for cheap, mobile VOIP communications, or have near universal wireless Internet access, we are going to have to persuade the law to get the hell out of the way."
My take on this is that intent plays a large part of the equation. Did you just set up your first wireless router and left it open out of sheer ignorance? Or did you then tell your neighbors, "Pssst, want some free cable Internet if you cut my lawn?" In a busy downtown coffee shop, did your wireless laptop automatically jump onto another's Wi-Fi network because its default settings told it to connect to the first open access point it found? What if that wasn't the coffee shop's free network, but that of the business next store? The problem is that other than reading the SSID (the wireless network's broadcasted name), it's not easy to know whose network it is. It's not like when you go to log in at the office, and a message pops up to tell you it's a private network, keep out unless authorized.
Both the technology and the law need to meet somewhere on these issues. Many of these questions and cases are very fact-specific. But here is the Catch-22: If the technology needs to add features like the ability to broadcast a "Private Property: Keep Out" message to provide notice of unauthorized access, then that broadcast itself is compromising security by announcing the network's presence in the first place. Perhaps this could be mitigated by enabling basic security as a default in the hardware from the manufacturers. In turn, the laws need to address the intention issues.
In the meantime, given the rate at which the law generally lags behind technological advances, we're probably in for a bumpy ride.
August 02, 2004
Thanks to All on My Wireless Router Query
A number of people replied to my query a few weeks ago, when I was trying to decide between the Linksys WRT54G and Netgear WGR614 wireless "g" routers on a security basis. I just wanted to say "thanks" for all the feedback. As you can tell from my recent posts, I've been playing around a lot with my wireless network to get the best performance and security out of it. All I can say is "This Rocks!", and I should have done this much, much sooner. But then again, I wouldn't have had the many benefits of having a "g" router if I bought "b".
Most people replied they didn't see much difference between the two models security-wise, but surprisingly many more favored the Linksys model, almost to the exclusion of Netgear. I ended up trying both of them thanks to a generous return policy at my favorite store. The security features were mostly the same, and while the Netgear had more user-friendly help screens and wizards, I kept the Linksys and returned the Netgear. Why?
The Linksys beat the Netgear router in wireless signal range alone, and it didn't hurt that it had two antennas to Netgear's one. Although Netgear definitely has the cooler-looking, more compact design, I'll take performance over looks any day. Also, the Netgear router's web interface didn't work well with my Norton Internet Security (NIS) firewall enabled. I had to disable my personal firewall just to reliably program the router. No problem with the Linksys, which incidentally ships with a trial version of NIS. The Linksys router also has additional encryption methods for supporting RADIUS and WPA key servers. While this is overkill for most home networks as these are usually enterprise solutions, it demonstrates a commitment to providing additional security features.
Last but not least, I really liked the fact that the Linksys firmware is based on Linux, and you know what that means. Yep -- open source. A little Googling led me to quite a variety of alternative open source Linksys firmwares offering a host of additional features. It piqued my interest that many included included the ability to adjust the transmit power of the router up or down (something Linksys doesn't provide, presumably due to FCC limitations).
However, I've since learned that a number of recent Linksys firmware releases introduced some bugs. While this is not good, the open source community works very quickly to report them and come up with alternative solutions. This is nice in that affected users don't have to wait months for the manufacturer to fix the bugs (if ever). In this regard, open source really works, and I have to wonder if this is part of the reason why the WRT54G is such a popular wireless router.
Regardless, the Linksys WRT54G has performed admirably and reliably. Even though I've placed it down in my basement office to limit signal leakage to potential hackers, it covers my entire house and back deck -- even the rooms on the top floor, which are two floors up. Amazing. I'd recommend it with the shipping v. 2.02.2 firmware version with the firewall enabled to close a remote administration security hole. If signal strength is important to you, stay clear of the two latest firmware versions, as quite a few people have reported this problem. I experienced it firsthand when I tried it before going back down to 2.02.2. Still, it performs better than the Netgear router, so I'm pretty happy with it overall.
Thanks again to all those who responded with a recommendation.
Posted by Jeff Beard | Permalink | Comments (0)
Various Wi-Fi Security Technologies Explained
The Ziff-Davis Channel Zone has a good article explaining the differences between the new wireless networking (Wi-Fi) security technologies, such as TKIP, AES, and 802.11i, and alerts us to some of the latest Wi-Fi security holes and threats. Thus it's appropriately entitled, "Making the Most of Wireless Security". Great companion piece to my "Wireless Networking Best Practices: Version 2.0" article.
August 01, 2004
Wireless Networking Best Practices: Version 2.0
I've updated my Wireless Networking "Best Practices" to add even more things you can do to harden your wireless network against intrusion. Please keep in mind there is a diverse range of networking equipment available, and that this information is provided as a courtesy. I've taken considerable time to compile and publish this information, because I have not found any single good source for all of these items. It's grown into quite a compilation.
This is also mostly geared toward home Wi-Fi networks, but the concepts are adaptable for corporate networks as well. Thus, you choose to make all changes at your own risk. If your router or access point has an option to backup its settings, then I highly recommend you back it up before and after making any changes, as well as being diligent in documenting any changes made. If you don't want to be an easy mark for wardrivers or your neighborhood hacker, read on. It's worth your while.
First, you really must change many of the default settings. Hackers and wardrivers know them all, because there are web sites that publish them.
This means you'll need to access your wireless router's configuration screen. One of the easiest ways is doing this through your web browser, and while you should be careful in the settings you change, it's something even a novice can do. While this isn't an all-inclusive list of security measures, these are things most home network users can do with care:
- Change the default SSID (Service Set ID or network name).
Hackers know all the default values for nearly each make and model, as they are posted all over the Web. If you really want to know, try another simple Google search for the following: default wireless SSID.
The SSID is your network name, and your wireless cards use this like a login name to connect to your network. That's why it's so important to change it from the default value. Resist the urge to name it after yourself or anything personally identifiable -- this just makes it easier for a hacker to find or guess a targeted network's name, and you just provided the casual hacker with your name.
- Disable the SSID broadcast.
By default, most wireless network equipment broadcast the network name to make it easy to find and connect to. If it's a convenience to you, it also makes a hacker's job a whole lot easier. Free programs like NetStumbler make it a breeze to find nearby networks and to tell its user the network names, whether or not they're encrypted, and much more. Disabling the broadcast of your network name essentially hides the network's login name. If convenience is a concern, then instead of broadcasting your network name, you're much better off setting your wireless software on your laptop to automatically login to it as a "preferred network".
Be forewarned, however, that even if you turn off your router's or access point's SSID broadcast, your laptop's Wi-Fi card will give it away. Wi-Fi cards broadcast the SSID in clear text when they attempt to connect to your Wi-Fi network. Like many of the other precautions listed here, disabling the SSID broadcast just makes it a little harder for the bad guys. The upside is that you're not broadcasting your network name 24 x 7, and that helps to make your network less visible. Otherwise, leaving the SSID broadcast enabled is the same thing as putting up a neon sign that says, "Hey guys, here I am, come hack me!"
- Change the default password for the router's Administrator account.
Again, wireless hackers know these defaults, most of which are simply "admin". Try a Google search for: default wireless router passwords. You'll find sites that list the login names and passwords for many manufacturers. Even if your particular model isn't listed, many manufacturers use the same values across their models.
If you don't change the password, then an intruder could easily reprogram your router to lock you out and open more security holes to allow him/her easier access. You'd then have to reset your router back to its default factory settings, and start all over again.
- Enable MAC Address Filtering.
This is a key wireless security measure, as it adds yet another layer of protection. Every Ethernet network card, wired or wireless, has a unique number called a MAC address. Enabling this feature tells your router to only allow access to authorized Ethernet cards. While it's possible for hackers to "spoof", or fake, a MAC address, it requires a higher level of hacker savvy, and it takes longer. The idea is to make it as difficult and time-consuming for wireless hackers, to discourage them to move on to easier pickings.
If you're wondering where to find each network card's MAC address, many of them have it printed on a label right on the card. Here's another easy way to find it:
For Windows NT/2000/XP/Vista:
1. Click on Start, Run, and type in cmd
2. Click OK, and a DOS-like window will appear.
3. Type ipconfig /all and press ENTER.
4. This will likely list information both for your ethernet network card and for your second wireless card. Under the wireless card, the "Physical Address" line should provide the 12-digit MAC address.For Windows 9x/ME:
1. Click on Start, Run, and type in winipcfg
2. Click OK, and an information window will appear.
3. In the pull-down section, click and select your network card.
4. The "Adapter Address" is your card's 12-digit MAC address.This 12-digit number is the one you need to enter into your wireless router's table. Make sure MAC filtering is set to only allow specified MAC addresses access to your network.
- Limit the number of allowed connections to the bare minimum needed.
Most routers will let you restrict the number of network connections. For example, if you have one desktop and one laptop, you only need two connections.
- If you can, consider disabling DHCP and assigning each of your PC's a static IP address.
DHCP (Dynamic Host Control Protocol) is a method in which your wireless router automatically assigns an IP address to each PC connected to the network. Thus if a hacker joins your network sufficiently, your router will cheerfully give her an IP address as well. Which is why limiting the number of connections is so important, and turning off DHCP so they don't get an automatic IP address.
BIG CAVEAT: It's probably ill-advised to set a static IP address if you connect your laptop to an office network. Most corporate networks use their own DHCP servers to assign and control IP addresses, and your static IP address could conflict or be in the wrong range. Thus if your laptop needs to connect to two or more networks, you probably will want to leave this alone.
- Enable the highest encryption possible: WEP 128-bit (802.11b) or WPA with TKIP or AES (802.11g).
Due to the relative ease in which WEP (Wired Equivalent Privacy) is cracked, WPA (Wi-Fi Protected Access) is vastly preferred. For home use, most people will want to enable WPA Pre-shared Key (WPA-PSK) and use a long key name with a mix of upper and lower case letters, numbers, and odd characters (such as ~!@#$%^&*).
For the WPA Algorithm, at a minimum choose TKIP (Temporal Key Integrity Protocol). Better yet, use AES (Advanced Encryption Standard) if your router, Wi-Fi card, and software support it. TKIP is an interim industry solution, but it adds the ability to automatically generate new keys at preset intervals. (For you Trekkies, this is akin to rotating the shield harmonics to repel the Borg. ;^) Rapidly changing keys gives the wireless hacker much less time to "sniff" and break the code before it changes again. Again, AES is the stronger encryption method that the wireless networking industry has been moving toward and is the preferred choice. If you have it, use it. [Update: The TKIP protocol has been partially hacked, so only use it if your router doesn't support AES. Many router manufacturers provide free firmware updates for your router that will allow you to use AES encryption instead.]
Please note that encryption reduces your overall network performance. However, since Internet speeds via cable and DSL are usually much slower than your network with encryption (especially under the "g" protocol), it should have no effect on your Internet access speed, just on file and print sharing speeds within your local network.
If you don't have WPA as an option, check your wireless equipment's manufacturer's web site for any firmware upgrades to WPA. If you can't upgrade your equipment, then enabling WEP encryption is better than nothing. However, I strongly suggest spending the money and upgrading to newer equipment that features much stronger encryption and is faster (12mbps with "b" wireless vs. 54mbps with "g" and 108mbps with "super g").
[Update: If your router and wireless devices support WPA2, use it instead of WPA as it is more secure.]
- Don't run your wireless network as a mixed "b" and "g" environment.
While 802.11b and 802.11g networks are compatible, it's not desirable regarding both security and performance results. The problem is that as soon as you add even a single "b" device to your wireless network, it brings the network down to the lowest common denominator. In this case, that means you only get the weaker and inferior WEP encryption (unless the "b" device can handle WPA), and the much slower "b" network speeds. Thus running a "pure g" network is better all around.
- Limit folder/file sharing to the minimum with password protection.
If you're home network is typical, you may have enabled folder/file sharing between your PC's for convenience. If you must enable sharing, then limit it to only those subdirectories required. Don't enable sharing at the root level of the hard drive. For instance, you might want to move a shared "My Documents" folder to another drive or partition and only grant access to it, rather than your entire hard drive.
- Change the default IP address of your wireless router or access point.
