November 29, 2008
Wireless WPA Encryption Component Hacked -- How to Protect Yourself
Beware, security researchers have discovered a way to do a partial hack of some wireless networks using WPA (Wi-Fi Protected Access). WPA is used by many to encrypt and secure their wireless networks. I first read about this announcement a few weeks ago, and preferred to wait until after the findings were published for confirmation. ARS Technica has an excellent and balanced article, "Battered, But Not Broken: Understanding the WPA Crack", describing the hack, and the researchers published their paper online.
There's a lot of FUD (Fear, Uncertainty & Doubt) floating around on this, so I decided to add my perspective and tips for legal professionals. The sky isn't falling. It's important to understand that WPA itself hasn't been cracked, just one of the algorithms used with it, known as TKIP (Temporal Key Integrity Protocol). If you're using AES (Advanced Encryption Standard) encryption with WPA, you're still safe. If you're still using WPA with TKIP, you just need to make a simple change in your wireless router and any wireless device that connects to it, such as your laptop. I've posted an example below on how to change the settings in a Linksys router.
Basically, if you have your wireless router configured to use WPA with TKIP, your wireless network is now vulnerable over that connection. One of the researchers, Erik Tews, stated that for routers using WPA with TKIP, he can access and manipulate the network traffic being sent from your wireless router. While they're not yet able to break the TKIP keys, it's still serious. Supposedly, the traffic sent from your PC back to the router is still safe, but now it's probably only a matter of time before that gets compromised as well.
What Should You Do?
I'll try to keep the jargon to a minimum, but need to mention a few acronyms throughout because that's what you'll see in your router and laptop options. Keep these guidelines in mind:
- First, using any encrypted network is better than a non-encrypted network, even if it only stops the casual or amateur snoops in the area.
- Use a long and strong passphrase for your encryption key -- at least 20 characters with a mix of upper- and lower-case letters, numbers, and symbols.
- Keep in mind that cheap and home-made wireless antennas can access your wireless signal even a mile away.
- Never, ever use WEP (Wired Equivalent Privacy) if you have a better choice -- WEP has been cracked for years now and is considered very insecure.
- WPA (think of it as WPA1) and
- WPA2, which is more secure than WPA.

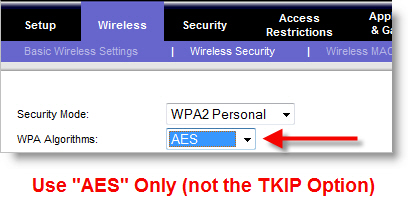
AES encryption is used by the U.S. government, as it's considered much more difficult to crack. If your wireless router doesn't support WPA2 (i.e., doesn't have it listed), then you probably need a firmware update from the manufacturer, which you can usually download from their web site. If your router is too old that it doesn't have WPA2 and there isn't a firmware upgrade for it, then it's probably time to buy a new router. I'd suggest buying one of the new "n" routers for better speed and coverage, as new laptops have been coming out with "n"-capable wireless cards for well over a year. While "g" routers are still very usable, 802.11n is the platform to use going forward if you need to upgrade.
Also, you may need to configure all of your wireless network devices (PC's, wireless printers, BlackBerries, etc.) to use WPA2 if available in their setup options. Windows Vista supports WPA2 out of the box, whereas you'll likely need a patch for Windows XP (see the end of this post for details). I've found my new HP wireless printer and BlackBerry Curve also both support WPA2. If you have some devices or PCs that cannot use WPA2, then you'll need to use WPA for all of them, including your wireless router.
Why Some Sources Reported WPA Was Hacked
It's a matter of semantics. In many wireless routers, WPA comes with two types of encryption algorithms, TKIP and AES. It's important to know that TKIP was only intended as an interim industry solution until they could come up with something better (AES encryption). I explained this back in 2004, when I published my "Wireless Networking Best Practices: Version 2.0" on this blog:
Due to the relative ease in which WEP (Wired Equivalent Privacy) is cracked, WPA (Wi-Fi Protected Access) is vastly preferred. For home use, most people will want to enable WPA Pre-shared Key (WPA-PSK) and use a long key name with a mix of upper and lower case letters, numbers, and odd characters (such as ~!@#$%^&*).That advice still holds true today, just with the added suggestion to use the newer WPA2 if available to provide more security, and practically, to buy you more time as less secure options continue to be hacked. Consider that it's taken a number of years for researchers to find a crack in WPA-TKIP's armor. Like WEP, don't use WPA with TKIP if you have a better option. Keep in mind that home users will likely want to select the WPA2 Personal (aka "WPA2-PSK" or "WPA2 Pre-shared Key") option, while enterprises will use simply "WPA2". The main difference is that the "Personal" or "Pre-shared Key" options require you to enter the passphrase (the pre-shared key) into each device that needs to connect to your wireless network.For the WPA Algorithm, at a minimum choose TKIP (Temporal Key Integrity Protocol). Better yet, use AES (Advanced Encryption Standard) if your router, Wi-Fi card, and software support it. TKIP is an interim industry solution, but it adds the ability to automatically generate new keys at preset intervals. (...) Again, AES is the stronger encryption method that the wireless networking industry is moving toward. If you have it, use it. (emphasis added)
Adding Some Perspective
Again, keep in mind the sky is not falling. While serious, this is a limited hack. It's far better to use some level of encryption than nothing, since the latter leaves your wireless network wide open. Use the most secure option available to you. If you do any work from home, I'm sure your employer will appreciate it as well.
Consider this from the ARS Technica article:
Don't hyperventilate yet; you're (mostly) safeWith all that said, if you have the option of using AES instead of TKIP, use AES. If nothing else, you'll sleep better knowing you're using the most secure encryption currently available.
Now let's back up a little. The early coverage of this crack indicated that TKIP keys were broken. They are not. "We only have a single keystream; we do not recover the keys used for encryption in generating the keystream," Tews said.To describe the attack succinctly, it's a method of decrypting and arbitrarily and successfully re-encrypting and re-injecting short packets on networks that have devices using TKIP. That's a very critical distinction; this is a serious attack, and the first real flaw in TKIP that's been found and exploited. But it's still a subset of a true key crack.
Tews pointed out that "if you used security features just for preventing other people from using your bandwidth, you are perfectly safe," which is the case for most home users. Someone can't use this attack to break into a home or corporate network, nor decipher all the data that passes.
[...]
So WPA isn't broken, it turns out, and TKIP remains mostly intact. But this exploit based on integrity and checksums should argue for a fast migration to AES-only WiFi networks for businesses who want to keep themselves secure against further research in this area-research already planned by Tews and Beck. And now that these two have opened the door, WPA will certainly become subject to even closer scrutiny by thousands of others interested in this space: black-, gray-, and white-hatted.
For those of you still running Windows XP: You might not see the option for WPA2 in your wireless client settings. A while back, Microsoft released a patch to add the WPA2 protocol to XP's wireless settings. Please note this patch is only for 32-bit versions of XP running SP2 (Service Pack 2). While I've successfully installed this patch on several PCs, I always recommend performing a full backup of your system using a drive imaging tool such as Norton Ghost. I also recommend creating a "restore point" in XP as a precaution before installing any patch. While this patch installed just fine for me, I take no responsibility for it or any resulting consequences as it is a Microsoft patch. I'm merely pointing you to it as a resource. Let's be safe out there.