Again, hackers know these default addresses, so they know where to find your network devices. For instance, many Linksys routers default to 192.168.1.1 and Netgear's are 192.168.0.1. Under Internet standards, one of the three available private network IP ranges is from 192.168.0.0 to 192.168.255.255. (Tip: Each 3-digit section can only go from 0-255. Also, since 0 and 255 can have some special significance, avoid these two values.)
For example, you could change the IP address of a Linksys router from 192.168.1.1 to 192.168.100.1, or 192.168.1.100 (depending on which of the last two segments you want to change). Or you could pick a really odd number to make it difficult to guess, such as 192.168.177.13. Just keep in mind that it's more important that you can remember it. Otherwise, you won't be able to access your router to make changes (at least not without having to reset it to factory defaults and losing all of your hard work -- not good).
If you change this default IP address, also keep in mind that if you ever need to reset the router back to its factory defaults, afterward you'll have to manually login at the default address (e.g., 192.168.1.1) and change it back to your custom number. If your router is not using DHCP, then it's a good idea to keep your PC's IP addresses and the router's address coordinated.
By changing your router's default IP address, you are changing its location on your private network. Thus a hacker looking to access your router for reprogramming or discovering your settings will not find it nearly as easily.
- Make sure the router's firewall is enabled.
Most routers have their firewall enabled by default, but just make sure it's enabled, along with any related feature to block pings or "anonymous Internet requests". This will help stealth your network's presence to the Internet at large.
- Make sure the DMZ is disabled on the router.
A DMZ (DeMilitarized Zone) is a buffered zone that separates the Internet from your private LAN. However, in most SOHO routers, enabling the DMZ bypasses your router's NAT (Network Address Translation) and other filters, so it greatly weakens the security of any device located in the DMZ. Thus unless you're very savvy with networking, keep the DMZ feature disabled.
- Disable the router's Remote Management feature.
Remote management allows you or others to access your router to change its settings from outside your local area network. This should already be disabled as a default setting, but check it. Disabling remote management only allows access to the router's settings from within your private network.
- Disable Universal Plug 'n' Play (UPnP) on your router unless you absolutely need it.
UPnP is used for some devices like the Xbox game system. If you don't have a UPnP device, then make sure it's disabled. Otherwise, it's another potential security hole for your network.
- Use a VPN to connect to your office network when using a wireless network.
A VPN (Virtual Private Network) provides remote access to an organization's network over the Internet, through secure "tunnels" created by additional encryption. Typically, when your PC is connected to your office's network via a VPN, it can't "see" the rest of the Internet. Thus it's no surprise that VPNs are commonly used to help secure wireless networks. If your organization offers VPN use, it's yet another wireless networking best practice in your arsenal.
- Place the wireless router or access point away from outside walls to minimize signal leakage.
The closer you locate it to an inside wall, the more signal drop-off will occur by the time it reaches the outside. You don't want to provide a nice strong signal for others to jump onto your private network.
- Configure your laptop's wireless card software appropriately.
To avoid accidental connection with strange Wi-Fi networks (you don't know where they've been or who's on them), configure your wireless card's software for the following:
- Connect only to access point (infrastructure) networks, to avoid any undesired "ad hoc" peer-to-peer connections, and
- Uncheck any feature for automatically connecting to non-preferred networks. Otherwise, your laptop will jump onto the first open network it finds. If you routinely forget to turn off the card's radio, this will help stop it from getting you into trouble.
Additional "Must Use" Safeguards:
- Personal or software firewalls, such as ZoneAlarm Pro and Norton Internet Security
Even if your router has a good firewall, it generally won't stop outgoing traffic from spyware and malware that's phoning home. A properly configured personal firewall will. You also need a personal firewall on your laptop when you connect to other access points, such as when traveling.
- Good antivirus software
I'm quite partial to the Norton Antivirus line, it just works without causing me any problems.
- Anti-spyware/malware programs, such as Ad-aware, Spybot Search & Destroy, and PestPatrol
Ongoing Maintenance for the Best Security:
- Keep the personal firewall and antivirus programs updated with the latest definitions.
- Keep up with the various security patches from Microsoft.
- Change the router's login name and/or password periodically. Use strong passwords (at least 7-8 digits, with mixed case, numbers, and other characters).
- Change the wireless network SSID value periodically. Again, use strong names (at least 7-8 digits, with mixed case, numbers, and other characters).
- Change the WEP or WPA encryption keys periodically. Same advice regarding strong passwords applies.
- Always check all of the above settings after performing any router firmware upgrades. For example, Linksys router owners discovered that upon upgrading from firmware version 2.02.2 to 2.02.7, Linksys changed the firmware's UPnP default to "enabled" just to earn Microsoft Xbox certification. However, for most of their customers, they just opened up another potential security hole. Thus it's helpful to print out all of your router's setting pages and keeping them in a secure place for reference.
Naturally, the more secure you make it, the less convenient the setup. But I'll take the extra wireless security anytime, because wireless networks are still horribly insecure compared to wired. But as you can see from the above, you can still do a lot to harden it against intrusion, and it doesn't take a networking guru for many of them. Wi-Fi itself is a tremendous convenience and enabler, if it's done right.
[Update 11.29.08: Please see my post, "Wireless WPA Encryption Component Hacked -- How to Protect Yourself" in light of the published TKIP vulnerability.]
Posted by Jeff Beard | Permalink | Comments (0)
July 08, 2004
Which 802.11g Router is More Secure?
Here's a query for the security savvy -- in your opinion, which Wi-Fi "g" router is better for overall security features for a home network, the Linksys WRT54G or NetGear WGR614?
The background info: The dust has begun to settle after my move, and I've got the cable guy coming in next week to install broadband. They're providing the basic cable modem for free, so it makes sense for me to get an 802.11g Wi-Fi router over the weekend, primarily to share the Internet access, but also to network an HP DeskJet, and for the odd file transfer between two PCs (a desktop and a laptop). The Wi-Fi is primarily for the laptop's mobility, a Dell Latitude D600 with a Dell TrueMobile 1400 802.11a/b/g combo card.
While Wi-Fi performance is important, I'm much more concerned about the security. I've got it pretty well covered on the PC level (software firewall, AV, anti-spyware scanners, checking on Windows sharing, etc.), but it hasn't been fun trying to get reliable security specs on the routers. It would've been better to run a dedicated firewall server on a separate device, but due to a lot of time constraints, I'm just not going to have any time to tinker with it for the forseeable future.
So far, both the Linksys WRT54G and NetGear WGR614 wireless "g" routers look pretty good to me, but I could use a more experienced eye. It appears that both feature NAT, SPI firewall, MAC address filtering, SSID broadcast disable, WEP and WPA encryption, and more. Although one Linksys WRT54G product page mentions NAT, another one omitted it -- any WRT54G owners who can confirm NAT is included? Also, can anyone confirm whether either one can limit the number of connections independently from MAC or IP address filtering (since MAC and IP addresses can be spoofed)? Their tech support people weren't terribly helpful or certain on this one. For instance, it would be good to limit connections to only 2 PCs, as well as by MAC and IP addresses.
Given that time is growing short, I'm hoping someone can confirm these security specs and/or make an experienced recommendation between them (or offer a better selection if warranted) for best overall "g" security. I won't be running any 802.11b devices, so this is a pure "g" environment. I'm looking to stick with proven, quality name brands for support, warranty, and firmware upgrade issues. Have I missed anything?
Many thanks in advance for all comments and/or e-mail replies.
Jeff
July 07, 2004
iPods & Flash Drives Are Probably Worse Risks Than Camera Phones
...At least in my opinion. Many camera phones on the street still take fuzzy low-res photos (although that's a-changing too, with more megapixels coming all the time). This isn't saying that they can't be used to compromise sensitive information, record movies, violate privacies, etc. Of course they can.
However, while the mainstream is busy banning camera phones like it's the latest fashion craze, innocent-looking camera-less devices (and their owners) can easily be making off with a LOT more information. Compact, high capacity, and high speed USB and Firewire devices connect nearly instantly, without security measures or additional drivers, and can receive or transmit a lot of information in a very short time. Consider iPods, portable hard drives, tiny flash drives, flash card readers, and more. Why steal a desktop or laptop PC when you can make a copy of its potentially more valuable data in a fashion that's quick and nearly undetectable? On the flip side, they could be used as entry points for distributing malware into various networks.
The allure of these tiny, light, ultraportable, hot-swapping, plug 'n' play marvels (which Windows instantly mounts) is incredible. After all those years of suffering through torturous legacy hardware incompatibilities, popping off PC cases, and incurring the lifetime scars from sharp innards, we've finally arrived into hot swap Nirvana.
Apparently, Gartner thinks so too, as the The Register reports these devices are the latest security risks. Don't get me wrong, as I'd rather part with a thousand blurry (and thus mostly useless) camera phones before giving up my High-speed USB drives. They're that convenient and they just plain work (like doing a full Ghost dump of my laptop's drive in 12 minutes under full compression, and restoring it in under 5). Quite a long while ago, I read an online news article about folks walking into computer stores with hard drive music players and using them to download and pirate Mac software right off the sales floor PC's (it was probably on Wired News or The Register). Back then I wondered how long it'd be until these devices would be banned in commercial places.
So once again, the mainstream feels good in banning cell phones all over the place to feel secure. In my mind, why capture bad video when you can get perfect copies of the source? Doh! It's not like these things haven't been around longer than camera phones. Just something to think about if you routinely leave your PC unattended and unwatched during meetings, lunch, etc. Even if you tie it down with a Kensington cable, make sure you lock it via Ctrl-Alt-Del. With new tiny flash drives being endowed with 32-bit processors and server capabilities, I truly feel it's only a matter of time until someone comes up with an even slicker way to suck your secrets while you're standing in the express check-out lane during lunch.
Of course, all of this discussion begs the question of why chance getting caught in the physical act at the scene of the crime? What the news story really should have mentioned is that even USB (Ultra Speed Burglary) and laptop lifting is passé today when you think of the chic-ness and thrill of doing it wirelessly through all of the many grossly insecure consumer-configured Wi-Fi networks and personal firewall-less notebooks. Somehow it gives new meaning in a Wi-Fied McDonalds when they ask if you want it "to go".
[P.S. It's good to be back posting again after over a week's self-imposed abstinence, which is highly unusual for me. Between the new job, the near-endless unpacking, holiday, and being an active Dad and husband, something had to give. Like life, the summers in the Midwest are too short to miss -- especially when it comes to grilling beer brats and enjoying good company on a perfect summer's eve. Rest assured the tips and tricks are still in the works.]
May 20, 2004
Spybot Search & Destroy 1.3 Released
Spybot - Search & Destroy version 1.3 was released this week. I've been using version 1.2 for quite a while and strongly recommend it as a very effective and free anti-spyware/anti-malware scanner and removal tool. Simply put, it does what your firewall and antivirus programs can't. Nowadays, spyware and malware are just as serious threats to your data and privacy as viruses.
From the download mirror at Download.com: "Version 1.3 adds enhanced immunization features, an improved interface, and integration of BrowserManager for spyware detection, plus the new Hosts File feature and bug fixes.
Download.com's mini-review states:
The latest version of Spybot - Search & Destroy adds some truly useful features to an already excellent app. The program still checks your system against a comprehensive database of adware and other system invaders, but it works much faster now (in our testing, three minutes versus 10 minutes previously). It also features several interface improvements. Scan results now appear arranged by groups in a tree, and a sliding panel lets you instantly view information about a selected item to help you decide whether to kill it or not. The Immunize feature blocks a plethora of uninvited Web-borne flotsam before it reaches your computer. Other useful tools, including Secure Shredder, complement the program's basic functionality for completely destroying files. Hosts File blocks adware servers from your computer, and System Startup lets you review which apps load when you start your computer. The functionality makes Spybot - Search & Destroy a must-have for all Internet users, and this version is a worthwhile upgrade."However, the download mirror at MajorGeeks.com has this caution regarding one of the new features:
Editor's Note: The Resident shield in version 1.3 has an issue allowing certain cookies (Specifically Double Click) when set to notify. If page loading becomes a problem, right click the icon in the Systray, select “Resident IE” and either uncheck “Use Resident in IE sessions” or check "Block all bad pages silently.Due to very high demand, occasionally Spybot's official web site may fail to load, stating that the CGI limits have been reached. Just keep trying to refresh the page, and it will eventually load. However, since you can't download Spybot directly from its site, you may just want to go directly to Download.com or MajorGeeks to get it right away. MajorGeeks advises, "Please uninstall previous versions before installing this one." As with all new versions, don't be surprised if there are some new bugs. Therefore, you'll probably want to run the program's internal web updater to get the latest fixes and malware updates.
May 10, 2004
Multi-Use Cell Phones Causing Multiple Problems
Sometimes, integration isn't such a good thing. That's a bit of a departure from the times I've emphasized that integration is a key productivity pursuit. Well, as much of a gadget lover and power user that I am, I just haven't had much interest in having a cell phone with an integrated camera. Why? For one, most current camera phones are barely cameras by today's high-tech standards (very low resolution, no flash, pitifully small memory, etc.). I prefer just having a separate pocket-sized and higher quality digital camera, and I'm not alone -- a number of camera cell phone owners have reported the thrill wears off fairly quickly and the photo quality isn't all that hot. Naturally, the drawback with separate devices is that you have to carry more than one. You also lose the instant ability to e-mail the pics unless your cell phone also uses a compatible flash memory card and supports e-mailing photos -- a feature which most non-camera call phones lack unless they have a built-in camera. See the problem?
Second, and more importantly, it's a good way to lose your cell phone and/or your privacy in a number of public places. Engadget posted about an eWeek article, "The Hassle of Built-In Cameras", which does a good job of summing up the issues. There are plenty of public and government locations where camera phones are banned and even confiscated. A little over a week ago, I went to the advance local movie premiere of "Laws of Attraction" and the tickets clearly stated that all video recording devices were prohibited, including camera cell phones. Since most of these devices feature an integrated camera, you can't simply pop it off. Instead, you have to throw the baby out with the bath water in leaving it behind. I put my non-camera cell phone on vibrate mode for a good compromise in the theater. That way I wouldn't bother anyone during the show with annoying ring tones and could easily walk out into the hallway to talk if an emergency arose.
The ability to remove devices is why I still love my trusty Handspring PDA -- it is a consummate technological chameleon. Handspring was definitely onto something important with their Springboard modular approach, and my many modules regularly continue to be of great use. The problem was that it just didn't catch on due to its size, modules' relative expense, and that people thought they wanted everything built-in, including cameras. Well, a number of camera cell phone users have had them confiscated or were told that they can't use them where standard cell phones are allowed. Thus the pendulum is beginning to swing back the other way as I thought it might, especially after reports of camera phone voyeurs popped up shortly after they arrived on the scene.
Another major issue is privacy. Engadget also posted about this serious privacy intrusion at a Pennsylvania high school, where a teacher and assistant vice principal tried to play Starsky and Hutch with a student's cell phone instead of calling in the real police or the parents. A key part of the facts relate not to an integrated camera, but to a text message present in the cell phone -- which the school personnel claimed could have one interpretation of a drug reference by slang use of a common word. Needless to say, the student's parents were not amused and contemplated legal action is mentioned. If filed, this is going to be an interesting test case in trying to balance the relative interests, especially since the Morning Call article mentions that "Pennsylvania is the only state with a constitution that protects privacy rights." Also consider that the more integrated something is, the higher the security and privacy risks become, because there is more information available on the device.
For some time I've been eyeing up the Treo 600 as my next possible PDA upgrade, but the integrated camera is actually holding me back rather than enticing me. Because I can't carry it in a number of places where I'd have a regular cell phone, the low-res camera becomes a liability, not an asset. I'd rather have the camera be an SDIO (Secure Digital I/O) card attachment than fully integrated, and preferably be at least 1.3 to 2.0 megapixels to be of any real use. That way I can leave it behind when prudent or necessary. Apparently others must have made the same comments, since Engadget mentions in the post that "PalmOne is already supposed to be coming out with cameraless version of the Treo 600." TreoCentral also mentions a non-camera Sprint Treo 600 should have been available by April, but I haven't had an opportunity to see if it's been released yet. As there's been several rumors of the Treo 610 being the next minor upgrade model, I'm now waiting to hear reliable information regarding its camera status to see if I can get the best of both worlds.
Don't get me wrong. Mobile digital photography and text messaging are incredibly useful technologies in their own right, and should definitely be used appropriately. I particularly love PDA smartphones due to the fact that we finally have the ability to have one address book -- the cell phone and PDA share the same one internally, and it's relatively easy to sync it up with one's favorite contact manager or groupware software, such as Outlook, on the PC. While smartphone PDA-based web browsing isn't the same experience as PC-based browsing, I've found it to be quite handy.
With that said, having a little too much crammed together into one device occasionally becomes a larger inconvenience -- rather than the ultimate convenience we were expecting. Another downside is that when one loses the integrated device for whatever reason (confiscation, theft, leaving it behind to prevent either of the former), one also loses all of the functionality in one shot. Which leads me to this strange situation where I find these integrated devices attractive and compelling (especially for the integrated address book and wireless access), and yet in some ways more troublesome than having the "standard" standalone devices. The trick is in selecting one which will provide you with more productivity and other gains overall, while keeping in mind that some key or critical uses may be prohibited at an inopportune time and/or place.
I believe we're going to see more instances of camera cell phone prohibitions, and I've already come across news articles reporting that various companies are developing technologies to remotely and automatically disable certain kinds of portable devices within a given area.
To each his or her own, but here is a place where I'd like to see more choice in the market. As camera phones gain higher resolution, functionality, and uses over the next few years, it's going to be very interesting to see how businesses, schools, government agencies, and the users themselves will address these issues.
[Update 5.24.04: The National Law Journal has a very good article discussing the specific problems that cell phones pose in court, ranging from contempt incarcerations to bailiffs dropping phones out of five-story windows.]
Posted by Jeff Beard | Permalink | Comments (0)
May 05, 2004
D.C. District Court Rules Gramm-Leach-Bliley Act Beyond FTC's Statutory Authority
The ABA and the New York State Bar just won at the federal district court level (D.C.) in their suits against the FTC regarding the application of the Gramm-Leach-Bliley Act to the practice of law, particularly in "financial activities" which include real estate settlement, tax-planning, and tax preparation services. If the decision ultimately stands, it appears attorneys should have one less regulatory concern regarding privacy notices and related provisions.
ABA President Dennis Archer sent out a mass e-mail to ABA members describing the victory, including the link to the ABA's GLBA web page wherein you can find the D.C. district court decision in PDF format.
Judge Reggie Walton of the U.S. District Court for the District of Columbia signed the order granting summary judgment:
"This is because the case is now in a posture where, for all of the reasons expressed by this Court in its August 11, 2003 Memorandum Opinion, the Court can now definitively conclude as a matter of law, pursuant to 5 U.S.C. § 706(2)(C), that Congress did not intend for the GLBA's privacy provisions to apply to attorneys who provide legal services in the fields of real estate settlement, tax-planning and tax preparation, and that, pursuant to 5 U.S.C. § 706(2)(A), the FTC's interpretation that attorneys are subject to the GLBA's privacy provisions constitutes "arbitrary and capricious" agency action.[Update 5.07.04: The ABA Journal eReport has a good article discussing the ramifications and issues surrounding these developments.]Accordingly, it is hereby, this 30th day of April, 2004 ORDERED that the Plaintiffs' Motion for Summary Judgment is GRANTED. It is FURTHER ORDERED that the Defendant's Cross-Motion for Summary Judgment is DENIED. It is therefore DECLARED and DECREED that the FTC's decision that attorneys engaged in the practice of law are covered by the GLBA is beyond the FTC's statutory authority. It is FURTHER DECLARED and DECREED that the FTC's decision that attorneys engaged in the practice of law are covered by the GLBA is an arbitrary and capricious agency action. SO ORDERED."
Posted by Jeff Beard | Permalink | Comments (0)
April 30, 2004
Overcoming Wi-Fi Networking Problems
If you've successfully set up a working wireless network, give yourself a pat on the back. Even with all of the security features disabled and using the default settings, they can be tricky little buggers to get up and running. However, if you haven't done much to change those default settings, you're leaving yourself wide open to attacks and other problems. Also, you might have found that your overall Wi-Fi range and user experience could use a little boost, but weren't sure how to do it. That's why I enjoyed PC World's feature article on "Beating the Wireless Blues" from their May 2004 issue.
It addresses a wide range of wireless networking problems and offers a number of troubleshooting ideas and solutions. Be prepared to roll up your sleeves for some of the items mentioned -- but this is why I liked this article over others which merely gloss over only the most common issues, or alternatively get too techie. While I thought the security advice could be a bit more robust, it did offer up some interesting bits.
For one, expect to see Intel 802.11g Centrino laptops this year, which is something I've been waiting for. Second, be extra careful with your WPA passphrase per the article: "Though this privacy standard is highly secure, a researcher reported in late 2003 that a passphrase less than 20 characters long composed entirely of words could be cracked. Use a longer passphrase, and include some punctuation marks or numbers for maximum security."
So how many of you are using 20+ WPA passphrases with mixed characters, case, and punctuation? Probably not enough. If you're still using 802.11b, be aware that newer "b" devices have WPA included, and some older ones have WPA patches available from the manufacturer, generally as firmware upgrades. You should be using this improved security feature over the vastly inferior and insecure WEP at all costs. While WPA isn't perfect, it's definitely better than WEP for encrypting and protecting your wireless network.
As I mentioned, I would have like to see a more complete security checklist, but the article appeared more focused on overcoming other obstacles to achieve a better user experience. Which is why I think it's helpful to include my list of Wireless Networking "Best Practices" for a fuller list of security items to address. Regardless, the PC World article is chock full of links to other great Wi-Fi articles and even provides a handy Wireless Networking Kit -- a list of essential hardware and software tools that no Wi-Fier should leave home without.
Posted by Jeff Beard | Permalink | Comments (0)
April 26, 2004
What to Make About Spyware Results from Earthlink
Earthlink published the spyware results for the first quarter of 2004, compiled from Webroot's SpyAudit program and EarthLink Spy Audit. The Register and MarketingVox commented on the results.
The number breakdown from a total of 1,062,756 system scans:
System Monitors (e.g., keyloggers) = 184,559
Trojans = 184,919
Adware = 5,344,355
Adware Cookies = 23,826,785
All for a grand total of 29,540,618 instances of spyware found. Divide this by the 1,062,756 system scans, and one arrives at the average of 27.8 instances of spyware per scanned PC.
However, these results are not empirically helpful. For instance, let's assume my PC had 100 infestations and I used their service to scan it weekly and didn't know how to remove the malware. Now let's compare it to someone who only ran the scan once and then cleaned their system. Wouldn't that skew the results?
Instead, I think the numbers are useful for less stringent scientific study. For instance, adware browser cookies are by far the most common, with adware not that much behind. Fortunately, true spyware (keyloggers, trojans, etc.) is less common in comparison, but I find those numbers quite telling in that it is definitely a problem. However, it's been my experience that users who have spyware on their system have it for the most common reason that they simply don't know how it got there. In other words, they're happily surfing along and downloading malware-ridden programs of interest, without realizing that they are the direct cause of their own infestations. Perhaps they didn't have a firewall or antivirus software installed. It's not uncommon at all to find that such a user has multiple spyware infestations ranging from browser hijackers to trojans, worms and other nasties. All of which would further skew any such "average infestation" analysis. While probably a good number of PCs have some malware installed either by choice or otherwise, I'd bet there are a smaller number of machines with "hyper infestations".
I'm also likely to conclude from the above results and my direct experience that the vast majority of us probably have more undesirable browser cookies than we'd like, but unless our browser is actively blocking them, we just don't have the time to deal with them individually. Running scans from Ad-Aware, SpyBot, PestPatrol and the like is probably the easiest second line of defense after they've made it past any browser defenses, which by default are set to fairly weak protection so that web sites load properly.
I don't see malware going away any time soon, and I'd suspect that the people with multiple infestations are probably not following some basic rules of practicing safe hex:
- Use a firewall, even if it's only a software-based personal firewall like ZoneAlarm. Properly configured, it stealths your computer ports and acts like a traffic cop to block many inbound and outbound threats. I don't recommend using Windows XP's built-in firewall since it only blocks inbound requests. However, even this is better than using no protection at all.
- Use a name brand antivirus program and keep it updated. My personal preference is Norton Antivirus, but there are a number of good ones available.
- Antivirus programs won't detect or block all threats. Install and regularly run good anti-malware programs such as Ad-Aware, SpyBot, and PestPatrol.
- Be selective of the web sites you visit, but more importantly, be cautious of the content you click on. For example, don't click on those ads that say you've won something (e.g., the moving monkey). If it's not relevant to what you are looking for, why click on it?
- Set your web browser to disable or block unsafe content (e.g., objects not marked safe for scripting), and set it prompt you for potentially dangerous content (e.g., ActiveX objects).
- Before downloading programs, especially those for free, read the privacy policy to see what information it tracks. This will give you some idea of its intrusiveness.
- Also check out special web sites such as SpywareInfo and Spyware-Guide.com, which provide tons of helpful information and maintain lists of spyware- and malware-ridden programs.
- Regularly use Windows' and other tools to examine your Windows startup settings (registry, startup group, etc.) to remove any malware from autostarting.
- Be wary of clicking on any links or attachments in e-mails that are not from trusted sources. If you can, open the source e-mail message in a pure text editor, such as Notepad, to verify that the links really do go where they're supposed to go.
- Use good anti-spam software. The more junk mail that is blocked or filtered into a separate spam e-mail folder, the less likely you'll want to open it or any attachments, or click on any embedded links.
I could go on, but you get the idea. The reason why malware spreads is collectively "us". Security is a process, not a product, and we remain the weakest link in that chain. While most of an organization could be using the Internet with caution, it only takes a very few uninformed users to unwittingly compromise a system. Thus having good backup/recovery/incident plans and systems are just as important. Perhaps most important might be what I've attempted to achieve via this post: education. Remove someone's spyware for them, and it's clean for a day. Show them how to avoid getting it in the first place, and it just might stay clean longer.
March 23, 2004
Is Your Network A Legal Minefield?
Art Jahnke at CIO.com has this to say about peer-to-peer file sharing performed over company networks:
"A survey released two weeks ago by security provider Blue Coat Systems found that many employees continue to download files at work, using applications like Gnutella and Kazaa. According to Blue Coat, 38.6 percent of 300 respondents said they do their file sharing on company networks. The survey also revealed that 60 percent of respondents were unconcerned about the possibility that the Recording Industry Association of America could sue their employers.There are several useful comments posted by readers at the end of the online article, which discuss the importance of having a well-drafted policy and utilizing the right tools to establish the audit trail back to the culprits, thus making the policy enforceable.Is that scary? Whose responsibility is it to keep a company’s networks from becoming a legal minefield? Isn’t that your job? What is your company doing to keep its networks clean? Nothing?"
Posted by Jeff Beard | Permalink | Comments (0)
March 03, 2004
Beware the Spy Phone
A company named Endoacustica claims they can modify Nokia and Siemens cell phones to reprogram them as spy phones. The site displays the Nokia 8310 relabeled as the "SPY-PH-NOKIA 8310". This phone can be used with any sim card in any country.
They claim the cell phone operates as usual for incoming and outgoing calls. That is, until someone calls it using a preprogrammed number. Then it answers automatically without ringing or lighting up, and the display appears to remain in ordinary standby. This enables the caller to listen to the cell phone's surrounding sounds and conversations, rather like a baby monitor.
Bottom line: Don't accept cell phones as gifts or loaners. I suppose it depends upon how the modification is done, but wouldn't the eavesdropper's airtime show up on the spyphone's monthly provider bill?
March 01, 2004
Anti-Spyware Legislation Introduced
From the press release:
"U.S. Senators Conrad Burns (R-Mont.), Ron Wyden (D-Ore.), and Barbara Boxer (D-Calif.), today introduced legislation to prohibit spyware, adware, and other invasive software from being secretly installed on Americans’ computers. For the first time, the SPYBLOCK (Software Principles Yielding Better Levels of Consumer Knowledge) Act would prohibit installing software on somebody else's computer without notice and consent, and requires reasonable "uninstall" procedures for all downloadable software. Spyware, adware and other hidden programs often secretly piggyback on downloaded Internet software without the user’s knowledge, transmitting information about computer usage and generating pop-up advertisements. Frequently such software is designed to be virtually impossible to uninstall."Amen to that. While I heartily applaud their efforts, I also have similiar concerns regarding this legislation that I had for the CAN-SPAM Act, which I enumerated here and here. It may provide relief against U.S.-based malware developers, but what about internationally-hosted software? At least some recourse against American companies may be better than none. For that I applaud the senators for trying to do something about it and protect the end users from some of the more insidious practices.
Lest my bias be misunderstood, I'm acknowledging that some adware/spyware may be beneficial. For example, someone who can't afford an expensive commercial program may find their needs met by an adware-supported free download. As long as there's informed consent, and the adware is easily and fully removable when the person no longer wants to use the ad-sponsored software, then that's the person's free choice and they shouldn't complain. As long as they know about it, then people are free to vote with their mice, and program authors should get paid for their work if it's on the up an up. In other words, there's some quid pro quo by consent. I'm really referring to the malware that surreptitiously installs itself as a parasite accompanied with other desired software or under other false pretenses.
Nifty Online Spyware and Adware Encyclopedia
If spyware and adware has crept into your system, most people will usually download Ad-aware or Spybot Search & Destroy, scan their system, and let it remove the offending software.
Sometimes, though, such a removal might fail, or you might want to know more about what the malware was designed to do on your PC prior to removing it. After all, some free programs will fail to operate if the underlying spyware/adware is removed.
In the "Why didn't I think of that?" category, that's where the free Bazooka Spyware and Adware Encyclopedia comes in handy. It lists several hundred of the more popular "vermin" (as I like to call malware), along with specific details regarding its classification, function, installed files, vendor web site and privacy policy, uninstall procedure, and perhaps most importantly, the manual removal steps if all else fails. The latter is also useful if you just want to verify that your system is finally rid of all traces. It's reminiscent of some antivirus vendors' virus databases, but is specific to spyware and adware, which are not technically viruses.
The encyclopedia is not all that's available. The same site also offers the freeware Bazooka Adware and Spyware Scanner. I haven't tried it yet, but it sounds like it's a scanner only, i.e., that it will scan your system and alert you if it detects installed spyware and adware. I didn't see any information that it will actually remove the vermin for you. If I'm correct, that's where the online encyclopedia (and other malware removers such as Ad-aware and Spybot) should be used.
While I run a tight ship on my own PC to keep it meticulously malware-free, I've helped others by removing offending software -- usually piggybacked in downloaded program installers. As I mentioned, it's important to know which changes have been made to the system and what the malware does prior to removing it. What's nice about this site is that the information is all in one place for many common malware programs. And for that I give the Bazooka Spyware and Adware Encyclopedia a big thumbs up!
February 29, 2004
RFID Tracking Concerns Lawmakers
If you're not yet concerned about RFID (Radio Frequency Identification) tags, you should be. These tiny devices can be included in many consumer goods. As such, there is growing concern about how they can be associated with individual consumer information and even tracked in public places by strategically-placed readers. Wired News has a good summary in "Lawmakers Alarmed by RFID Spying", which reports on several states' attempts to enact legislation. Not so coincidentally, Wired also reports German protesters have similar concerns.
Personally, I probably wouldn't care too much if someone knows I bought a pair of Levis, with the possible exception that I wouldn't want to get spammed by people trying to sell me more jeans (as least now I'm mostly protected by my state's Do Not Call List -- that has been a huge blessing from relentless and rather pesky telemarketers). Regardless, I'd categorize that as more of an annoyance. Now let's take it one step further: As one person commented here previously, it could be used to present personalized on-demand advertising, a la Minority Report (and this is also mentioned in the first Wired News story above).
However, after that unique identifier gets associated with me, readers in public places could track my whereabouts. My concern is once the genie is out of the bottle, where will it end? Several years ago, I posted to one of the legal tech listservs that online data collection (e.g., cookies, spyware, etc.) could eventually be tied into the brick and mortar companies' databases and the crossover effects would be chilling. Not too long after that, DoubleClick tried to do exactly that. Fortunately there was much public outcry and DoubleClick adolescently stated they were very sorry and wouldn't do it again. Suffice it to say, there are still serious public trust issues.
This quote pretty much sums it up: "'Some lawmakers now say that RFID tags in retail items may further erode consumers' privacy. "There is clearly an upside for the industry,' said Massachusetts state Sen. Jarrett Barrios, 'but underlying that is a burden borne by the consumers. It's unnerving to me that the companies have no incentive to protect consumer privacy.' " Sure, consumers can vote with their wallets and try to boycott merchandise with embedded RFID tags. That may work in the beginning, as a few select companies get scorned by consumers. But what happens if the manufacturers and retailers decide to tough it out until most items on retail shelves and in online stores have them? In my humble opinion, under that scenario consumers would have little choice but to succumb to the situation and buy them under protest if there are no other reasonable alternatives.
Thus unless sellers bow to public outcry, the free market model may not work in this case: "RFID technology is a surveillance tool that clearly can be misused, said Barry Steinhardt, director of the Technology and Liberty Program at the American Civil Liberties Union. 'To protect consumers, we need laws, not unenforceable policies," he said.' "
But what laws should we enact? Should RFID be banned outright? Should it stop merely at "truth in labeling" so consumers can make informed choices? Do we borrow a page from the online privacy debates to implement "opt in" vs. "opt out" strategies, and thus attempt to allocate who should bear the the burden that way? Or something different altogether? Certainly RFID has legitimate uses for inventory control. Somehow my gut tells me that none of the above will be the best solution, or worse, that there may not even be one due to the polarization that has already occurred. Only time and a lot of public debate will tell.
[Update 3/1/04: Techdirt has an interesting post on the potential for an RFID blocker tag. Apparently, researchers at RSA have begun demonstrating how the blocker tag works. As I mentioned above, I doubt a purely legal approach will adequately resolve the many RFID issues. As RFID is partially a technological problem, some creative technological approaches may help.]
February 25, 2004
Bluesnarfing: Serious Bluetooth Security Flaw
First there was Bluejacking, which was more or less harmless pranking via Bluetooth-enabled cell phones.
Bluesnarfing, on the other hand, is much more serious. (Don't look at me, I didn't make up these names -- ironically Bluesnarfing is closer to real Bluetooth hijacking.) CNet News reports in this article how a number of Nokia cell phones are the most susceptible.
Bluesnarfing is a security flaw in Bluetooth implementations in which an attacker exploits it "to read, modify and copy a phone's address book and calendar without leaving any trace of the intrusion." "According to Nokia, if an attacker had physical access to a 7650 model, a bluesnarf attack would not only be possible, but it would also allow the attacker's Bluetooth device to 'read the data on the attacked device and also send SMS messages and browse the Web via it.' " Furthermore, Nokia stated "that its 6310i handset is vulnerable to a denial-of-service attack when it receives a "corrupted" Bluetooth message."
As Dana Carvey would probably say, "Well now, isn't that special?" Wireless convenience just inherently introduces more security issues.
Per AL Digital, the security company that discovered the flaw, it affects some Sony Ericsson, Ericsson, and Nokia handsets. However, the Nokia 6310, 6310i, 8910 and 8910i phones are at greater risk because they invite attack even when in "invisible mode". FYI, in invisible mode, "the handset is not supposed to broadcast its identity and should refuse connections from other Bluetooth devices." Whoops.
I've been a big fan of Nokia phones. Compared to others I've had, their business class phones have been generally more rugged and have better sound quality. I've even read posts from Nokia owners who've run them over with their car, put them through the washer and dryer, and they still worked. However, until Nokia provides a fix for this, I'm going to stay away from their Bluetooth phones as a precaution. That's the real shame, as Bluetooth was just finally beginning to deliver on much of the hype we've heard over the past several years.
Posted by Jeff Beard | Permalink | Comments (0)
February 23, 2004
Easy SpamAssassin Tips That Work
A LawTech Guru feature article by Jeffrey Beard
(For reprint arrangements, please contact me via .)
If you're using the popular SpamAssassin software to deal with spam, or perhaps considering its use, here are some firsthand tips written in plain English to improve its effectiveness:
SpamAssassin was included in the base monthly price of my web host provider, one of the deciding factors for choosing them. Between June and November, SpamAssassin did an incredibly accurate job of flagging spam with virtually no false positives (less than a dozen misflagged legit e-mails in 6 months). SpamAssassin does this by analyzing each e-mail for certain traits and then assesses a differently weighted value for each trait found. Then it adds up these values, and if the total exceeds your chosen threshold, it flags it as spam.
Since SpamAssassin had done a great job, I left the original default settings alone. In December, my experience changed dramatically. Suddenly, roughly half of incoming spam messages were scoring below SpamAssassin's default threshold of 5.0. Luckily I wasn't seeing any false positives (legit e-mail being moved into my Spam folder), but I had to wade through a lot of spam left in my regular Inbox. It appeared spammers crafted messages that fell under SpamAssassin's default settings radar. I didn't want to reduce the threshold score because some valid e-mail was scoring in the 4.x range. I'd rather err on the side of having some spam in my Inbox than filtering legitimate e-mails into my Spam folder. However, I missed reading several important messages in my Inbox because they were buried in the surrounding spam.
At first I chalked it up to the holidays -- spammers were going all out during the big spending season. But it didn't relent in January or February. That's when I decided to take things into my own hands. I called my host provider's tech support, which has been exceptional on technical matters. Surprisingly, both the first level rep and supervisor were pretty clueless on SpamAssassin, and suggested I head on over to SpamAssassin's web site for better documentation. I was disappointed there as well. Armed with the suspicion there had to be more people using SpamAssassin with similar problems, I went a-Googling.
I quickly located information on enabling SpamAssassin's RBL checks (Realtime Blackhole List, a blacklist of servers used by spammers), as well as its Bayesian features for better spam identification and classification. I found it easy to do, and it took only 20 minutes. The immediate results over the past several days is very encouraging, although quite preliminary: Out of more than 100 total spam messages received, all but five were properly identified as spam, and I had no false positives. That's a far cry from the 10-25 spams previously left in my Inbox each day.
Enabling SpamAssassin's RBL checks resulted in spam originating from known open relays (i.e., mail servers that allow spammers to send mail through them) receiving a substantially higher total score -- for example, 8.7 instead of 2.7. As mentioned above, anything scoring 5.0 and higher gets filtered into my Spam folder via a simple rule in my e-mail program. [Please Note: The corresponding risk with using RBL checks is that legitimate e-mail coming from blacklisted servers may be improperly flagged as spam because of this trait.]
So now you know the "Why" and my preliminary results. Here is the "How" for making desired changes, and it's not difficult:
At Lunarpages.com, I have two easy ways of changing my SpamAssassin user settings. The first is by using their web-based Control Panel, under Mail, then under SpamAssassin. The other was adding the desired changes to the text-based "user_prefs" file via an FTP upload to my server. The Catch: Either method requires one to understand the settings, syntax, and the best way to select them.
That's where the SpamAssassin Configuration Generator site came in most handily. My web server is running SpamAssassin version 2.63, and the SA Config Generator site works with versions 2.5x and above. As the site states, "This tool is designed to make it easier to customize an installation of SpamAssassin with some common options. After you answer the questions below, a SpamAssassin configuration file matching your choices will be displayed, and you can download it and use it with your SpamAssassin installation." The best part is that it not only lists some of the most useful SA features and their options, but actually explains what each setting does.
I entered my choices into the web form, and it generated the following SpamAssassin setting file for me:
# SpamAssassin config file for version 2.5x
# generated by http://www.yrex.com/spam/spamconfig.php (version 1.01)# How many hits before a message is considered spam.
required_hits 5.0# Whether to change the subject of suspected spam
rewrite_subject 0# Text to prepend to subject if rewrite_subject is used
subject_tag *****SPAM*****# Encapsulate spam in an attachment
report_safe 1# Use terse version of the spam report
use_terse_report 0# Enable the Bayes system
use_bayes 1# Enable Bayes auto-learning
auto_learn 1# Enable or disable network checks
skip_rbl_checks 0
use_razor2 1
use_dcc 1
use_pyzor 1# Mail using languages used in these country codes will not be marked
# as being possibly spam in a foreign language.
# - english
ok_languages en# Mail using locales used in these country codes will not be marked
# as being possibly spam in a foreign language.
ok_locales en
The big changes above were the "skip_rbl_checks 0" to enable RBL checking (don't you just love double negative syntaxes?), and the two Bayes settings.
After that, I downloaded the original default "user_prefs" file from my web server via FTP so I could edit it. Windows Notepad, while primitive, is more than sufficient for the quick copy/paste task. If you want a more full-featured text editor, then I strongly recommend TextPad. I retained all the original text for future reference (commented out by preceding "#" characters), pasted the above text into the bottom of the file, and saved it. It was then uploaded via FTP to replace the original.
To double-check the settings actually changed, I went into the web-based SpamAssassin Control Panel, and sure enough, all of the new settings were displayed. Alternatively, I could have manually entered the above settings into LunarPages' web-based Control Panel and skipped the FTP file transfer. If you are running some type of SpamAssassin plugin program locally on your PC instead of a web server, odds are that the text-based settings file is stored on your local hard drive.
Lastly, I expect everyone's mileage will vary, as we all have a different mix of e-mail messages. I also plan to monitor the true effectiveness of these setting changes over a longer period. However, it was quite empowering to be able to combat spam on my own terms and see immediate results. While somewhat cryptic at first, the SpamAssassin software was fairly easy to tweak with a little self-help. Perhaps best of all, I didn't have to go purchase one of the many commercial anti-spam packages or services, as it was already included in my low monthly web host fee.
I prefer using SpamAssassin because frankly, I've never liked the various "whitelist" spam services. Why should I make friends and business colleagues jump through confirmation hoops when the problem is on my end? Not exactly my idea of customer service. Likewise, there will always be some people who won't perform the confirmation process, so their e-mail would otherwise be blocked from me. So I prefer to let spam through as long as it's flagged and managed appropriately. I'm also dramatically increasing the odds that I will see the important messages that were previously buried amongst the flotsam.
As a parting tip, if you're looking for a good free FTP program without included adware, then I heartily recommend LeechFTP, which has many features and has worked extremely well for me.
February 10, 2004
More on Microsoft Metadata
Back on January 6th, I reported the release of Microsoft's "Remove Hidden Data add-in for Office 2003 and Office XP".
With Microsoft's track record, I was somewhat skeptical that such a free utility would live up to its hype. With that in mind, I cautioned:
"I mentioned the readme file so that savvy users could compare its functionality to other metadata removers on the market. Although it's free, I strongly suggest that you make sure this tool removes everything you need it to remove. If it doesn't, then I recommend obtaining a program that will do the necessary job rather than rely upon this free utility. Otherwise, it could create a false sense of security, which when relied upon can cause many of the same problems as not using a metadata remover at all. Still, if you do not currently have a metadata remover and use the Office XP or Office 2003 suites, then using this add-in is probably better than the alternative."
Microsoft recently posted "Known issues with the Remove Hidden Data add-in for Office 2003 and Office XP". Also, Microsoft's Knowledge Base Article 834427 provides more information on the types of data this add-in can remove.
Therefore, it's up to each person to decide whether or not this tool properly suits their needs, and how it stacks up against leading programs such as Payne Consulting Group's Metadata Assistant for Word, Excel and PowerPoint. If the Microsoft tool removes what you need it to remove, then it may be worth using. The problem is that many people are just not tech savvy enough to know how to determine this -- thus my caution about false reliance on a metadata remover. My best advice is that whenever you can achieve it, as a general rule, Word document files do not contain revision and other metadata after conversion to HTML and PDF files. If you must share or send MS Office files, then make sure it is properly cleansed before sending. As part of one's due diligence in this regard, I believe a bit of in-house testing is required. If you don't know how to do this, then I heartily recommend engaging someone who does, such as Donna Payne.
As a good example of why we need to understand and care about metadata is this intriguing article by Preston Gralla. Mr. Gralla, a noted technology author, outlines how savvy privacy experts were able to debunk a supposedly valid high-level U.K. intelligence dossier about Iraq to be little more than a "cut-and-paste job" from three publicly available articles, one of which had been written by a postgraduate student in the U.S. I've also read similar approaches being used on college research papers and even attorneys' briefs to see who really wrote them and how much editing time was involved (cut-and-pastes take much less time than actual drafting) compared against the time billed.
[Thanks to Tom Mighell of inter alia and Sabrina Pacifici of beSpacific for some of the links.]
Posted by Jeff Beard | Permalink | Comments (0)
January 27, 2004
MyDoom Spreads Gloom
In case you've been bombarded by strange e-mails over the past two days and don't know why, there's a new bad boy in town named MyDoom, with AKAs of Novarg and Mimail.R by the various antivirus providers. Right now, experts are saying this could be the next big one. Among other things, it's been reported to do the following:
- Travels as an e-mail attachment, and by social engineering it entices recipients to open the attachment which infects PCs. (Never underestimate social engineering -- it's one of the reasons blogs are so popular in search engine results.)
- Sends out 100 infected e-mail messages in 30 seconds to e-mail addresses stored in the computer's address book and other documents. (Interestingly, it specifically avoids distribution to certain domain names and e-mail accounts -- presumably so these organizations and accounts are not infected.)
- Copies itself to the Kazaa download directory on PCs if Kazaa is installed. The offending file is one of seven file names: Winamp5, icq2004-final, Activation_Crack, Strip-gril-2.0bdcom_patches, RootkitXP, Officecrack and Nuke2004, with a file extension of .PIF, .SCR, .BAT, or .EXE.
- Performs a Denial of Service (DoS) starting on February 1, 2004, and has a trigger date to stop spreading on February 12, 2004.
- Opens up a backdoor so that hackers can download and execute files later (some speculate that this may be for launching other DoS attacks).
- Affects computers running Windows 95, 98, ME, NT, 2000 and XP.
- Per Wired News, there were conflicting reports as to whether or not it includes a key-logging program. Although the key-logging discovery was attributed to Symantec, it doesn't appear to have the keylogger component mentioned on their Novarg security response page.
This worm looks to be more of a social protest, which probably explains MyDoom's partially selective nature. According to CNet News, MyDoom is programmed to instruct infected PCs to launch a Denial of Service (DoS) attack against the SCO Group's web server between Feb. 1 and Feb. 12. Per CNET, "[t]he SCO Group has incurred the wrath of the Linux community for its claims that important pieces of the open-source operating system are covered by SCO's Unix copyrights. IBM, Novell and other Linux backers strongly dispute the claims."
My best advice regarding e-mail attachments is this: Even if you recognize the sender of the e-mail, never click on any e-mail attachment that is an executable (e.g., ending .PIF, .SCR, .BAT, or .EXE.). It also helps if you have Windows configured to NOT hide file extensions, so you can see files' true extension names. This worm spreads if one opens the attachment. As Nancy Reagan once put it: "Just Say No" to strange attachments. However, if you absolutely must open them, make sure your antivirus definitions are completely updated, and always scan suspect attachments prior to opening them (don't rely upon your antivirus program to catch it on the fly).
For more information:
"Tricky E-Mail Worm Spreads Fast", Wired News, Jan. 26, 2004
"Gloomy Forecast for MyDoom Fallout", CNet News, Jan. 27, 2004
Symantec Security Response for W32.Novarg.A@mm
January 18, 2004
CAN-SPAM Act -- Can't
Wired News reports that despite the enactment of the CAN-SPAM Act of 2003, "providers of spam-filtering software say they're blocking more messages than ever. Spammers, they say, are either ignoring the law or pretending to comply with guidelines for legitimate e-mail marketing."
Here's why I believe it's going to get a lot worse before it gets better, and offer a few tips that may help.
Particularly troublesome is that spammers have "created programs that rapidly morph the content of messages, so that only three or four identical e-mails are sent out at a time. With the advent of Can-Spam, Jacob said spammers are also increasingly guilty of "faux compliance," exploiting a caveat in the law that permits unsolicited e-mails from legitimate marketers who allow recipients to opt out of future mailings. Unscrupulous junk mailers are pretending to go along with the guidelines by including false return addresses for opting out." Thus recipients who attempt to opt out either have their requests ignored or are validating their e-mail addresses for the spammers.
Ed English, CEO of Intermute (which offers SpamSubtract), confirms my original comments when he states that "many spammers will likely evade the law by moving offshore" since spam is a global problem and the U.S. law has limited reach.
Interestingly, some Wired interviewees believe that spam will continue to increase until the FTC makes an example of someone. Unfortunately, given the recent developments in music and file trading, even though the RIAA made numerous loud examples of prosecuting offenders, Wired reports mixed results in its recent "Study: Music Piracy Rising".
Indeed, the Wired spam article suggests the CAN-SPAM act may turn out to be a green light for "U.S. businesses to begin spamming American e-mail addresses as long as they give users a way to opt out. If this happened, the group predicted, 'opting out of spammers' lists will very likely become the main daytime activity for most U.S. e-mail users in 2004.'" Thus in the interim, expect more, and not less spam. I've said it before: Although the federal government was trying to do something about it, this Act was the "feel good legislation of the year", as it will not likely be effective in any meaningful way.
In my humble opinion, the Law of Unintended Consequences comes into play here. Separately the CAN-SPAM Act and the FCC "Do No Call Registry" are intended to combat unwanted and voluminous communications. However, as I've mentioned previously, a large side effect of the national "Do Not Call Registry" and separate state "do not call" laws is that they are driving the blocked telemarketers over to spamming techniques to make up for the lost call opportunities.
Here's a parting tip if you're interested in opting out from receiving more from a spammer: Don't just click blindly on the "unsubscribe" link -- its displayed text can fool you. That's because HMTL formatting in e-mails and web pages allows the displayed text to be different than the underlying link.
Instead, there's a better way to check before clicking through. It's not foolproof, but it's sometimes helpful. Depending on your e-mail program or web client, you can oftentimes right-click on the opt-out link and copy it to the clipboard. Then paste it into a text-only field (say, in Notepad or your web browser's address field). If the e-mail address looks legitimate, you have a chance it may work as desired. Conversely, there are many experts who advise against any opt-out attempts, so use your best judgment.
If the link doesn't look legitimate (e.g., it doesn't contain a valid domain name, or it goes back to a free e-mail service like Yahoo or Hotmail), then by clicking through you're just begging for more spam. Also, it depends on the sender and the relationship you do or don't have with them. If it's from a reputable company with whom you've done business, I've often had good luck unsubscribing from their newsletters, sales and PR announcements etc. (I consider it spam when I receive such things from a company when I did not specifically request them). Most mainstream companies don't want to risk offending and alienating their customers into boycotting them.
In conclusion, while I would prefer to say that it's going to be spam as usual, I fully expect it's going to get worse before it gets better, if ever.
January 06, 2004
Risk Management of Wireless Networks
Slashdot has an interesting thread on this one, and particularly a link to the OCC's (Office of the Comptroller of the Currency, for banks) advisory on the topic. While the advisory lists a number of technical and tactical items to address, it also covers strategic concerns and lists many items that a wireless network security policy should consider.
If the idea of a bank using a wireless network concerns you regarding your financial privacy and security, then definitely check out the sub-thread on doctor's offices, which eerily could apply to lawyers.
Posted by Jeff Beard | Permalink | Comments (0)
New MS Office 2003/XP Add-in to Remove Hidden Data
Microsoft just published a free tool to remove hidden data (metadata) from the following Office applications:
- Microsoft Office Word 2003
- Microsoft Office Excel 2003
- Microsoft Office PowerPoint 2003
- Microsoft Word 2002
- Microsoft Excel 2002
- Microsoft PowerPoint 2002
Microsoft's overview states: "With this add-in you can permanently remove hidden and collaboration data, such as change tracking and comments, from Word 2003/XP, Excel 2003/XP, and PowerPoint 2003/XP files." There is a "readme" file included in its installation which provides a complete list of all of the types of data that the tool will help to remove.
Per MS, "you can run the Remove Hidden Data add-in on individual files from within your Office XP or Office 2003 application. Or, you can run Remove Hidden Data on multiple files at once from the command line."
Here's the big catch (you knew there had to be one): Currently, the only supported operating system for this add-in is Windows XP. Microsoft states that "[t]he Remove Hidden Data add-in has not been tested on Microsoft Windows 2000. Also, the add-in cannot be installed on Windows 98 or Windows Millennium Edition." While I'll resist the temptation to mention this appears to be yet another MS ploy to drive Win XP upgrades, I have to admit the thought crossed my mind. It could also be that MS wanted to release it as soon as they had a Win XP-ready add-in. Here's hoping they will support other Windows versions (but I'm also not holding my breath on this one).
Apparently this add-in is free to licensed users of these programs. Please note this is not a separate standalone program, so you must have the necessary Office program installed in Windows XP for the add-in to work. Microsoft's web page above also lists a number of helpful tips, such as saving to a new file so as to preserve any wanted items (e.g., Track Changes) in the original collaborated files.
I mentioned the readme file so that savvy users could compare its functionality to other metadata removers on the market. Although it's free, I strongly suggest that you make sure this tool removes everything you need it to remove. If it doesn't, then I recommend obtaining a program that will do the necessary job rather than rely upon this free utility. Otherwise, it could create a false sense of security, which when relied upon can cause many of the same problems as not using a metadata remover at all. Still, if you do not currently have a metadata remover and use the Office XP or Office 2003 suites, then using this add-in is probably better than the alternative.
On another note, while speaking at a recent legal technology conference, I was glad I attended a presentation from Donna Payne of Payne Consulting. She emphasized that metadata issues and improved metadata control is at least one compelling reason to upgrade to either Office XP or 2003 from prior versions. Of course, she then "scared us straight" by demonstrating metadata issues about which MS was unaware until she showed them. Yikes.
Posted by Jeff Beard | Permalink | Comments (3)
December 11, 2003
Blackberries to support Wi-Fi in 2004
CNET News reports that RIM "has been testing built-in Wi-Fi connectivity in its BlackBerry devices, the company confirmed Monday. The capability should be available sometime after spring of 2004."
This portion summed up the "whys" and trade-offs between cellular and Wi-Fi data access:
"Blackberry devices wirelessly send and receive data and voice calls over wide-area cellular networks. Supporting wireless transmissions over Wi-Fi would echo recent interest in the communications and networking worlds to combine cellular and Wi-Fi technologies. Data and voice can be exchanged more cheaply over Wi-Fi networks than cellular networks. Wi-Fi networks also allow for higher throughput speeds but have a shorter range than cellular networks."
Between RIM and its third-party developers, I've seen a huge push in the past several months to compete head-on with Palms and Pocket PCs in terms of richer features. It also doesn't hurt that Blackberries are Java-based (J2ME), which opens the doors to more developers and partnering opportunities. I'll still take a Palm-based PDA any day for sheer versatility, but professionals who primarily need a mobile e-mail solution with some fringe PDA features are still well-served by a Blackberry.
It will be interesting to see how RIM incorporates Wi-Fi security features, if any. On one hand, they have to make it drop-dead easy for their customers to hop on any accessible Wi-Fi network. On the other, there could be many sensitive e-mails, contacts, and documents being transmitted over Wi-Fi. I'm still very cognizant of this disturbing and publicized result from an end-user executive's lack of education regarding how these devices work -- and how it negatively impacted his former company, Morgan Stanley.
Without the necessary encryption, I could easily see someone camping out in a highly-traveled Wi-Fi cloud (think major airports and Starbucks in key locations) with some packet sniffing tools to pick up useful intelligence. A war-driver could park in front of a cyber café and broadcast his/her own Wi-Fi network with a stronger signal to drown out the legitimate network and have the patrons send all of their data through the rogue network instead. Scary, isn't it? This isn't a jab at the new Blackberry Wi-Fi feature, but at any mobile Wi-Fi device that doesn't have sufficient security features enabled by default.
Regarding cell phone convergence, I can't see many people using Blackberries as their primary cell phone. In the e-mail/PDA/cell phone combo arena, I still say the PalmOne Treo 600 is king. While I haven't researched it, I wouldn't be surprised if there was a Wi-Fi SD card under consideration for it. Although with the GSM/GPRS Treo version, the bandwidth speed should be pretty decent, but it still can't hold a candle to broadband over Wi-Fi.
Expect to see lower-power 802.11b chips released for mobile devices like PDAs and combo devices, since right now Wi-Fi chipsets put a substantial load on the battery, resulting in shorter use between charging. That's why we're initially seeing more Bluetooth-enabled small devices, which is much easier on battery life. However, that erroneously implies that Bluetooth and Wi-Fi are comparable. Bluetooth is better seen as a short-range hard-wired cable replacement, whereas Wi-Fi is better seen as a more robust wireless networking solution. In any event, we're going to see more devices capable of transmitting information over multiple types of wireless networks, particularly cellular and Wi-Fi.
Posted by Jeff Beard | Permalink | Comments (0)
December 02, 2003
Wi-Fi Hacker Arrest Raises Security & Liability Concerns
Per a recent CNET News story, an unusual arrest of a war-driver in Toronto is raising a lot of Wi-Fi security and liability questions. As CNET sums it up, "Toronto police said they stopped a car last week for a traffic infraction when they found the driver naked from the waist down with a laptop computer on the front seat, playing a pornographic video that had apparently been streamed over a residential wireless hot spot. The driver was charged with possession, distribution and creation of child pornography, as well as theft of telecommunications--a first in Canada, according to local authorities."
Now imagine that it was your Wi-Fi connection he hijacked, except that the authorities didn't catch the war-driver, but instead tracked the downloads back to your network from your ISP's logs. Talk about some explaining to do.
Study after study shows that the vast majority (more than two-thirds per one study cited in the story) of consumer Wi-Fi networks do not have even basic wireless security features enabled. The article further discusses some of the liability concerns for the owners of Wi-Fi networks, particularly on negligence theories. As most Wi-Fi networking components ship with most or all security features disabled for "easy setup", and the default passwords are well known, it certainly doesn't help matters.
All of the above clearly illustrates the serious need for a comprehensive set of "Wireless Best Practices". Here's some links to get off to a good start:
- LawTech Guru's Wireless Networking "Best Practices"
- "Best Practices for Wireless Network Security", by Susan Kennedy, posted on ComputerWorld
(Link courtesy of Dennis Kennedy's Blog.) - ABA LPM Law Practice Today, November 2003 online issue devoted to Wireless Technology
(Alternatively, you can search its archives for "wireless".)
Naturally, there's much more information available on the web on this controversial topic. Some advocate the strict prohibition against Wi-Fi networks due to the valid security concerns. Others advocate its use by enabling as much security as possible, to make it "reasonably secure", which is subject to various interpretations.
There's no doubt that wireless networks are very convenient, but that needs to be balanced against the relevant risks. Each person or organization needs to make the call for themselves, but I'd rather see the decision made as an informed one -- hence the need for better Wi-Fi security education, best practices, and policies.
November 20, 2003
Wireless Networking "Best Practices"
[8.01.04: Click here for Version 2.0 of this article. I've updated this list to include many more security measures, tips, and explanations.]
While at the WI legal tech conference mentioned in my immediately prior post, one the best technical presentations I attended was "Cutting The Cord: Wireless Law Practice Is Here!" by Nerino Petro and David Whelan. Not only did they provide great written materials, but they took a very complex, jargony topic and made it understandable.
If any of you are considering using a wireless network (predominantly 802.11a/b/g Wi-Fi), in addition to the articles mentioned in my prior post this week, I've compiled a nice checklist of tasks you should always do when setting up and maintaining your wireless hardware and software. If you don't know how to do these, get someone in who does or as Dale Haag recently corresponded with me, any kid with a Pringles can will own your system. (For even more info, try a Google search for the following: pringles can wireless range).
To make your wireless network the most secure:
(Caveat: I make no guarantees or warranties that this is an all-inclusive list.)
- Change the default SSID (Service Set ID or network name) and encryption keys.
Hackers know all the default values for nearly each make and model, as they are posted all over the Web. If you really want to know, try another simple Google search for the following: default wireless SSID.
- Disable the SSID broadcast.
- Change the default password for the Administrator account.
Again, wireless hackers know these defaults, most of which are simply "Admin". Try a Google search for: default wireless router passwords.
- Enable MAC Address Filtering.
This filters MAC addresses at the access point to allow access to only authorized Ethernet cards. Every Ethernet network card, wired or wireless, has a unique number called a MAC address.
- In addition to MAC Address Filtering, limit the number of allowed connections to the bare minimum needed.
- Enable WEP (802.11b) or WPA (802.11g) 128-bit Encryption.
Please note that this will reduce your overall network performance. However, since Internet speeds via cable and DSL are usually much slower than the maximum Ethernet speeds, it should have no effect on Internet access speed, just on file and print sharing speeds.
- Limit folder/file sharing to the minimum with password protection.
Additional "Must Use" Safeguards:
- Personal or software firewalls, such as ZoneAlarm Pro and Norton Internet Security
- Good antivirus software
- Anti-spyware/malware programs, such as Ad-aware, Spybot Search & Destroy, and PestPatrol
Ongoing Maintenance for the Best Security:
- Keep the personal firewall and antivirus programs updated with the latest definitions.
- Keep up with the various security patches from Microsoft.
- Change the SSID value periodically.
- Change the WEP or WPA encryption keys periodically.
- I've heard some newer wireless access points (WAPs) have a feature for automatic rotation of one or more of these keys, which would definitely make it more challenging to hack. (For you Trekkies, this is akin to rotating the shield harmonics to repel the Borg. ;^)
Naturally, the more secure you make it, the less convenient the setup. But I'll take the extra wireless security anytime, because wireless networks are still horribly insecure compared to wired.
Posted by Jeff Beard | Permalink | Comments (0)
November 06, 2003
Are You Ready for Bluejacking?
It seems there's no end to the imagination of high-tech cell phone users. First there was cell phone camera "voyeurism", which prompted a number of organizations to ban or otherwise restrict them (think potential trade secret and other leaks). So much so that cell manufacturers are now being asked to sell special editions without the cameras to various organizations. But enough on the cameras.
"Bluejacking" is the latest craze. In essence, it's a way to surreptitiously send messages to strangers, from one Bluetooth-enabled cell phone to another. For example, your Bluetooth phone mysteriously receives a message, "You've been Bluejacked!" Gizmodo has a nice summary of the process. Ironically, it's actually done by sending a new contact record to another phone that's in "discoverable" mode, but it appears to the recipient as a message. That's because the sender types the message into the name field. At this point, it sounds like a harmless prank to watch people's puzzled reactions or perhaps a clever way to break the ice with an attractive stranger. But if you're like me, the idea of leaving one's device open to pranksters doesn't generate any warm fuzzies.
In the U.S., Bluetooth phones have not truly taken off yet, so most people don't have to worry for now. This is really quite similar conceptually to what happened with open Wi-Fi access points. Either people don't realize they can enable simple security or they don't want to because the lack of security makes it easier to connect devices on the fly -- which enables Bluejackers to have their bit of fun. At least the good news is that Bluetooth is a short-range radio technology, with a range of only 30 to 40 feet, but newer developments are extending its range. That's about the same range for cell phone cameras, and look at the mischief it's caused.
And in case you were wondering, yes, there are more than a few people who find this quite amusing and can't wait to try it -- it's the latest tech craze. Just check out the forum chat at Mobiledia.
My suggestion is that if you have a Bluetooth-enabled device (who said this is only limited to cell phones?), I'd recommend searching through its settings, or heaven forbid, read the manual to see whether there are any password features worth enabling. If necessary, one can disable the security if things aren't connecting when desired. With the possible exception of Bluetooth wireless headsets, I'll wager that most Bluetooth cell phone owners are not even using their Bluetooth connection most of the time. So it just makes sense to close the open hole.
Again, this seems like a bit of harmless fun at the moment, rather like the digital equivalent of "ding dong ditch" or prank phone calls. Although it's possible some miscreant could find more serious implications. Thus if you'd like to learn more about Bluejacking, head on over to BluejackQ, which further explains Bluejacking and freely offers the steps, tips, and tricks for the Bluejacker wannabe.
Posted by Jeff Beard | Permalink | Comments (0)
October 23, 2003
Antispam Bill Passes Senate Approval
CNET News reports the unanimous approval of the CAN-SPAM Act of 2003, S. 877 with 97-0 votes in the Senate, which leaves the House of Representatives to hammer out their differences. The CNET article gives the highlights and examples of how the bill applies to and criminalizes certain spamming techniques.
While I applaud the Senate's action, in all practicality this can only be marginally effective at best. My opinion is that this will probably be the "feel good legislation" of the year. The FCC Do Not Call Registry has a much better chance at curbing telemarketers than any antispam legislation will have on spam. The simple reason is that spam is much more of a global problem. Spammers are also much more adept at trickery and covering their tracks than telemarketers, simply because the internet technology is more advanced, and prone to abuse.
In addition, the FCC Do Not Call Registry and separate state "do not call" laws are driving the blocked telemarketers over to spamming techniques to make up for the lost call opportunities. Thus U.S.-based legislation alone cannot be effective globally. Now, a world treaty coupled with advanced spam origination discovery tools might make a larger bite, but still wouldn't be as effective as desired. The problem is that spammers are teaming up with hackers and together they will stay at least a step ahead of the game for the forseeable future.
Again, I heartily applaud the Senate's approval, but I'm not even cautiously optimistic about its ultimate effect at curbing spam. I certainly hope I'm mistaken in this, but in my humble opinion, self-help and anti-spam/prevention education is going to make more of an immediate impact on a particular person's or organization's spam situation. Only we can prevent spam, by what we do and don't do online and even offline, such as in answering telephone questions and filling out application forms with e-mail addresses.
IMSecure Pro: A Firewall for Instant Messaging
Yet another good review from the November issue of PC World Magazine, this time reviewing IMSecure Pro from ZoneLabs. Here's what the review doesn't explain, but should have:
Besides the clever name, IMSecure Pro (and its free basic sibling, IMSecure) sounds like the right product at the right time. More and more people have been tuning into Instant Messaging, but IT departments have rightfully been concerned when their users download and install the free and insecure consumer-level IM clients -- which is why a fair number of organizations have already banned IM. Likewise, even home and laptop use of these programs introduces the definite possibility of malware and other undesirables (such IM-borne scripts, buffer overflow attacks, and IM spam) being transmitted along IM channels.
In comparison to ZoneLabs' well-known ZoneAlarm firewall, IMSecure Pro is best described as a firewall for IM clients. It works with most IM programs, even the multi-network Trillian IM client, but there are a few exceptions per the review (apparently it doesn't work with ICQ or IRC).
What makes this different from a regular personal firewall like ZoneAlarm? A regular personal firewall lets you control web access by port number and program name, but it usually doesn't have the finer control over individual features within a program. Consider this: What is one of the first things you need to do after installing an Instant Messaging program on a PC with a personal or network firewall installed? That's right: If it's not already open, you need to open a hole in the firewall so your IM program can talk to all of your buddies' IM programs -- potentially a hole that a savvy hacker can drive a truck through.
That's where IMSecure comes in: IMSecure Pro allows you to block certain IM features, such as file transfers and voice and video chats. The program also supports encryption for messages sent between between different IM programs, as long as they communicate over the same service. Its "ID Lock" feature can also prevent the inadvertent release of private data over IM channels and exploits. What I like is that ZoneLabs included a similar lockout feature from ZoneAlarm, called "IM Lock" in IMSecure Pro, so that you can take ultimate control over instant messaging in case of IM misuse or extreme IM security.
Now I haven't had a chance to try IMSecure yet, and I've oversimplified this discussion to get the points across in relatively plain language. However, if you use one or more of the popular consumer-based (read: very insecure) IM programs, this sounds like a must-try program.
October 09, 2003
Another Critical IE Cumulative Patch Released
Microsoft has recently released yet another cumulative patch for Internet Explorer 5.01 and later. This one is classified as critical, and Microsoft Security Bulletin MS03-040 describes it in more detail. To save you some time, here's the actual download link.
To sum up the Microsoftese: With the latest vulnerability, an attacker could run programs on your computer when you are viewing a Web page. An attacker could also craft an HTML–based e-mail, so you could be attacked by spam with teeth.
When visiting an attacker's Web site, it could be possible for the web site to exploit this vulnerability without any other action by you, and particularly if ActiveX is fully enabled in IE. Please see my post yesterday -- this is precisely the reason why I recommended setting IE's ActiveX controls to "prompt" nearly two years ago. While the prompts are annoying, it shifts the control back to you as to what is or isn't installed via the web browser. The most prudent course of action is to install the latest IE patch and change its ActiveX settings to "prompt" if you haven't already.
Per Microsoft, this vulnerability affects all computers that have Internet Explorer installed. You do not have to be using Internet Explorer as your web browser to be affected by this issue.
Several related caveats:
- A prior IE cumulative patch disabled some of IE's HTML Help functions. Since the current patch includes all prior patches, this one will also disable the same functions. You can address this by downloading the necessary HTML Help patch via the MS Knowledge Base Article 811630.
- In addition, an attacker could use Windows Media Player's (WMP) ability to open URLs to construct an attack as described above. Therefore, MS recommends patching the Windows Media Player as well. This patch is available via the MS Knowledge Base Article 828026.
October 08, 2003
Practicing Safe Hex
To morph a phrase: Hey, don't put that in your computer! You don't know where it's been!
Jim Calloway, a good friend and Director of the Oklahoma Bar Association Management Assistance Program, authored "Computer Viruses to Spyware: Things You Don't Want to Pick up Online" in the October issue of Law Practice Today. This is a highly recommended read.
To Jim's savvy suggestions, I'll add my own, "Ten Steps to Online Privacy & Security".
I particularly liked these recent "Tips" articles, also on the recommended reading list:
- "Invasion of the Computer Snatchers" by Mark Tamminga,. Mark is the recent past chair of the ABA TECHSHOW®, and coauthor of The Lawyer's Guide to Extranets (ABA, 2003).
- Also, this gem about using public computers was passed along via Dennis Kennedy's blog.
Jim and Dennis are both serving on the TECHSHOW® Board this year, which as you can see, sums up the caliber of talent that puts this great conference together every year. (Full disclosure: I served on the TS planning board for 2002 and 2003, and am active in the ABA Law Practice Management section.)
From these gurus, perhaps the most important steps to highlight are:
1) Installing good defenses, keeping them updated and tested, and running scans frequently on your computer systems (firewall, antivirus, and pest-removers such as Spybot S&D, Ad-aware, PestPatrol, etc.). For example, test your firewall at Shields Up!
2) Patching your PC (operating system, browsers, office suite, e-mail programs, etc.).
3) Outsmart the spammers: In your e-mail program, turn off any preview pane features, disable java and javascript to thwart e-mail tapping, and don't open any suspected spam message. Even if it's "harmless" advertising, many spam messages contain web bugs that log your opening of the message and correlate it back to your e-mail so they can spam you again (and again and again and...).
4) Disable any automatic installation or launching features of your web browser (e.g., ActiveX) -- set them to prompt you instead.
5) Backup, Backup, Backup -- This is your first and last best defense against losing your valuable data and all the misery that accompanies it.
And the most important step:
6) Use your head: Many computer invaders get past all of these formidable defenses from the inside, using one powerful tool -- you. Jim's summary of the KRESV tests for identifying and avoiding spam on your own was very useful in this regard.
Posted by Jeff Beard | Permalink | Comments (0)
September 28, 2003
Better Check Your Zipper
While thumbing through the Sept. 2003 issue of PCWorld, I saw an update on the WinZip / PKZip encryption incompatibility problem. In essence there's been no progress, so it was mainly a caution: For now, if you're using the newest version of either program and sharing Zipped files with others, you'll probably want to send them as unencrypted, standard .ZIP files. Read on for more details.
In a nutshell, PKWare, original makers of PKZip for DOS and Windows, introduced new encryption technology earlier this year. However, according to the press, they chose not to post or share the specs with their main competitor, WinZip. Naturally WinZip Computing felt they had to offer better encryption, as normal password-protected Zip files have been easy to crack for some time. So WinZip introduced a different encryption method, and thus the newest versions of PKZip and WinZip generate incompatible encrypted .ZIP files.
This brainy move between the two developers blows the one thing the Zip format really had going for it -- full compatibility. Also, a new WinZip 9.0 beta feature allows the new Zip format to hold more than 65,535 files and be larger than 4GB, which wasn't possible nor is compatible with older versions of either program.
To confuse things even further, both Zipping programs use the same .ZIP file extension for the standard (unencrypted) and encrypted Zip files . Many have suggested they simply implement a second file extension for encrypted Zip files -- to make it much easier for users to differentiate between the two when they download or receive them via e-mail attachments. But, no dice -- it appears they want to keep slugging it out between themselves at their customers' expense. (Uh guys, really bad plan...)
Ever since WinZip beat PKZip to the Windows platform years ago, they've been the clear leader in market share. My money is on WinZip, especially since they released their encryption specification back on May 12th. This is key so that others making Zip-compatible software can incorporate it into their own programming. Since PKWare has been less forthcoming, many question its intentions for keeping Zip an open standard. This move also makes it doubtful their new format will become the new Zip standard or will even be used by others. (That "bad plan" thing keeps coming up, doesn't it?)
The good news is that they both continue to generate the standard compatible .ZIP file if the new encryption is not used, and you don't create larger Zip files than what was supported previously. So unless you know for sure which Zipping program and version your recipient is using, you're best off not using any new encryption or compression feature, unless it's for yourself. No sense in sending a client a file they can't use. If you're regularly receiving Zip files from clients or vendors, you may just want to send them a quick e-mail asking them to use the standard "classic" features, for lack of a better term.
As it's the current issue, the Sept. PCWorld article isn't yet posted online. However, earlier similar articles can be found online at both c|net News.com and PCWorld.com.
September 24, 2003
eBay Privacy: The Latest Oxymoron
Think the RIAA is being aggressive in serving DMCA-sanctioned subpoenas upon ISPs without prior court approval (not to mention the individual lawuits)? According to this disturbing article, eBay could have them beat by comparison. In essence, eBay officials freely distribute their member's private information to any law enforcement agency who requests it -- without requiring any subpoena in many cases.
If this account is accurate, then Joseph Sullivan, eBay's director of "law enforcement and compliance", told numerous law enforcment officials in a closed session that "There's no need for a court order," and further stated:
"We don't make you show a subpoena, except in exceptional cases," Sullivan told his listeners. "When someone uses our site and clicks on the `I Agree' button, it is as if he agrees to let us submit all of his data to the legal authorities. Which means that if you are a law-enforcement officer, all you have to do is send us a fax with a request for information, and ask about the person behind the seller's identity number, and we will provide you with his name, address, sales history and other details - all without having to produce a court order. We want law enforcement people to spend time on our site."
The article goes on to state:
The meaning is clear. One fax to eBay from a lawman - police investigator, NSA, FBI or CIA employee, National Park ranger - and eBay sends back the user's full name, email address, home address, mailing address, home telephone number, name of company where seller is employed and user nickname. What's more, eBay will send the history of items he has browsed, feedbacks received, bids he has made, prices he has paid, and even messages sent in the site's various discussion groups.
Have we really agreed to this? On this point, the article states:
A brief visit to the company's Web site reveals that the "user contract" that visitors are supposed to read before agreeing to the conditions is 4,023 words long. One paragraph makes reference to the site's "privacy policy." The user has to click on a link and is diverted to another document that is some 3,750 words long. It then takes another 2,390 words to reach the section about which Sullivan told the legal authorities: The user's privacy is solely up to eBay.
It gets even better when you factor in PayPal's information, as eBay acquired them in July 2002:
PayPal has about 20 million customers, which means that we have 20 millions files on its users," Sullivan proudly relates. "If you contact me, I will hook you up with the Paypal people. They will help you get the information you're looking for," he tells his listeners. "In order to give you details about credit card transactions, I have to see a court order. I suggest that you get one, if that's what you're looking for." It isn't certain that visitors to the site are aware of the thick hints eBay gives the lawmen."By buying PayPal, eBay is merging the information about the goods trail with the money trail," explains Kozlovski. "Thus, in spite of the protective mechanisms of the law against disclosure of details on transactions, eBay is in a position to analyze the full set of data and `advise' investigators when it might be `worthwhile' for them to ask for a subpoena to disclose the details of a financial transaction. Essentially, this bypasses the rules on non-disclosure of details of financial transactions and the confidentiality of the banker-client relationship."
It's a small comfort knowing they have to get a court order somewhere along the way -- my, what an inconvenience that must be. When I set up a PayPal account earlier this year, on several occasions their service strongly encouraged me to "verify" my account by providing my financial institution's account information. In fact, they place certain limits on your PayPal account until you do so. Somehow, I just didn't think it a bright idea to hook up my checking or savings account in this manner, so I declined. In hindsight, I'm pleased with that decision.
However, they're free to require this to continue using PayPal (arguably the number #1 payment option on eBay-hosted auctions) and my only two choices will be to a) provide it begrudgingly and hope blindly that my funds stay secure (not a prudent thing to do), or b) lose my PayPal account "privileges", which will necessarily foreclose me from participating in any eBay auction or transaction where the seller only accepts PayPal as the method of payment. Then I can't use it to collect payment as a seller either. And I'm a normal, law-abiding guy who just wants to find a good deal or buy something that's hard to find elsewhere (again, legally).
This is not the first time these issues have been raised with eBay. They've been criticized by PCWorld and most notably JunkBusters in its April 2003 letter to the FTC describing why they believe eBay's privacy policies and summaries (and the gap between them) constitute unfair or deceptive trade practices.
So that I'm not misunderstood here: eBay has its share of scammers, con artists and gray/black market sellers, and they need to be stopped for the protection of its legitimate buyers and sellers. This, by itself, is a worthy goal. On one hand, it's comforting to know that eBay is being "policed", because eBayers benefit from that (as does eBay, the credit card companies, etc.)
However, the wealth of information tracked, collated, analyzed, and distributed under eBay's control is more than a bit concerning. Remember all the hullabaloo years ago when many fought against having their personal video rentals disclosed? And somewhat more recently, all the hype surrounding DoubleClick's data collection practices? For frequent eBay participants, that could be chump change by comparison.
Yes, eBayers have a choice in using the service, but I don't think that is a fair thing on which to hang one's hat. In my humble opinion, I truly believe there needs to be a better balance between fighting crime and opening our private lives to the State just because we're trying to find a good deal online. It's one thing for my local supermarket to track my local purchases via my "saver card". It's another when they start sharing it with others. (By the way, what do they do with all that information anyway?) I'm reminded of the old standby: "If you haven't done anything wrong, you have nothing to worry about." Why doesn't that console me in this electronic age?
I'll stress that this is my personal opinion: I don't think it's even close to "fair" to expect the average lay person to read several thousand words of legal gobbledygook when all they're trying to do is get a good deal on a used CD, PDA, or what-have-you. And I'm seeing a pattern here where organizations' "summaries" of their policies can be quite misleading. A recent case in point is the ongoing discussion about the Creative Commons warranty provisions, which do not appear in their policy "summaries" (you have to read the fine print to find them).
Granted, the latter has to do with copyright licensing and not privacy. But again, this is a real problem for the average person to understand in a meaningful way. We need some "Truth in Labeling" standards. Hey, wasn't that what TRUSTe and similar organizations were supposed to address? Hmmm... Yes, the criminals need to be caught and brought to justice, and we benefit from those efforts. It sounds like the PATRIOT Act debate all over again. However, in this context, it just seems a bit too "over the top" for my taste -- especially eBay's Sullivan's imputed enthusiasm to give away our information.
As the recent onslaught of RIAA lawsuits illustrates, it's just too easy to catch the dolphins along with the tuna in their nets. In this electronic age, Orwell's head would have been mimicking my new hard drive -- spinning around at 7,200 rpm.
September 19, 2003
What's in Your PDA? PDA Survey Sends Wake-Up Call
Pointsec Mobile Technologies conducted the "PDA Usage Survey 2003" and compiled a list of 20 facts discovered from the survey results.
From a security and identity theft perspective, this is scary. I, for one, do not keep any sensitive financial account information on my PDA for this reason. I do use a password, but admit that I don't lock my PDA with it as much as I should, for convenience sake. I have tried numerous Palm programs that are supposed to lock your PDA after "x" minutes of inactivity, but they universally caused so many fatal errors and soft resets that it was counterproductive. There's still a few more I want to try, but I'm not hopeful -- my PDA is just too "tricked out" with a lot of different apps and hacks running on it. The security programs just don't play nice with the rest.
I am, however, extremely diligent about my devices in public places. For example, whenever I get up from a restaurant seat or exit a taxi, I always do a quick pat check, just to make sure the PDA and cell are still there. If this is obsessive-compulsive, so be it. These are indeed the top ways people lose their mobile devices -- the little devils just slip out of your pocket when you're not looking. (I think Dockers was onto something with their Mobile Pants, but the external zippers just looked too geeky.)
The lack of PDA passwords is not surprising at all. What is: storing sensitive financial information or key passwords without password protection. That's just plain crazy, especially since the survey reported that 25% lost their PDA's at some point. That's one out of every four PDA owners. But again, the masses prefer convenience to security at this level -- we're just in too much of a rush these days.
I previously stored online passwords on my PDA in a database using 160-bit Blowfish encryption, which is pretty strong. However, after several months, the database was irretrievably corrupted, and I decided that it was just smarter to keep them in my head. I probably have over 50 passwords, since I rarely recycle them between sources. That way, if someone discovers one of them, it doesn't compromise the rest. When it comes to passwords, compartmentalization is a good thing, as long as you can keep them straight.
So I'm good until Alzheimer's hits, and hopefully that's a long way off. At least I've made sure the Mrs. knows the important ones too. I've also considered encrypting them on my home PC, but that still bothers me -- that someone could somehow access them. If I'm somehow mentally disabled or dead, I just don't think looking up passwords is going to be my #1 problem.
I've recently posted a very compelling example detailing why storing sensitive information on a PDA or other mobile device, without proper security, can really come back to bite you. Let's be careful out there.
Posted by Jeff Beard | Permalink | Comments (0)
September 16, 2003
Smart Identity Theft Countermeasures
There's been an e-mail going 'round the Net for some time purporting to be from a corporate attorney who experienced the horrors of identity theft.
If you haven't read it yet, you should. Even if you have, it's a good reminder. To help prevent identity theft, s/he lists a number of smart things to do in advance as well as common traps to avoid. There's also good advice on immediate steps to take after losing a wallet or purse, to protect yourself as much as possible.
Yes, I suppose this classifies as spam as I came across it in my inbox. However, the tips just make good sense and so I decided to track down a cleanly-formatted copy on the web to share. Just goes to show that not all spam is bad (just 99.9999999999%). It's easy to think, "this happens to other people", until it strikes too close to home. You may want to verify the credit bureau numbers, just to be safe.
Also, Sabrina Pacifici has a great cumulative list of posts on ID Theft topics at her blawg, beSpacific.
September 12, 2003
What's in your e-Wallet?
I was reading this quick metric on CIO.com on the rapid climb of Identity Theft complaints filed with the FTC clearinghouse.
Then I recalled my recent experience. I discovered some personal information in one of my legal directory listings and had it removed ASAP. I don't want to go into too much detail here, as I don't want to create a roadmap for identity thieves. Suffice it to say, it was detailed enough to cause me concern. I called the publisher, who confirmed they had been receiving many calls from attorneys requesting the same.
I simply just hadn't looked at my listing in ages, and that info was added at least 5 years ago, when I joined my firm, and before Identity Theft was as rampant as it is now. It was a standard field on the profile form, and I dutifully filled it out at the time. Well, times have changed.
While I had it removed, there are many more listings with such information, which should be a concern to those individuals. Hopefully, this will raise some awareness within the legal community. Of course, this is only one of many sources of information. Sites like Anybirthday.com have been around for quite some time (although you should remove that data as well), and that's just the tip of a very large iceberg.
But at least I can help my little corner of it.
September 08, 2003
Juicy Blackberry Information Leaves a Stain
It's truly amazing what one can buy for under $20 on eBay these days:
Wired News details a cautionary tale for firms with confidential information stored on their employees' and principals' mobile devices: BlackBerry Reveals Bank's Secrets.
For a mere $15.50, a Seattle computer consultant picked up a Blackberry on eBay that contained high-level e-mails, names, addresses, phone numbers and transactions relating to Morgan Stanley, their clients and executives worldwide, and even the seller's personal financial information. The seller was a former VP of M&A at Morgan Stanley.
The VP's e-mail account was closed, but much of the data still resided on the device. He simply had no idea that data could remain on a device long after he removed the battery. (Apparently this guy never heard of flash memory.)
It's 10:00, do you know where your Blackberry is? Or PDA, cell phone, laptop, tablet PC, etc., for that matter. This is the perfect "poster child" situation for why mobile security solutions and procedures are a good thing to have -- and more importantly, follow.
Posted by Jeff Beard | Permalink | Comments (0)